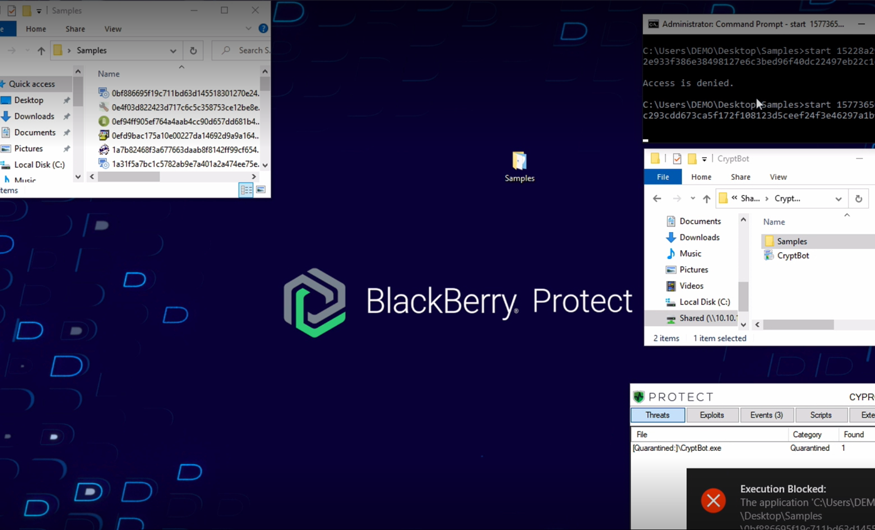
CryptBot has returned. This malicious infostealer is now streamlined and as dangerous as ever, with a sharpened focus on data-capture functionalities.
When CryptBot targets a user’s endpoint, it seeks browser login credentials, crypto wallets, stored financial account information, and additional sensitive data of interest to attackers. The stolen data is then sent back to attackers through a command-and-control (C2) address, where it is exploited for monetary gain.
CryptBot first struck in 2019 and returned with a recent outbreak of attacks in early 2022. The infostealer often lures potential victims through compromised software pirate sites, where the malware masquerades as “cracked” versions of commercial software packages and video games. Attackers draw victims to these sites via sophisticated search engine optimization (SEO) promotion techniques.
The updated variant of CryptBot malware no longer comes equipped with anti-sandbox and exfiltration functions. When downloaded, the newly trimmed malicious file is about half its original size, which allows the infection processes to occur more often — and at faster speeds. CryptBot’s deceptive presentation and increasingly efficient form make it a hazardous threat to home and corporate users alike.
See how BlackBerry prevents CryptBot attacks in our demo video below, which shows our AI-powered endpoint protection solution, CylancePROTECT®, going head-to-head with a live sample of CryptBot Infostealer.