Arkei Infostealer has upped its game. While cryptocurrency remains its primary target, new analysis reveals this flexible and stealthy infostealer has recently expanded its capabilities to also target Chrome-based browser extensions related to two-factor authentication (2FA) and multifactor authentication (MFA), as well as password management. This increases its risk to both corporate and private environments.
Often sold and distributed as Malware-as-a-Service (MaaS), Arkei infects Windows® operating system users. The use of SmokeLoader as a method of deployment for Arkei has been seen repeatedly and BlackBerry researchers are watching to see if this will develop into a trend among threat actors that use the infostealer.
One feature included in Arkei is a configuration file. This gives the malware more versatility in its application as it allows threat actors to customize the malware’s capabilities and easily change infection tactics. For instance, depending on what is enabled in the file, the malware could target saved password details, raid saved auto-complete forms, browser and extension data, pilfer saved credit card details and browser cookies, or a combination thereof and more.
Organizations typically affected:
- Government
- Commercial and professional service providers (legal, consulting, and healthcare)
- Manufacturers of consumer durables (vehicles, computers, and televisions)
- Organizations in the apparel industry
- Telecommunication service providers
- Organizations in the insurance industry
Arkei’s developers have incorporated a function where the malware will download legitimate files as it executes its attack. These files are often extremely common in corporate networks and on devices. While there are various possible reasons to include legitimate files, one is that they act as camouflage for the attack.
Arkei targets popular browsers, including Google Chrome™ and Firefox™, before it attempts to scrape data for exfiltration. One of Arkei’s more notable functions is its ability to steal data, like cryptocurrencies, from Google Chrome browser extensions. The infostealer also targets specific crypto wallets stored locally on a victim’s device by using a similar function to what researchers observed in BHunt malware.
BlackBerry classifies Arkei Infostealer as a potential medium impact and medium risk level threat to network security.
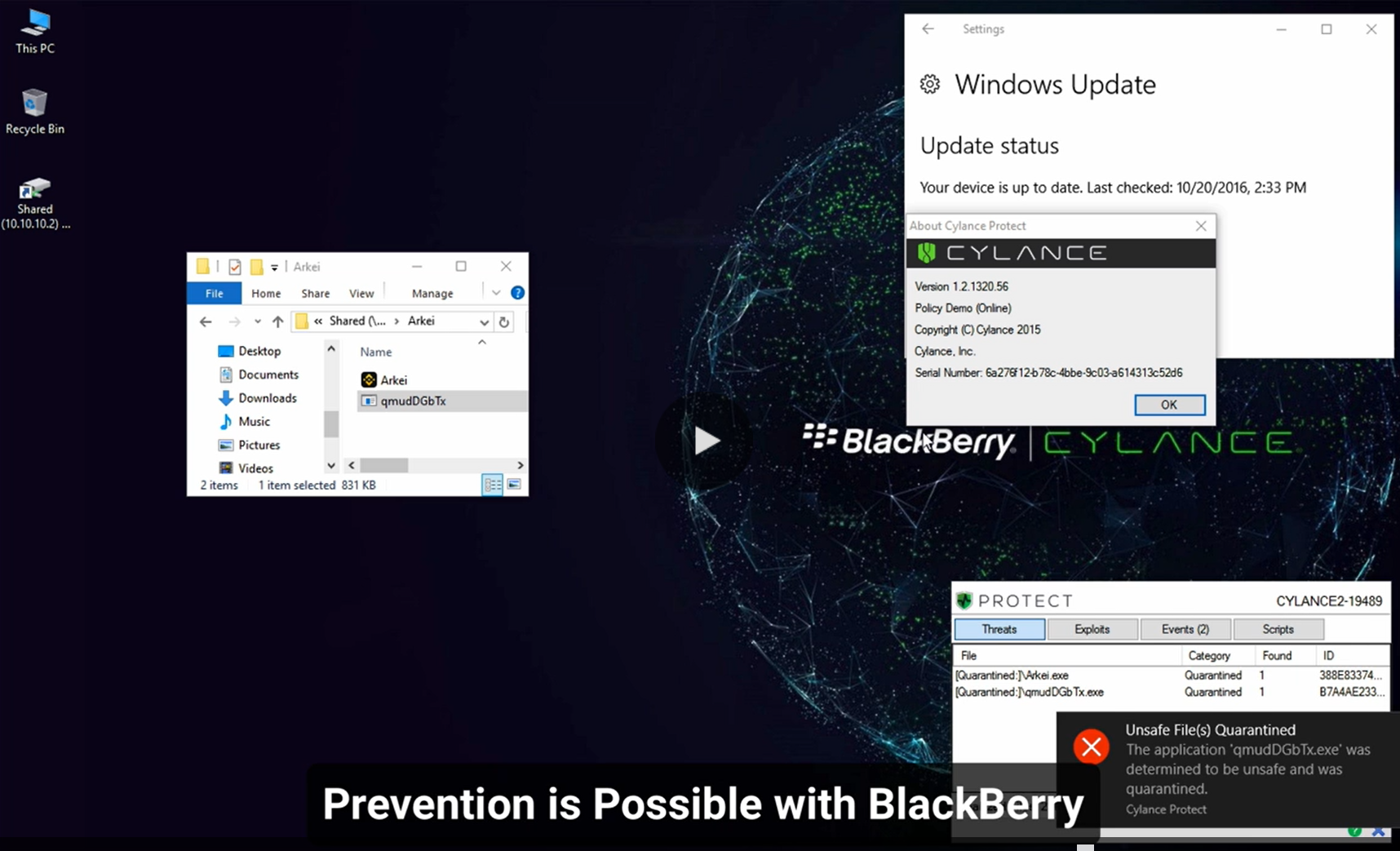
BlackBerry AI Stops Arkei Infostealer
Watch our demo video to see how a known and newly created variant of Arkei Infostealer are defeated by the BlackBerry® Endpoint Protection Platform (EPP) solution, CylancePROTECT®.