Black Hat Look-Back: Linux Implants – A Silent, Long-Living Threat
As implants on Linux® systems continue to gain prevalence and create blind spots in organizations’ security posture, the BlackBerry Threat Research and Intelligence team continues to advise practitioners on how to best fortify their Linux defenses. In fact, I recently returned from Black Hat 2022 in Las Vegas, where my team members and I spent time doing just that.
In the Linux world, as in the rest of IT, the most basic set of rules is proving no longer sufficient to protect ourselves from today’s threat actors. But there is still much that we can do if, like our adversaries, we are willing to learn and adapt.
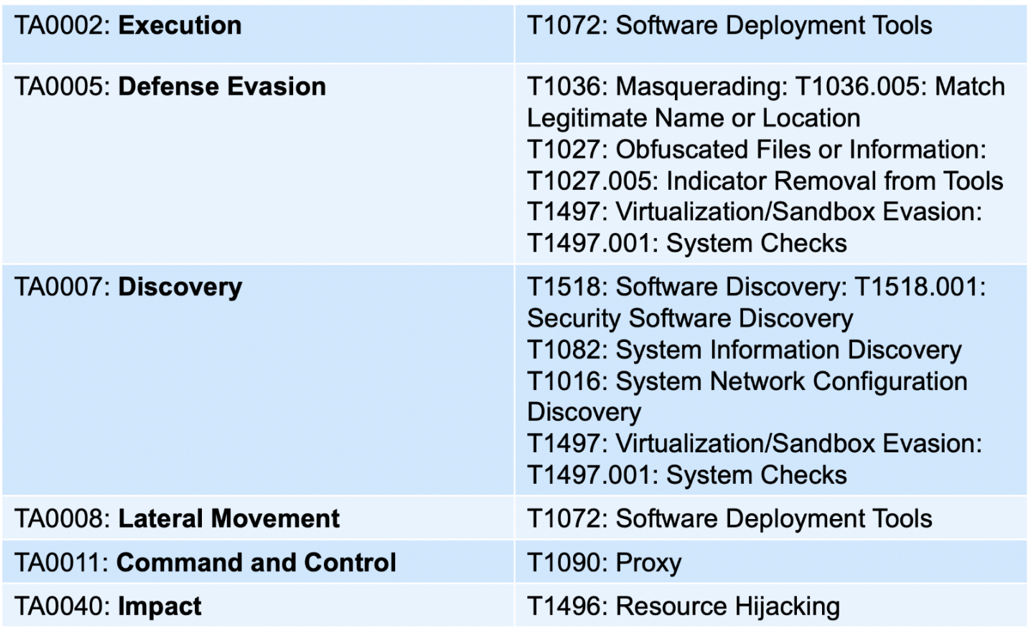
By studying three prevalent malware families — Symbiote, Orbit, and Red Alert Ransomware — BlackBerry threat researchers have developed a map of shared tactics, techniques, and procedures (TTPs) that are common among these families, and which are represented in the MITRE ATT&CK® Matrix.
For your convenience, BlackBerry has posted a JSON implementation of the shared TTPs for the Symbiote, Orbit, and Red Alert ransomware families on our
GitHub repository.
TTPs to Focus On
While there are numerous shared TTPs among these Linux ransomware families, in the opinion of BlackBerry threat researchers, the most advantageous tactics to focus on are MITRE TA0005 (defense evasion) and TA0007 (discovery). Both tactics represent events that occur early in the attack chain. If this activity is spotted in time, defenders can mitigate the impact of an attack before more damaging actions occur, such as credential access, lateral movement, or data exfiltration – or before any ransomware payload is detonated.
These TTPs often include the use of living-off-the-land techniques. These techniques seek to avoid detection by relying on legitimate tools already present in the victims’ environment, which are commonly used in standard, non-malicious activity, including:
- cURL and Wget, used to pull files
- Proxy scripts, particularly SOCKS5 proxies, reverse or otherwise
Attackers are investing significant time and resources to design stealthy attacks because of the immense financial opportunity at stake. If today’s threat actor is thwarted by a security policy, they often will take the time to attempt a workaround to defeat the detection, until, by trial and error, they eventually succeed.
Virtualization
In addition to more standard public cloud attacks, Linux threat actors have begun moving into the private cloud using seeking to attack virtualization environments. Rather than encrypting each file on an individual virtual machine (VM), attackers are targeting the hypervisors, as a way to compromise the whole VM infrastructure — including virtual disks and virtual memory — in a singular action.
In particular, two of the largest ransomware families (LockBit and BlackBasta) now have ESXi-specific variants as well as Linux variants, for encryption.
Amid this trend in virtualization attacks, Linux servers are at significant risk, especially when confronted with ransomware. Moreover, many organizations are inadequately prepared for these attacks, often opting for limited protection based on an outdated notion that Linux is seldom targeted, and so does not require adequate security controls.
Overall Telemetry Observations
During this period of heightened Linux-based threats, BlackBerry threat researchers have relied on our own internal telemetry to monitor threat levels and activity. Based on data from the past 30 days, we have made the following observations:
- Cylance® AI-based technology has prevented 20,620 attempted attacks on Linux systems using Linux-based malware.
- From the perspective of BlackBerry’s telemetry, the top geographic targets are the United States, South Korea, Mexico, and Brazil.
- The transportation industry is among the verticals under the greatest attack, followed by commercial and professional services, and the public sector. These sectors cumulatively represent over 60% of the past month’s Linux attack telemetry. This tallies with the fact that these industries generally favor the use of Linux systems both on servers and embedded systems.
Recommended Countermeasures
Prevention against these ransomware families is possible by using effective countermeasures. We recommend the following:
- Be prepared for an attack. Assume there will be an attack and eliminate the element of improvisation with a tested and rehearsed response plan.
- Conduct Purple Team tests to emulate threat actors, determine effectiveness, and assess gaps.
- Avoid the use of generic playbooks for protecting against ransomware and have specific plans for specific attacks, specific threat actors, and specific weapons.
- Evaluate recovery plans and posture, early and often.
- Reduce attack surface and apply a least-privilege policy by removing unnecessary services and ensuring they don’t run with root privileges.
- Apply patches in a timely and consistent fashion.
BlackBerry Stops Symbiote, Orbit, and Red Alert Ransomware
Customers using CylancePROTECT® are protected from Symbiote, Orbit, and Red Alert Ransomware.
About CylancePROTECT
CylancePROTECT endpoint protection platform (EPP) employs BlackBerry seventh-generation Cylance AI technology, which uses advanced machine learning models to provide a predictive advantage against both zero-day threats and legacy cyberattacks.