Cyber Threat Intelligence: How CTI Boosts InfoSec Defenses
These past months, I’ve indulged in my passion for speaking about how cyber threat intelligence (CTI) helps defenders anticipate and mitigate attacks. I’ve written a blog about it (Benefits of Cyber Threat Intelligence and Who Offers It) and have been interviewed about it on BlackBerry LIVE (Contextual Threat Intelligence: How CISOs Can Level Up Their Cyber Defenses). You might think, what more could I say about CTI that hasn’t been discussed already?
Well, there is more I want to share, this time from a recent keynote presentation on the topic. You can watch or listen to my presentation, “How Threat Intelligence Is Evolving to Address Advances in Adversary Attacks,” from the 2022 BlackBerry Security Summit under the keynote section.
Cyber Threat Intelligence Puts Names Back on the Map
For those who follow me on social media, you already know I love analogies.
I want you to imagine that you’re trying to make your way to a place you’ve never been to before. You look at your navigation app for directions but realize it’s missing the street and highway names. You have close to zero context about where you go next. You will probably start to take wrong turns, and the odds that you will arrive where you need to be — when you need to be there — are greatly diminished.
This is how it can be for CISOs and infosec leaders who try to map out an effective security defense strategy without CTI. They want to drive the organization in the best direction, by focusing on the most relevant threats for their industry, but aren’t exactly sure how to get to that point. To navigate the cyber threat landscape requires context, not just noisy indicators of compromise (IOCs) that just add to an already noisy environment. Effective cyber defense is based on contextual threat intelligence, which helps improve an organization’s cyber resilience.
CTI and Cyber Resilience
Within the context of cyber threat intelligence, the National Institute of Standards and Technology (NIST) defines cyber resilience as the ability to anticipate, withstand, and efficiently recover from cyberattacks, as well as being able to adapt quickly to new environmental stresses as your organization navigates through the threat landscape. While we typically think of resilience in the context of an ongoing attack, I like to take it a bit further and say that cyber resilience is a continuous improvement loop that must be repeated before, during, and after an attack. So, what does that look like?
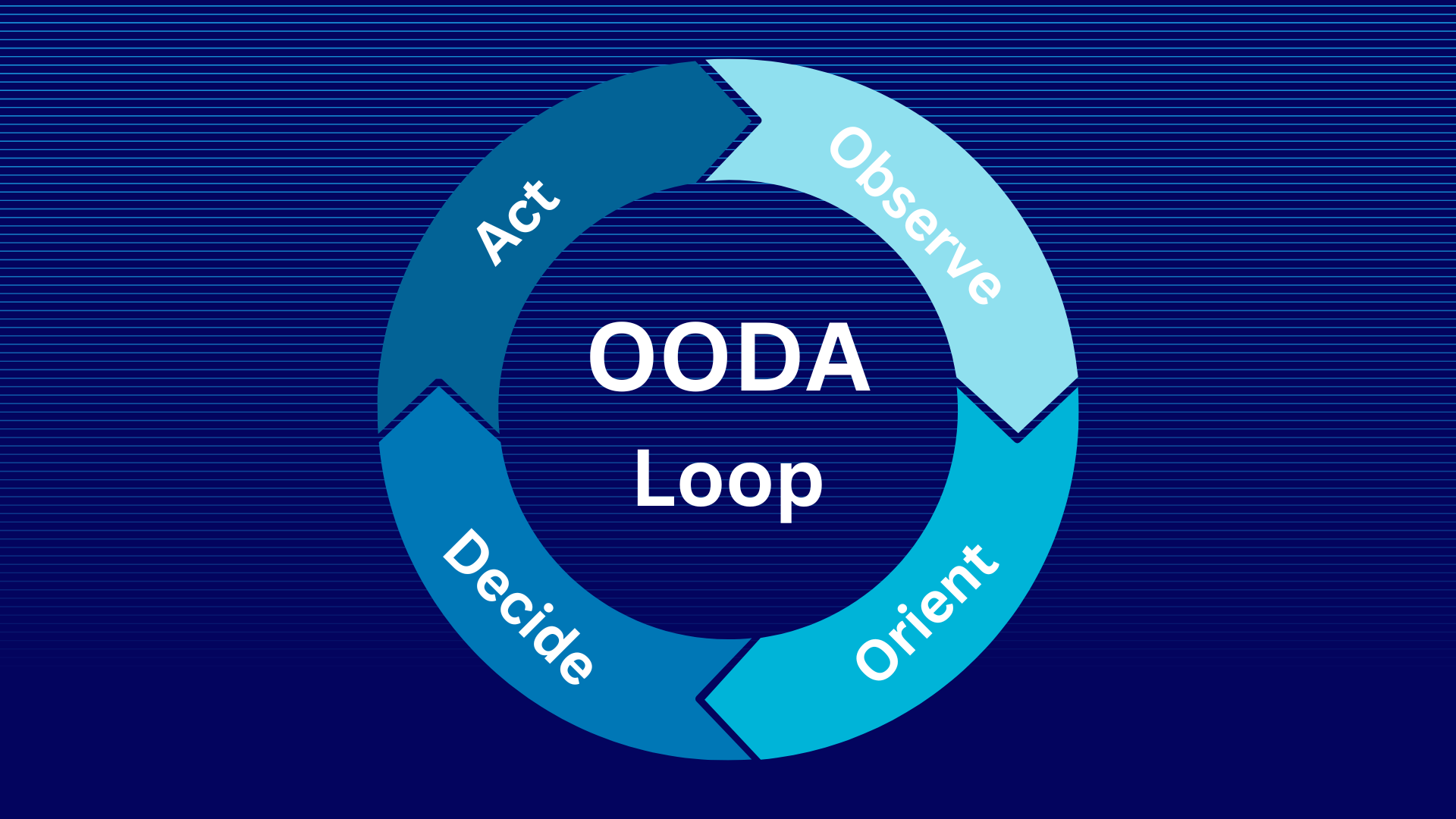
Luckily for us, back in 1976, a military strategist and Air Force colonel by the name of John Boyd developed the OODA loop model.
Intelligence and OODA Loop Decision Making
Boyd came up with the OODA decision-making model to explain how one side in a conflict could gain an advantage over the opposition. The key to this model is in how quickly and effectively one side can go through the decision cycle of observe, orient, decide, and act – as shown below. Whichever side is faster in this contest has the advantage.
How does this model apply to cyber defense and cyber threat intelligence? Well, it’s much like the way mature businesses gather data on consumer behavior specific to their target audience, then extrapolate insights and implications, devise a plan of action based on the insights, and implement it. In the realm of cybersecurity, it looks something like the following:
Observe
What do we need to observe? Well, obviously we need to keep an eye on threats, but we can’t observe all of them, it’s just not feasible. So, we observe the threats that are applicable to our industry. Now, which ones are those?
Answering this question is not always cut and dried because threat actors can easily change their scope of work. For instance, when the BlackBerry Threat Research and Intelligence Team initially observed the malicious actor named RomCom, its target appeared to be only government entities, as it was focused on attacking Ukrainian military infrastructure. However, as our team continued its investigation into this previously unknown actor, it discovered that RomCom had launched new campaigns that targeted IT companies, food brokers, and manufacturers in the U.S., Brazil, and the Philippines. It was – and still is – also in the process of new cyber weapon development, to launch more attacks worldwide.
Without this type of actionable threat intelligence, how will you be able to anticipate, withstand, recover, or effectively adapt?
Orient
Once we have our observations, what are the insights and implications? We need to orient ourselves to the threat and understand how this would apply to our organization. What are the implications of conducting business in specific locations? A change in geography can change our threat model completely! Where are our assets at risk? What impact could a given attack have on our organization if we do nothing?
Decide and Act
Now, given what our insights tell us, what could we do with our available resources of time, budget, and available cyber defense technology in our environment? How will we implement these countermeasures as part of a defensible security architecture?
Remember, the faster an organization can get through this OODA process, the better chance it has of getting a leg up on threat actors.
And to help organizations do just that, our team has launched a contextual cyber threat intelligence subscription service to empower you at the tactical, operational, and strategic level.
BlackBerry Cyber Threat Intelligence Service
This intelligence service is designed to save organizations both time and resources, by focusing on specific areas of interest tailored to each organization’s security goals. Think of it as an accelerant for moving through the stages of the OODA Loop cycle. The cyber intelligence service supplies infosec leaders with accurate and timely analysis of threat actor behaviors, motivations, and activities, to assist with threat prevention and detection efforts, as well as to respond more effectively to cyberattacks.
Our team has released numerous “first-to-market” research reports over the past year, leveraging BlackBerry’s data- and AI-driven digital ecosystem and analytical capabilities.
These research reports have revealed new developments in the ransomware and malware space, along with exposing new targeted, state-sponsored APT (advanced persistent threat) activity. Our reports on RomCom, Symbiote, DCRat, Chaos “Yashma” ransomware, and LokiLocker have all been well-received by BlackBerry’s customer base and the broader security community.
And our elite in-house team includes world-recognized threat research leaders, including SANS authors and instructors, former members of law enforcement and intelligence agencies, winners of DEFCON challenges and more. Our CTI analyst network is also distributed around the world, which means we not only understand the language of all the countries we monitor, but also their culture, economy, political structure and current events. That knowledge is crucial, because CTI is not just about technology — as I mentioned earlier — it’s also about understanding geopolitics so we can anticipate attackers.