LockBit 3.0 Ransomware Abuses Windows Defender to Load Cobalt Strike
LockBit, a ransomware-as-a-service (RaaS) threat, just weaponized a Microsoft® antivirus tool so it will deliver Cobalt Strike payloads. And this new version, LockBit 3.0, now shares similar functionality with ransomware families such as BlackMatter, DarkSide, and BlackCat.
LockBit 3.0
This latest version, LockBit 3.0, is also known as LockBit Black, the internal name used by the threat author as part of the ransom note. Once deployed, LockBit 3.0 encrypts all files on the victim’s machine and changes both parts of affected files’ name, rendering the files both unusable and unrecognizable.
The ransom note for Lockbit 3.0 is quite extensive compared to many other ransomware families. In this missive, the author explains that they will publish data stolen from victims if they don’t pay the ransom. The note goes on to explain that the “double-extortion” threat could cause victims to violate the General Data Protection Regulation (GDPR) – the European Union’s data protection law – implying that victims may be subject to legal fines when their information is made public.
It's notable that LockBit’s threat actor apparently anticipated the possibility of its TOR infrastructure, used to communicate with their victims, being taken down. To provide redundancy, the ransom note for this version includes several different Onion servers and Tor2Web proxies (used for accessing TOR via traditional browser).
Leveraging Cobalt Strike to Drop LockBit 3.0
Cobalt Strike beacons are side-loaded to the system through a malicious DLL that decrypts the payload onto the user’s system. Researchers found these beacons can later be used to gain a further foothold on a target network, to download or execute malicious payloads in the future. The BlackBerry Research and Intelligence Team profiled Cobalt Strike Beacons in-depth in their 2021 publication, Finding Beacons in the Dark: A Guide to Cyber Threat Intelligence.
Once attackers have gained initial access to an organization, the actions they can take are fairly open-ended. From the content of their ransom note, it’s clear that the attacker’s primary goal is to get payment from their victims, after having gathered and exfiltrated sensitive data to the attacker’s infrastructure for “insurance.” Whether they will take additional steps beyond this is up to the threat operator and will likely depend on whether they see the need or opportunity.
LockBit 3.0 also abuses the Windows Defender command line tool MpCmdRun.exe to decrypt and load Cobalt Strike payloads. This file is used to scan for malware as part of the Windows Defender security app.
Which Organizations Should Be Concerned About LockBit 3.0?
All organizations should remain cautious of this threat. There are currently no known methods to decrypt the LockBit 3.0 encryption. Public exposure of personal and sensitive data has serious consequences.
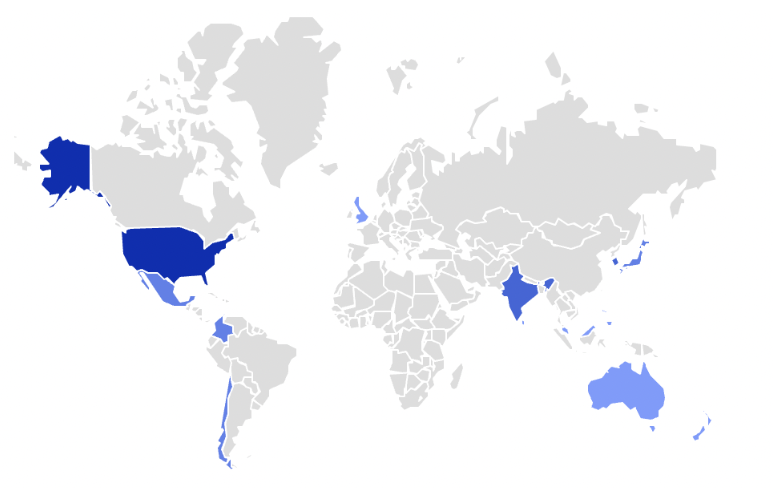
According to BlackBerry telemetry, there were at least 478 blocks on LockBit malware family in our tenants. That’s about five attempts per day worldwide, as shown in Figure 1 below. This includes both previous LockBit versions as well as LockBit 3.0.
Protecting Against RaaS Campaigns Like LockBit 3.0
The BlackBerry Threat Research and Intelligence Team recommends implementing the following strategies to protect against RaaS attacks:
- Continuously monitor and patch software and firmware assets.
- Regularly review the rights and privileges of all accounts. Remove accounts and privileges that are not needed to perform necessary job functions.
- Monitor failed password attempts, password changes, and creation of new users.
- Enable a 24x7 SOC enhanced with Sigma, Suricata, and Yara rules. Empower it with professional, high-quality feeds.
- Hunt for anomalies and not just for matches.
- Extend your visibility over all network assets.
- Enable good visual data representations so that you can easily identify data exfiltration in outbound network traffic.
- Test and implement a reliable backup system. Backups must be inaccessible from the primary network so the threat actor cannot encrypt them.
- Conduct Purple Team exercises based on LockBit tactics, techniques, and procedures (TTPs) to test security posture and detection capabilities.
Indicators of Compromise (IoCs)
| SHA-256 |
| 0d38f8bf831f1dbbe9a058930127171f24c3df8dae81e6aa66c430a63cbe0509 9a34909703d679b590d316eb403e12e26f73c8e479812f1d346dcba47b44bc6e 39c363d01fb5cd0ed3eeb17ca47be0280d93a07dda9bc0236a0f11b20ed95b4c 80e8defa5377018b093b5b90de0f2957f7062144c83a09a56bba1fe4eda932ce 391a97a2fe6beb675fe350eb3ca0bc3a995fda43d02a7a6046cd48f042052de5 506f3b12853375a1fbbf85c82ddf13341cf941c5acd4a39a51d6addf145a7a51 742489bd828bdcd5caaed00dccdb7a05259986801bfd365492714746cb57eb55 a56b41a6023f828cccaaef470874571d169fdb8f683a75edd430fbd31a2c3f6e b951e30e29d530b4ce998c505f1cb0b8adc96f4ba554c2b325c0bd90914ac944 c6cf5fd8f71abaf5645b8423f404183b3dea180b69080f53b9678500bab6f0de d61af007f6c792b8fb6c677143b7d0e2533394e28c50737588e40da475c040ee f9b9d45339db9164a3861bf61758b7f41e6bcfb5bc93404e296e2918e52ccc10 fd98e75b65d992e0ccc64e512e4e3e78cb2e08ed28de755c2b192e0b7652c80a |
Yara Rule
| rule LockBit3_ransomware { meta: author = "BlackBerry" date = "08-03-2022" version = "1" tlp = "white" description = "Rule detecting Lockbit3 ransomware samples" strings: $code1 = {004E01536574506978656C0000590153657454657874436F6C6F7200006B01546578744F757457000067646 933322E646C6C0063004372656174654469616C6F67506172616D570000} $code2 = {7D0C66AD6685C07505E98A0000006683F841720C6683F84677066683E837EB266683F861720C6683F86677 066683E857EB146683F830720C6683F83977066683E830EB02EBBC0FB6C8C1E10466AD6685C07502EB436683F841720C6 683F84677066683E837EB296683F861720C6683F86677066683E857EB176683F830720C6683F83977066683E830EB05E97 2FFFFFF32C1AAE96AFFFF} $code3 = {FFFF8BC885C974348BF78BD166B82000F266AF85C975128BCA894DFC8B7D0CF366A56633C066ABEB132BD14A87D1894 DFC8B7D0CF366A56633C066AB8B45FC5F5E5A8BE55DC2080090558BEC81EC840000} condition: uint16(0) == 0x5a4d and filesize < 3MB and 2 of them } |
BlackBerry Stops LockBit 3.0 and Cobalt Strike
Customers using CylancePROTECT® are protected from LockBit 3.0 and Cobalt Strike.
To combat this highly effective and infectious malware variant, BlackBerry recommends using artificial intelligence-based agents trained for threat detection on millions of both safe and unsafe files, in addition to the aforementioned security practices. For example, Cylance® AI uses automated security agents to block LockBit 3.0 based on numerous file attributes and malicious behaviors, rather than relying on a specific file signature.
Customers can take this protection a step further with the use of the CylanceGUARD® managed Extended Detection and Response (XDR) service to defend against LockBit 3.0 attacks.
About CylancePROTECT
CylancePROTECT endpoint protection platform (EPP) employs BlackBerry's seventh-generation Cylance AI technology, which uses advanced machine learning models to provide a predictive advantage against both zero-day threats and legacy cyberattacks.
About CylanceGUARD
CylanceGUARD is a subscription-based 24x7 managed extended detection and response (XDR) service. BlackBerry expert analysts act as an extension of your team, correlating telemetry across devices and providing actionable intelligence to prevent threats quickly while minimizing alert fatigue.
