Threat Thursday: Unique Delivery Method for Snake Keylogger
A recently found downloader for Snake Keylogger brings several slippery evasion tactics together. It socially engineers its victims, targets organizations/users that failed to patch a known exploit, and uses a variety of twists and turns in an effort to evade traditional antivirus (AV) products. In this blog, our team digs into this threat to find out exactly how it works and what takeaways we can share with people to help protect them from this extremely stealthy threat.
In a recent threat campaign, the Snake Keylogger was delivered by a downloader that uses an unconventional file type as a lure, in addition to using embedded files within that lure, encrypted shellcode, and remote code execution exploits. The Snake Downloader uses these techniques like tall grass to hide its path toward an intended target.
Because of the public’s familiarity with Microsoft® Office formats, DOC and XLS files tend to be the lure documents of choice for threat actors. Because of this, it is far less common to see a PDF file like the one used by this threat as the initial vector in an attack. We’ll examine why the author of Snake Downloader chose this uncommon threat vector and what it reveals about the threat actor’s intentions and ultimate goals.
Operating System
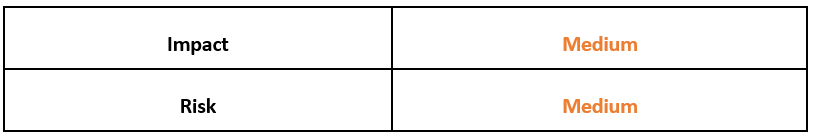
Risk & Impact
Technical Analysis
For an initial understanding of how this attack is structured, let’s look at the different files involved in our analysis of the downloader and how they relate to each other.
Here are the files used:
- “REMMITANCE INVOICE.pdf” – The original PDF attachment/lure document
- “has been verified. However pdf, jpeg, xlsx, .docx” – The DOCX file used to download the rich text format (RTF) file via macros. It is opened by the PDF lure after prompting the user.
- “f_document_shp.doc” – The RTF document downloaded by the DOCX file; it holds the malformed objects.
- “00000000.ole” – The object linking and embedding (OLE) object extracted and reconstructed from “f_document_shp.doc”
- “00000000.bin” – The encrypted shellcode extracted from “00000000.ole”
- “fresh.exe” – Snake Keylogger
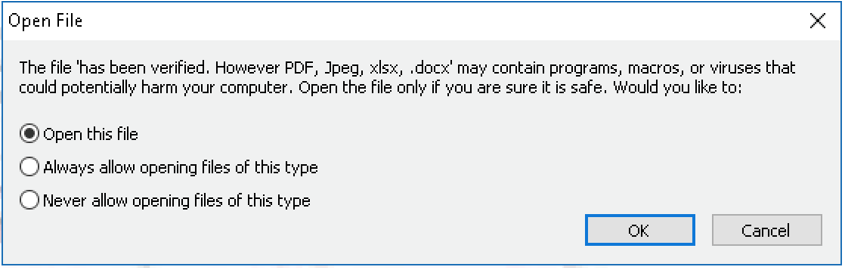
HP Wolf Security recently discovered this threat when they came across a PDF attachment named “REMMITANCE INVOICE.pdf.” Running this file prompts the user to open a DOCX file, which is deceptively named “has been verified. However PDF, Jpeg, xlsx, .docx.” This strange choice of filename was chosen for a specific reason; at a casual glance, the filename cleverly makes it appear as if the file has been automatically vetted and verified by the victim’s machine, as shown in Figure 1.
This is a type of social engineering that relies heavily on the victim only giving the popup a cursory glance. The threat’s author hopes that the victim will be too busy or distracted to properly read the “Open File” dialog, which means that many people working in a fast-paced office environment may fall victim to this threat.
Figure 1 – Prompt displayed after opening “REMMITANCE INVOICE.pdf”
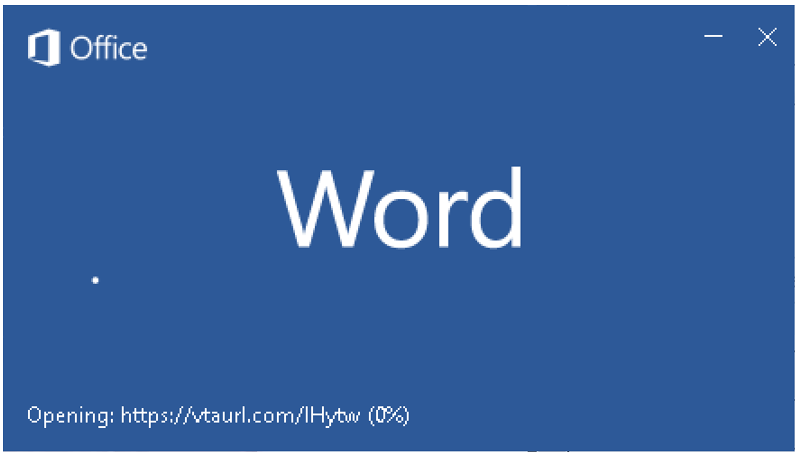
If this DOCX file is opened and macros are enabled by the victim, this triggers the download of an RTF file while displaying the strangely named document in Microsoft® Word. Users who look closely will also see that Word reaches out to a certain URL while loading, as shown in Figure 2, coinciding with DNS requests to the same URL.
Figure 2 – URL displayed when loading Word
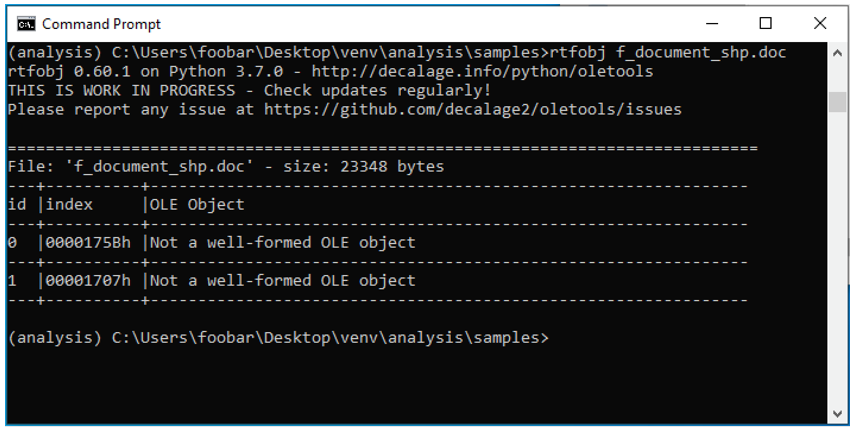
For a closer look at the file, our team viewed the Office Open XML (OOXML) file contents and found the URL (vtaurl[.]com/IHytw) in the document’s relationships file. We can also see that an OLE object is being loaded from this URL. Once the RTF document (f_document_shp.doc) is downloaded, we can check it for any OLE objects, such as the two malformed objects shown in Figure 3.
Figure 3 – Malformed OLE objects found in f_document_shp.doc
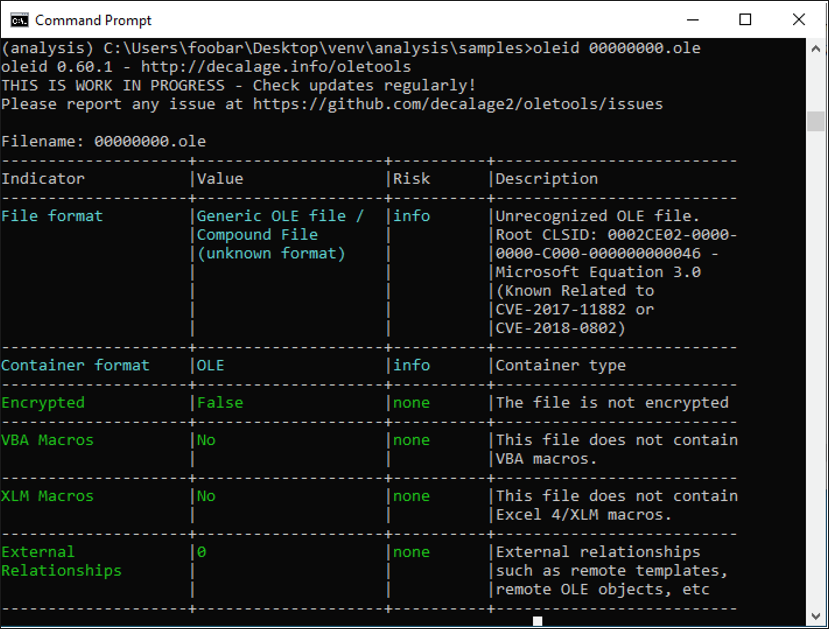
To take a closer look at these OLE objects, we reconstructed them first, as seen in Figure 4. Then, using oletools to view information about the objects, we find that one of them (00000000.ole) mentions the Microsoft Equation Editor in its description. This feature is often used by attackers to exploit known Word vulnerabilities to execute arbitrary code.
Figure 4 – Information about one of the reconstructed OLE objects
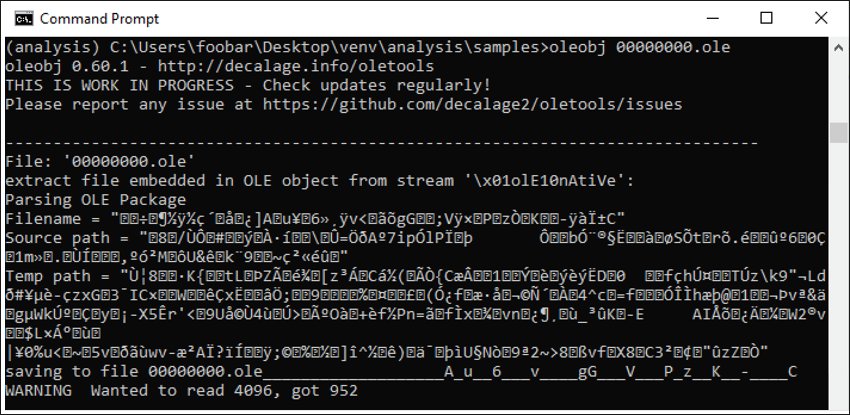
Following this information, we find shellcode in the OLE that exploits the Equation Editor’s remote code execution vulnerability (CVE-2017-11882). This vulnerability was patched over four years ago, but there are still many unpatched machines in the wild that remain vulnerable. The shellcode is shown being extracted from the OLENativeStream structure of the object in Figure 5.
Figure 5 – Extracting encrypted shellcode from 00000000.ole
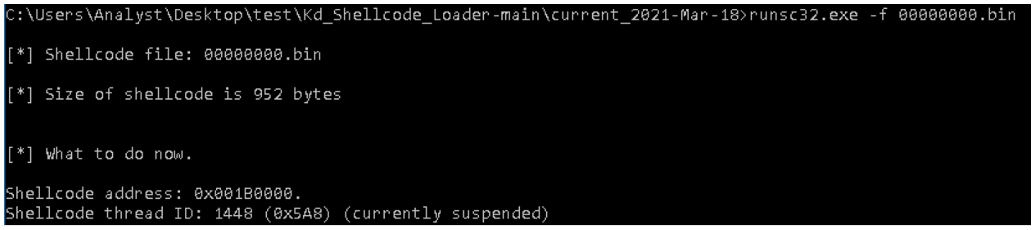
Since the shellcode is encrypted at first, we must look for the moment during execution where it decrypts itself. To do so, we can use a tool like runsc to convert the extracted shellcode into executable code (see Figure 6), then walk through the code with a debugger.
Figure 6 – Converting shellcode to attach to debugger
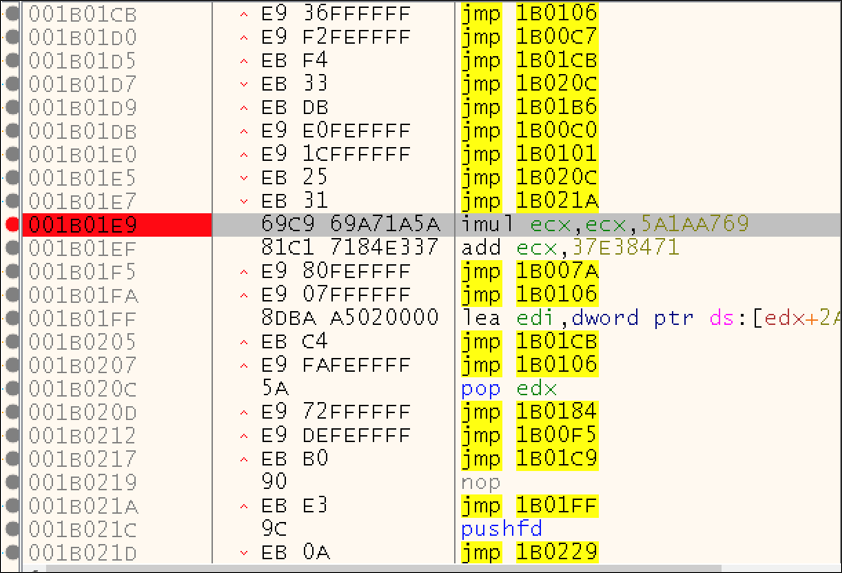
As we step through the shellcode, after defining the correct offset, the file begins decrypting itself. In particular, the highlighted instruction shown in Figure 7 is quite revealing. For each iteration of this decryption loop, it shows a specific register (ECX) getting multiplied by a static value and added. Mathematic operations like this can be typical for decryption routines.
Figure 7 – Mathematic operations used in shellcode decryption
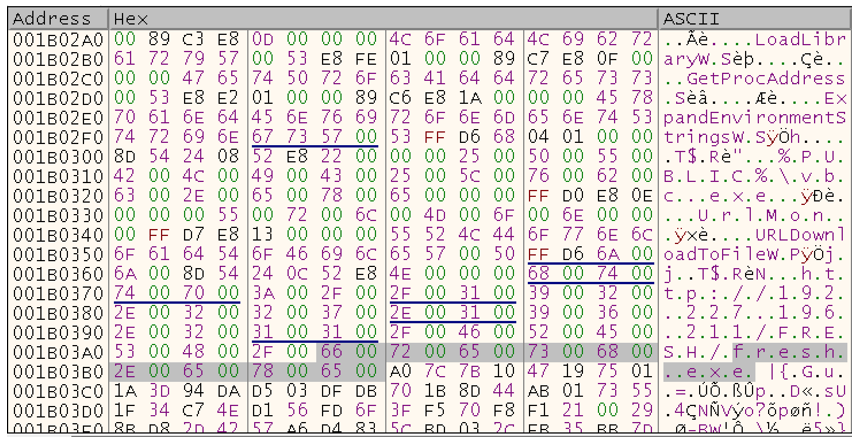
If we follow the dump from register ECX, it reveals more and more with each iteration as the shellcode is decrypted. When finished, a reference for downloading fresh.exe can be seen, which is the Snake Keylogger itself. This keylogger is a prevalent information stealer, also known as the 404 Keylogger, which has been in circulation since late 2020. This decrypted shellcode can be seen in Figure 8.
Figure 8 – Decrypted shellcode used to download Snake Keylogger
Once the shellcode in the RTF file downloads the keylogger, the Snake Downloader has done its job, and now it’s up to Snake Keylogger to continue from here. Keyloggers such as Snake lurk in the background on an infected machine and wait for the user to input any juicy information via the keyboard, particularly website logins, such as those used for banking or a cryptocurrency wallet. That information then gets exfiltrated back to the threat actors and used for their own financial gain.
Conclusion
Although it may be less common to see PDFs used as malicious file attachments, they should still be taken just as seriously and handled with the same precautions as any other potentially infected attachments. In the case of Snake Downloader, the lure document is only the first step in an array of tactics used to obfuscate the installation of the Snake Keylogger payload.
From its use of embedded files, encrypted shellcode, and even remote code execution exploits, it’s clear that this downloader goes further than most to hide its initial execution on the system. While the CVE-2017-11882 exploit had a patch created for it in 2017, it has been a slow process to get all affected machines patched, which means it’s still one of the most common vulnerabilities that threat actors continue to exploit. This latest example speaks to the prevalence of such attacks, and emphasizes the ongoing need for diligence when it comes to patching your organization’s endpoints, and distrusting attachments and files shared over the internet.
Who is Affected?
Those with machines still vulnerable to CVE-2017-11882 could be infected by Snake Downloader/ Keylogger malware. The Snake Downloader threat is not confined to a particular industry or sector, but rather takes advantage of busy or distracted individuals to perpetrate its malicious activity.
Mitigation Tips
You can take the following steps to reduce your exposure to this threat:
- Always remain cautious when opening email attachments, regardless of file type.
- Be sure to carefully read all security popups when you’re being asked to manually enable something on your machine, particularly macros.
- Ensure you stay up to date with all Security Updates from Microsoft to stay protected from exploits like CVE-2017-11882.
- Monitor accounts for unusual and unauthorized access that falls outside of the baseline (MITRE D3FEND techniques D3-AZET, D3-LAM).
YARA Rule
The following YARA rule was authored by the BlackBerry Research & Intelligence Team to catch the threat described in this document:
rule Snake{
meta:
description = "Detects Snake"
author = "BlackBerry Threat Research Team"
date = "2022-06-03-"
license = "This Yara rule is provided under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0) and open to any user or organization, as long as you use it under this license and ensure originator credit in any derivative to The BlackBerry Research & Intelligence Team"
strings:
$s1 = "Game1Screen_Form_Load"
$s2 = "get_KeyCode"
$s3 = "Good luck mate"
condition:
filesize < 1000KB and all of them
}
|
Indicators of Compromise (IoCs)
05dc0792a89e18f5485d9127d2063b343cfd2a5d497c9b5df91dc687f9a1341d
250d2cd13474133227c3199467a30f4e1e17de7c7c4190c4784e46ecf77e51fe
165305d6744591b745661e93dc9feaea73ee0a8ce4dbe93fde8f76d0fc2f8c3f
f1794bfabeae40abc925a14f4e9158b92616269ed9bcf9aff95d1c19fa79352e
20a3e59a047b8a05c7fd31b62ee57ed3510787a979a23ce1fde4996514fae803
|
References
https://threatresearch.ext.hp.com/pdf-malware-is-not-yet-dead/#
https://www.bleepingcomputer.com/news/security/pdf-smuggles-microsoft-word-doc-to-drop-snake-keylogger-malware/
https://www.socinvestigation.com/pdf-campaign-delivering-snake-keylogger/
https://www.zdnet.com/article/this-malware-spreading-pdf-uses-a-sneaky-file-name-to-trick-the-unwary/
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you, providing around-the-clock support where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
Related Reading:
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.