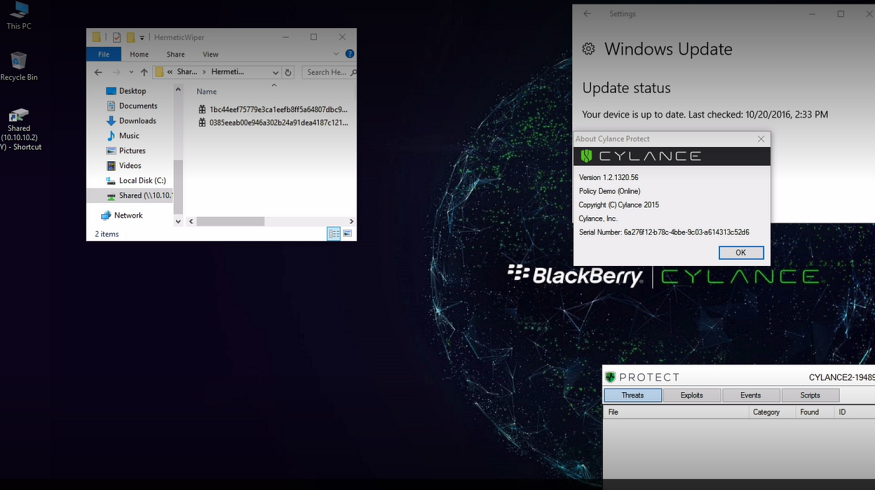
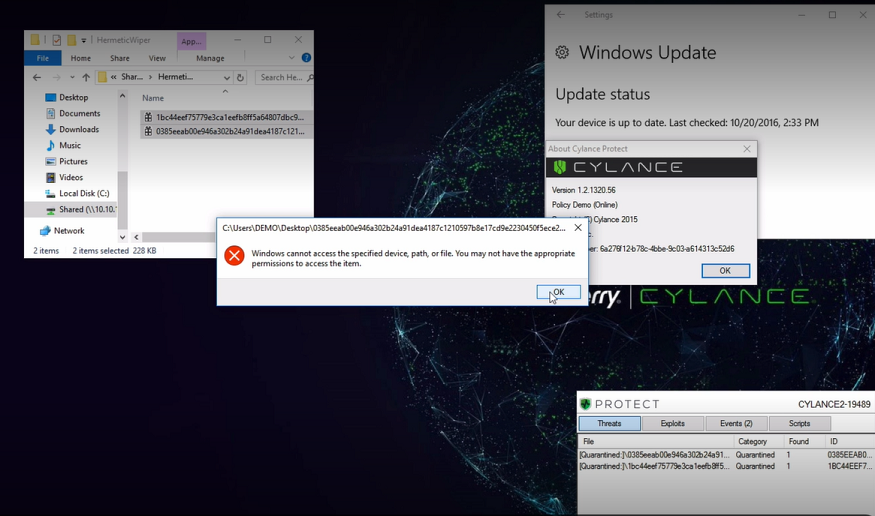
HermeticWiper, a new malware first seen by ESET and Symantec, has been observed infecting organizations in Ukraine, Latvia, and Lithuania. Leveraging a digital signature from “Hermetica Digital,” and using real recovery drivers (from EaseUS), the attack relies on transitive trust in order to perform its malicious behavior. While some organizations have noted that ransomware has been seen deployed alongside, potentially as cover, this threat appears to be solely focused on destruction of data.
The wiper, seen being implanted via Active Directory, places the appropriate drivers on the victim machine as a Windows® service. After establishing a foothold, the system’s Master Boot Record is destroyed and the machine is rebooted, preventing the device from initializing.