Sneaky GPU.zip Technique Steals Sensitive Information From Your Graphics Card
Summary
Researchers from four top American universities have uncovered a new way for threat actors to sneakily access visual information from your graphics card while you're online and browsing certain websites. The researchers call this threat “GPU.zip,” because it takes advantage of the hidden data compression methods used by modern graphics processing units (GPUs) to leak visual data to a malicious third party.
In testing, they found the technique could be used to steal sensitive visual data such as usernames and passwords from a target, without the user being aware of what was happening.
The researchers wrote up their Proof-of-Concept (PoC) findings in a paper, which they will present at the 45th IEEE Symposium on Security and Privacy in San Francisco next May. This blog will help you understand more about how the GPU.zip attack works, and what it means for your online security and privacy.
Weaponization and Tactical Overview
Weapons
|
Modern graphics cards
|
Attack Vector
|
GPU side-channel attack
|
Network Infrastructure
|
Malicious websites
|
Targets
|
Global users of modern graphics cards
|
Technical Analysis
Context
The graphics processing unit is a specialized type of processor used by your computer to accelerate graphics rendering. Originally, GPUs were responsible for rendering 2D and 3D images, including animations and video, but over time, they’ve evolved into more flexible and programmable units. They are now used for everything from video game graphics to high-performance computing, and even for training deep-learning and neural networks.
GPUs compress data as they work, and hardware-based data compression like this can sometimes unintentionally reveal confidential information. This happens because the act of compressing data creates distinct, data-dependent DRAM traffic and cache utilization. To avoid this, software usually turns off compression when dealing with certain types of data.
However, the researchers investigating the GPU.zip flaw found that most modern graphics processors use data compression even when they shouldn't. They do this to boost performance and save memory by using your computer’s hardware to do the job, thus foregoing the need to use additional software. This is great from a computer optimization standpoint, but doing so comes with certain risks.
This compression is often not disclosed to the end user, and varies between chip makers. This is because the graphical data compression algorithms used by GPUs vary widely across vendors and architectures.
The researchers figured out how to exploit this compression to steal visual data from a number of modern processors. More specifically, they demonstrated an attack that extracts individual pixel data through a web browser on various devices.
Their proof-of-concept demonstration used a cross-origin SVG filter pixel-stealing attack (try saying that three times quickly before your first morning coffee). SVG is a web graphics format that allows you to create scalable and interactive vector graphics. Its compatibility, flexibility, and ability to maintain image quality at any size make it a widely-used tool among web designers and developers.
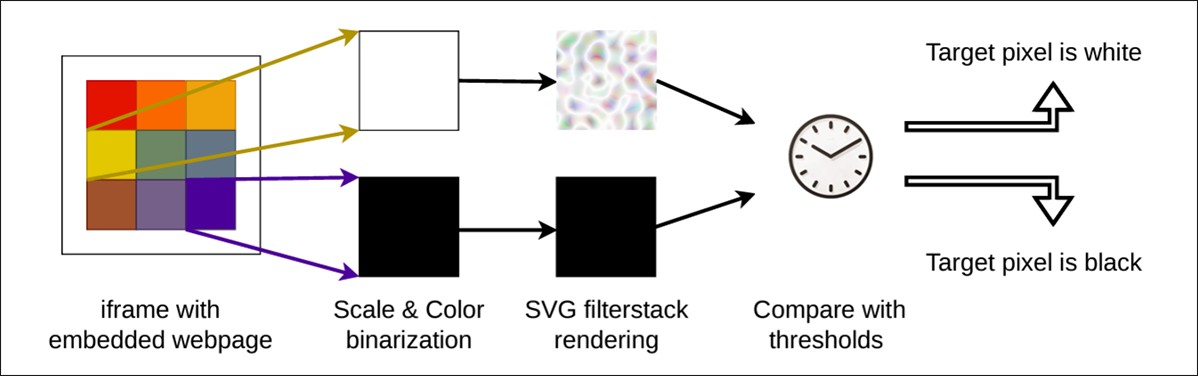
In a cross-origin SVG filter pixel-stealing attack (more coffee, please), the attacker leverages vulnerabilities or loopholes in web browsers, to apply SVG filters to elements on a web page hosted on a different domain – hence the “cross-origin” part of the attack description. These filters can manipulate the appearance of the elements and capture visual data pixel by pixel, effectively "stealing" parts of the visual content.
Figure 1 – Filters applied by the attacker to an iframe with embedded webpage, converting them into two possible colors: black or white. (Source: https://www.hertzbleed.com)
As part of their PoC, the researchers demonstrated a specific attack that could extract a person's username from a web page currently displayed in their browser – as a random example, they chose a Wikipedia iframe.
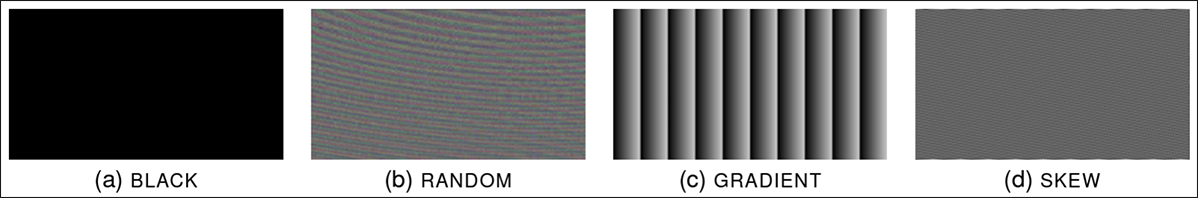
They extracted the username from the host GPU by simplifying the colors on the webpage, and using a special technique based on four different patterns to figure out the original colors, essentially like decoding a secret message.
Figure 2 – The four patterns used by the researchers to facilitate the GPU.zip attack. (Source: https://www.hertzbleed.com)
This means that if a user who is currently logged into a page, such as Wikipedia, opens a new tab and simultaneously visits a malicious website before logging out, the threat actor who owns that website can then exploit GPU.zip to learn the user’s Wikipedia username.
What Is a Side-Channel Attack?
The technique used by GPU.zip is known as a side-channel attack, which is a covert way of gathering information that has been inadvertently leaked. This attack is somewhat similar to another one called "Hot Pixels," where an attacker can pull pixels from a web browser to uncover the user’s navigation history.
GPU.zip differentiates itself because it takes advantage of the hidden data compression in graphics processors to achieve the same result. Put simply, it steals data from other websites that are rendered by the GPU at the same time as data from the attacker’s website – so if you log in to Site A, then stay logged in while opening a new tab in the same browser and navigating to Site B, it would set you up perfectly for this kind of attack. (Not good news for multi-taskers!)
The attacker’s website could begin this data theft by sending carefully crafted requests to the intended victim’s GPU, which then trigger compression or decompression operations on the data of other websites that the user is currently logged into. The attacker can then reconstruct the visual information that is currently displayed on the user’s screen, and scoop up passwords, usernames, or even credit card numbers.
What makes GPU.zip different from other compression-based side-channel attacks? According to the researchers, this new exploit takes advantage of software-transparent uses of compression. This is in direct contrast to previous compression side-channel attacks, which may leak because of software-visible uses of compression. These “visible” attacks can be mitigated by disabling compression in software.
Potential Targets
GPU.zip could potentially impact many big GPU makers and their customers. The researchers alerted the companies that make possibly vulnerable graphics cards about the problem back in March 2023, long before publishing their research.
The scary thing about this technique is that while other more general types of side-channel attack count on some kind of direct access to the user’s device, a targeted GPU.zip attack could be carried out by a bad actor just by remotely luring the target user to a malicious website, using a technique such as email phishing.
GPU.zip could work on a high percentage of laptops, smartphones, tablets, and desktop computers around the world, although it’s worth noting that it takes time and a setup of great complexity to carry out this kind of attack. The process is also extremely slow compared with simpler forms of data theft, such as those carried out via ransomware, which can exfiltrate data seconds (or less) after the initial infection.
In the researcher’s tests, extracting a username took a minimum of 30 minutes on some chips, although the rate of accuracy was very high, ranging from 97% to 98.3%.
The good news is that most websites that typically handle sensitive information already block other websites from embedding their content. This protection makes them safe from the type of pixel-stealing attack that GPU.zip can perform.
Additionally, websites that prevent other websites from showing their content (known as cross-origin iframe embedding) can't be used for this type of data theft through GPU.zip or similar sneaky methods.
Preventing GPU.zip From Stealing Your Data
To stay safe from the techniques used by GPU.zip, simple cyber hygiene will go a long way.
For example:
If in doubt, don’t click. If you’re in the habit of ignoring the security warning when your browser tells you it’s not safe to visit, think again. Use common sense when browsing the web, and be careful what you click. Any sites promising something that seems too good to be true, or any search results offering “free” cracks, keygens or torrents, are best avoided.
Update your web browser often. If you haven’t done so in a while, now might be a good time to check your favorite browsers for any updates or patches.
Close your browser window when you log off any website. This is Security 101 when it comes to checking your bank account online, and it makes sense to get into the habit of doing this with any website to which you login with a username. This will prevent pixel-stealing attacks.
Keep your GPU drivers updated. Find out what brand of processor your system uses by checking your Control Panel > System Information, then check the manufacturer’s website for any driver updates.
Conclusions
The type of attack demonstrated by the researchers against modern graphics processors can pose a serious threat to user privacy and security, as it could allow attackers to access and misuse visual information from web pages without the target's awareness.
It's essential for web developers and browser makers to address and prevent such vulnerabilities to protect users. If you are a web developer, you should configure your website to deny embedding by cross-origin websites. You can find more information on how to do this here.
One final thing to note is that Firefox and Safari web browsers are not as vulnerable to GPU.zip-type attacks, because they don't meet all the conditions necessary for this attack to work. These conditions include allowing other websites to load with cookies, applying SVG filters to certain website elements, and using the GPU for rendering tasks.
The new attack type is outlined in a paper from researchers at the University of Texas at Austin, Carnegie Mellon University, University of Washington, and University of Illinois Urbana-Champaign. It will be presented at the 45th IEEE Symposium on Security and Privacy in May 2024.
Related Reading