The saying, “With chaos comes opportunity,” applies whether one is seeking to do good—or bad. The latter was evidenced by a recent phishing campaign put forth by a threat group seeking to take advantage of the turmoil in Ukraine to prey on European government personnel as they were assisting refugees.
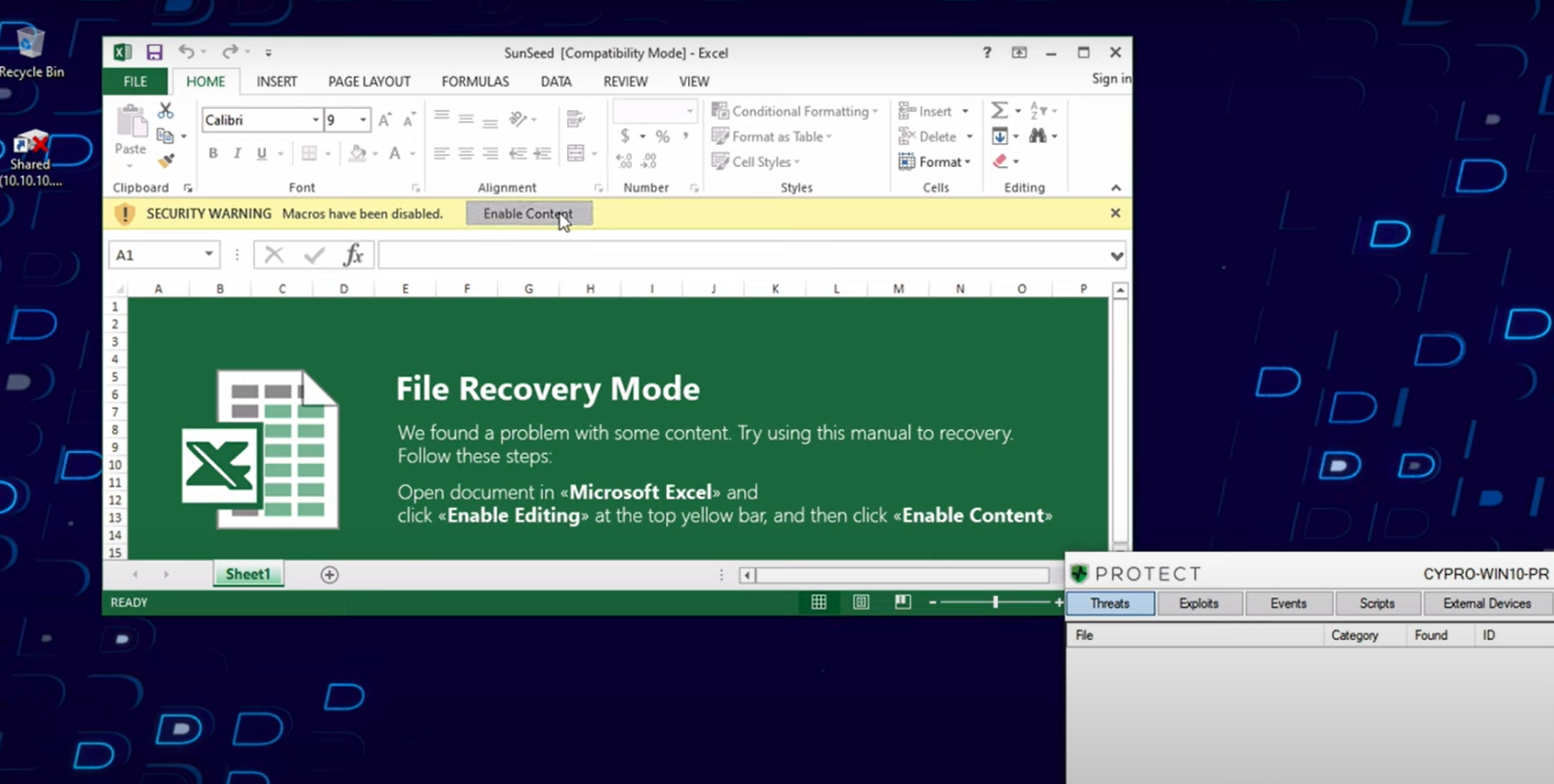
Researchers discovered the attacker’s tactics resemble those of Ghostwriter—also known as TA445 or UNC1151, which was previously identified as working in the interests of Belarus. In this attack, the threat group used an email originating from a UKR[.]net address to formulate a new email containing a malicious Excel® document, then sent the weaponized message to a European government entity. UKR[.]net is a popular Ukrainian ISP and provider of personal email accounts. The email had the following subject line: “IN ACCORDANCE WITH THE DECISION OF THE EMERGENCY MEETING OF THE SECURITY COUNCIL OF UKRAINE DATED 24.02.2022.” Once a user opened the official-looking email and Excel file, the macro would install SunSeed malware onto the victim’s system.
Findings also indicated the “sender’s” email account used in the attack might belong to a member of the Ukrainian military, who may have been victim of an earlier phishing campaign targeting both civilians and soldiers in Ukraine.
To see how BlackBerry prevents SunSeed malware attacks from occurring, check out the video below.