Jupyter Infostealer: Watch BlackBerry Bring It Down to Earth (Video)
Jupyter Infostealer lurks deep within legitimate installer packages, waiting for any opportunity to steal sensitive user data. After activation, this threat receives executables and malicious PowerShell scripts from its command-and-control (C2) server, including an infostealing module which swipes the user’s log-on credentials, administrative rights, workgroup and browser password databases.
Jupyter can also grab cookies from common browsers such as Google Chrome™, Microsoft Edge®, Opera, Brave, and Mozilla Firefox, along with login information and “autofill” data such as the user’s name, physical address, and email. Like many other information stealers, Jupyter also targets crypto wallets, as well as virtual private networks (VPNs) and remote access software.
In the past, Jupyter has gone by many names, including SolarMarker/Deimos, Polazert, and Yellow Cockatoo. Malware authors have continued improving its stealth features. For example, Jupyter is often wrapped with .MSIs, which are large Windows® installer packages. Commonly, these packages are signed with legitimate digital certificates. While the packages’ legitimate files run, Jupyter executes malicious actions in the background through a small, well-hidden PowerShell script.
The developers of this infostealer do not appear to target specific organizations and seem to lack a fixed agenda. They instead tend to target any user who might fall into Jupyter's deceptive trap which makes it a widespread threat.
BlackBerry Stonewalls Jupyter Infostealer
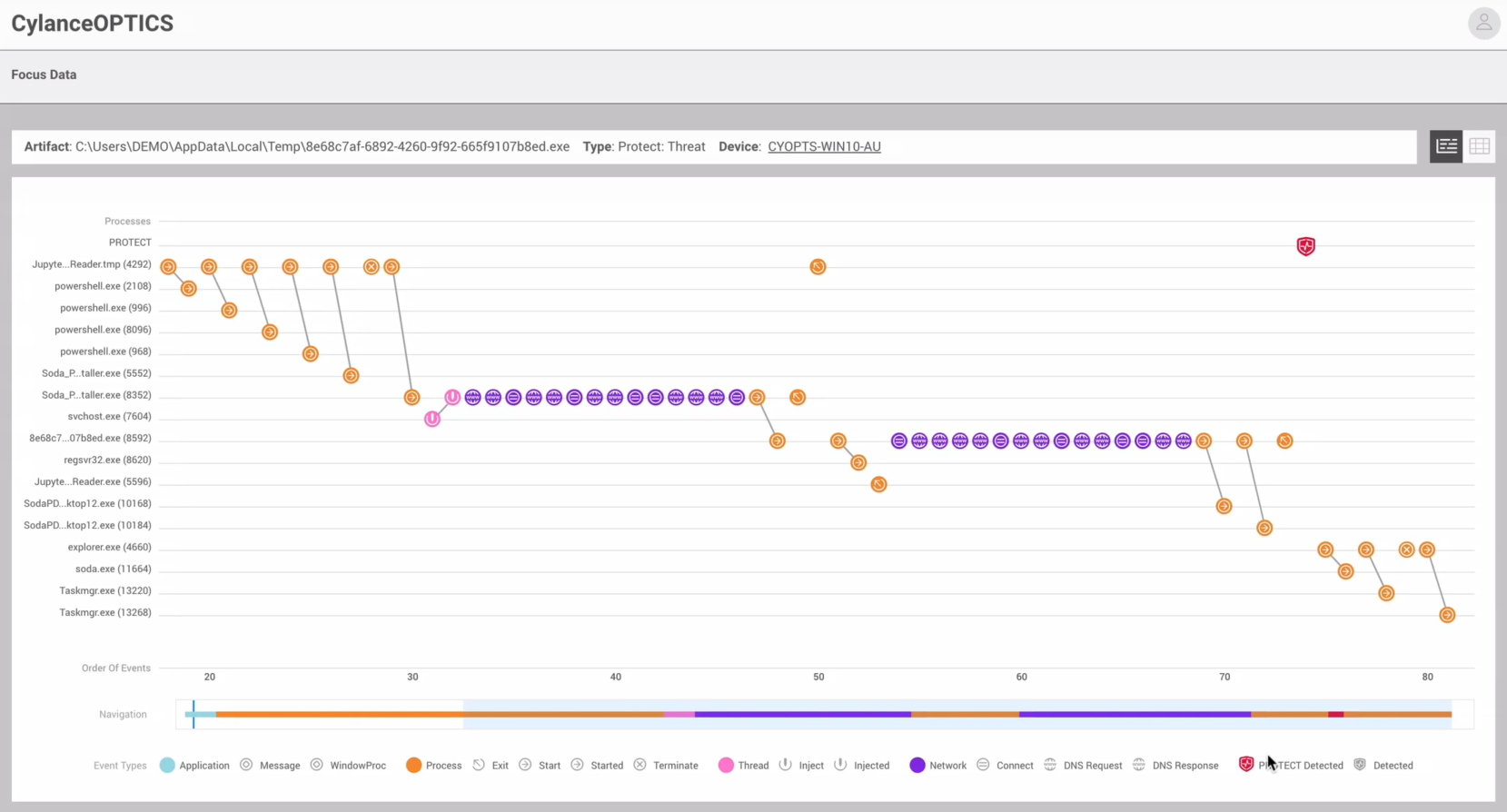
Watch our demo video below to learn more about Jupyter Infostealer attacks. See how BlackBerry defeats them using our cloud-enabled Endpoint Detection and Response (EDR) solution CylanceOPTICS® in conjunction with CylancePROTECT®, our artificial intelligence (AI) powered Endpoint Protection Platform (EPP).
DEMO VIDEO: BlackBerry vs. Jupyter Infostealer
BlackBerry Assistance
The BlackBerry Incident Response team can work with organizations of any size and across any vertical, to evaluate and enhance their endpoint security posture and proactively maintain the security, integrity, and resilience of their network infrastructure. For emergency assistance, please email us at DLIR@blackberry.com, or use our handraiser form.