Evaluating the Efficacy of Managed Detection and Response (MDR) Services in the Dynamic Threat Landscape of 2024.
The dynamic threat landscape in cybersecurity presents a constant challenge to organizations. From the development of advanced malware to more elaborate social engineering techniques being used by threat actors, defenders must maintain constant vigilance and stay up to date with the latest security strategies to keep assets safe and secure resources.
To help organizations combat today's sophisticated cyber threats and enhance their threat detection capabilities, MITRE conducted a managed detection and response (MDR) evaluation that emulated two notable threat actors: menuPass and BlackCat.
Highlights of BlackBerry Results
Here are some of the achievements of BlackBerry’s Cylance® AI during this evaluation:
Actionable Detections: BlackBerry placed in the top five for Actionable Detections, a significant ranking that underscores our comprehensive approach. The CylanceMDR™ solution by BlackBerry, supported by the Cylance portfolio, detected threats from the very beginning of the attack chain.
Alert Fatigue Prevention: BlackBerry issued 75 percent fewer alerts than the vendor who issued the highest number of alerts during the evaluation. BlackBerry delivered actionable alerts at each critical point of the attack chain, thereby providing prompt insights for the customer and preventing alert fatigue.
Best-in-class Visibility: Through a combination of detected activities, observed tactics, techniques, and procedures (TTPs) plus forensic analysis, the BlackBerry team accurately identified the threat actors menuPass and BlackCat/ALPHV at the earliest stages in both emulated scenarios, along with the specific malware they used.
Protective Security: CylanceMDR successfully detected and provided remediation suggestions for the most critical steps of the attack in both campaigns.
Above and Beyond: The BlackBerry team not only provided alerts for urgent actions and sent timely escalations, but also provided detailed daily reports summarizing each day's activities, showcasing BlackBerry’s commitment to thorough analysis and clear communication.
About the Evaluation
MITRE Engenuity’s ATT&CK® Evaluations: Managed Services — Round 2 represents a pivotal benchmark in assessing the capabilities of vendor participants in analyzing and describing adversary behavior within the MITRE Framework. This evaluation serves as a test for the efficacy of Managed Detection and Response (MDR) solutions in combating sophisticated cyber threats.
Although there were 11 vendors in Round 2 of testing, BlackBerry is one of just eight vendors in the market that have participated in both MITRE evaluations for MDR/Services. During this second evaluation, participants utilized a self-supplied toolset to demonstrate their service capabilities, providing analysis in the same format they would offer to their customers.
What makes this evaluation particularly challenging for participants is its “black box” approach to adversary emulation. Participants are kept in the dark regarding the emulated adversary or adversaries until after the execution is complete.
This round of testing also included a new category: Actionable Detection. MITRE was looking for a timely “scenario detection,” with clear, specific information such as activity, time, location, users and context, enabling a security team to take immediate and effective action to mitigate or respond to a detected threat.
Conducted over a rigorous five-day period in a cloud computing environment (AWS), the complete evaluation emulated two notable threat actors and demanded that participants provide their analysis as if MITRE Engenuity were one of their customers.
Meet the Adversaries: menuPass and BlackCat
Both menuPass and BlackCat are sophisticated entities within the cyber threat landscape; however, their operational tactics and techniques demonstrate distinct differences:
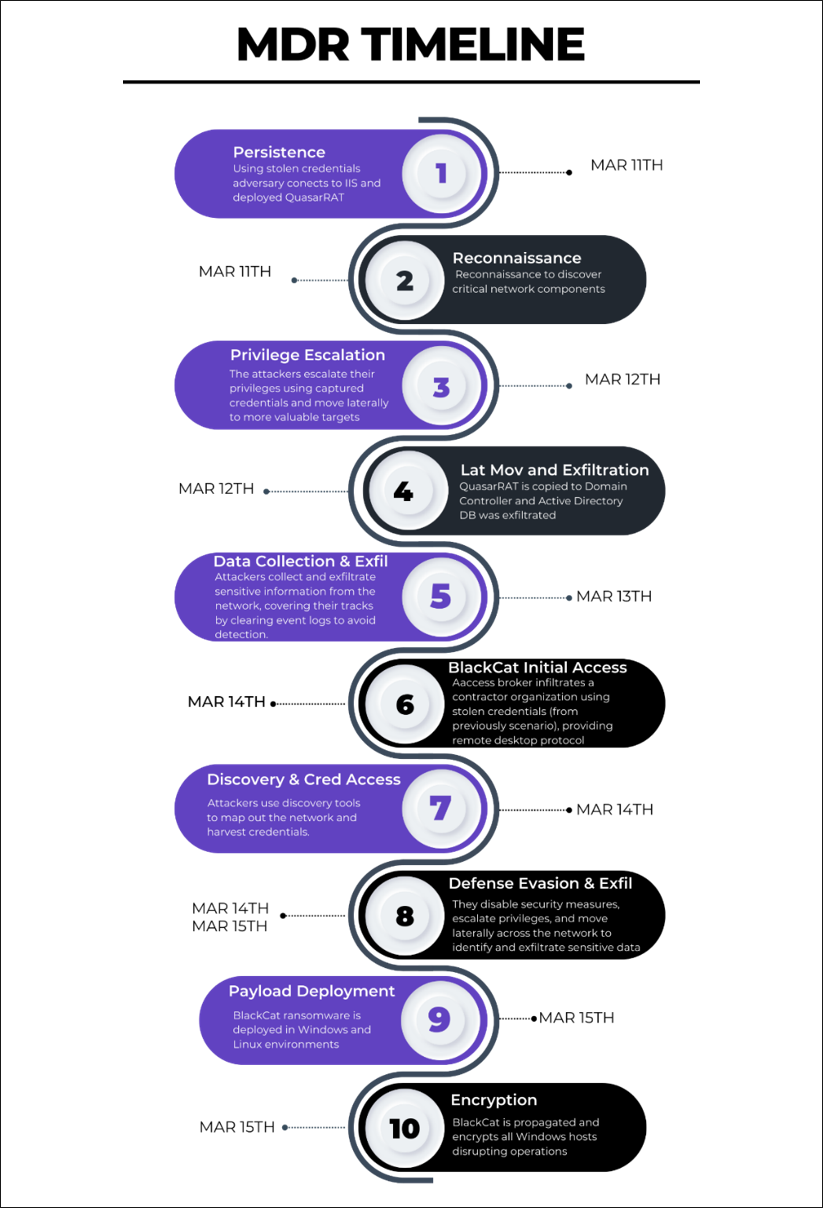
menuPass, also recognized as APT10, primarily engages in state-sponsored espionage, concentrating on gaining long-term strategic access and extracting data across numerous global industries, with a significant emphasis on Japanese targets. Members of menuPass are known to have acted in association with the Chinese Ministry of State Security (MSS). Their approach is methodical, using spear-phishing and custom malicious open-source access tools like QuasarRAT to infiltrate and persist within their targets' networks.
BlackCat, known to operate as ALPHV, represents the new wave of ransomware-as-a-service (RaaS). This prolific Russian-speaking group is notorious for its aggressive monetization strategies, leveraging ransomware attacks that threaten data encryption and leakage to extort money from its victims, often impacting businesses regardless of their geographic or sectoral alignment. While menuPass prefers stealth and sustained infiltration, BlackCat prioritizes rapid financial extortion and public disruption.
Test Results for CylanceMDR
MITRE Engenuity rigorously tested 11 MDR solutions for five continuous days, running 24 hours per day, with this round marking the second iteration of this closed-book evaluation. In this case, the evaluation was divided into two adversary groups: menuPass and BlackCat.
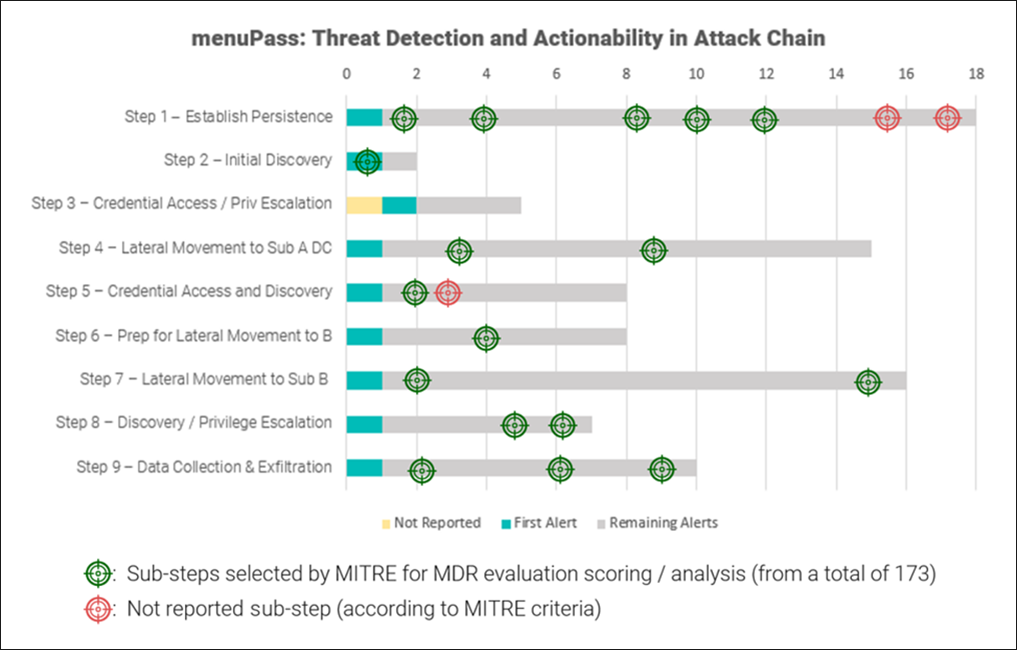
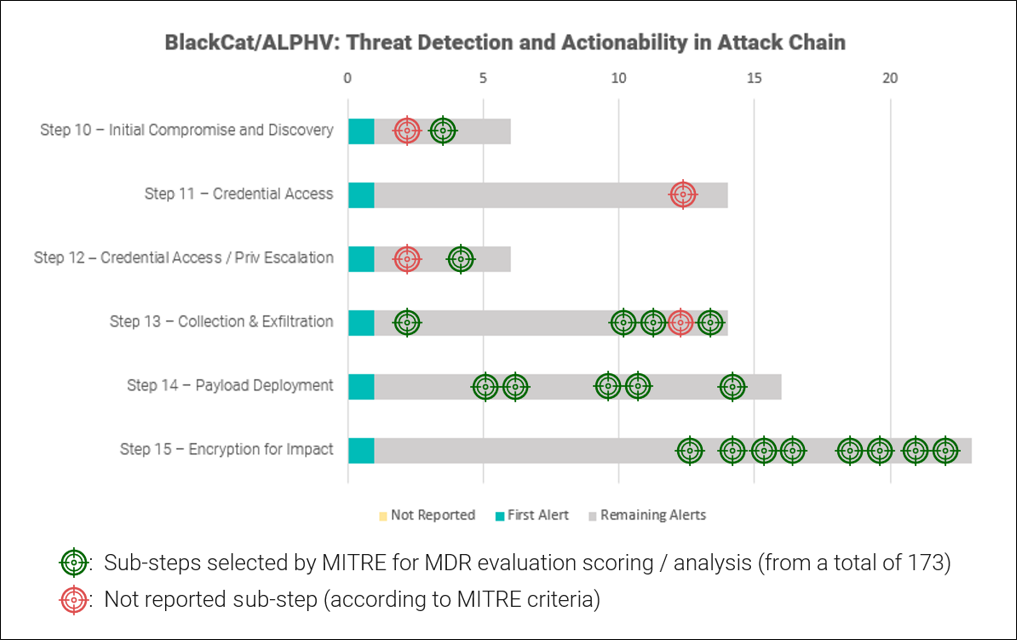
This evaluation tests a vendor’s ability to detect threats that prioritize stealth, leverage trusted relationships and system tools, and inhibit data recovery. The assessment consisted of 15 major steps, encompassing a total of 173 sub-steps, to emulate a complete attack chain.
The CylanceMDR™ solution by BlackBerry, supported by the Cylance portfolio, successfully detected and provided remediation suggestions for the most critical steps of the attack. Out of 11 MDR solutions tested, BlackBerry placed in the top five for Actionable Detections, an evaluation category which assesses the clarity, context and practical guidance of alerts for effective threat response.
Our top five placement highlights our proactive efforts both in reporting potentially malicious activity and in providing detailed context and thorough remediation information.
Out of the 173 sub-steps in the test, 43 key steps were selected by MITRE for final scoring. BlackBerry successfully addressed 35, showcasing the robustness of our solution. It is important to remark that for the eight remaining steps, BlackBerry was fully aware of the attack. As one example, for step 1.B.4 on Reflective Code Loading, we successfully identified the injected Notepad++ process but did not automatically report the in-depth technical details to the customer, as this is not part of our standard procedure.
Despite this, there was extra data in the reverse engineering reports that were produced internally. These reports can be made available to a customer upon request, but in the case of this emulated attack, simply identifying and reporting this data did not fulfill the detection criteria requested by MITRE.
In the context of the MITRE evaluation versus a real-world attack, however, there would have been low to no impact to the customer, as all suspicious artifacts were immediately escalated as malicious due to their behaviors and the activity they performed.
BlackBerry vs. Alert Fatigue
In this round of testing, MITRE graded vendors on Total Alerts sent. This part of the evaluation measured the total volume of alerts received, regardless of whether they pertained to actual malicious attacks, regular user activity, or false positives.
While alerts are important, they can also introduce a significant amount of noise into the SOC. This is a crucial point to understand: Issuing alerts on 100 percent of issues does not equate to effective threat protection. Organizations need to strike a balance between automated defensive actions and signal noise.
During the five-day period of the evaluation, CylanceMDR issued 1207 fewer alerts than the vendor who issued the highest number of alerts during the test, or 75 percent fewer.
By design, BlackBerry products powered by Cylance AI make automated decisions on behalf of the user to preemptively stop attacks before they can cause damage, striking a balance between the volume of robust and actionable reported events, and a lower number of alerts.
This optimal balance helps minimize alert fatigue for security teams, ensuring the MDR service remains both effective and manageable, regardless of the size of the organization or security team.
BlackBerry Results: In Depth
Infrastructure
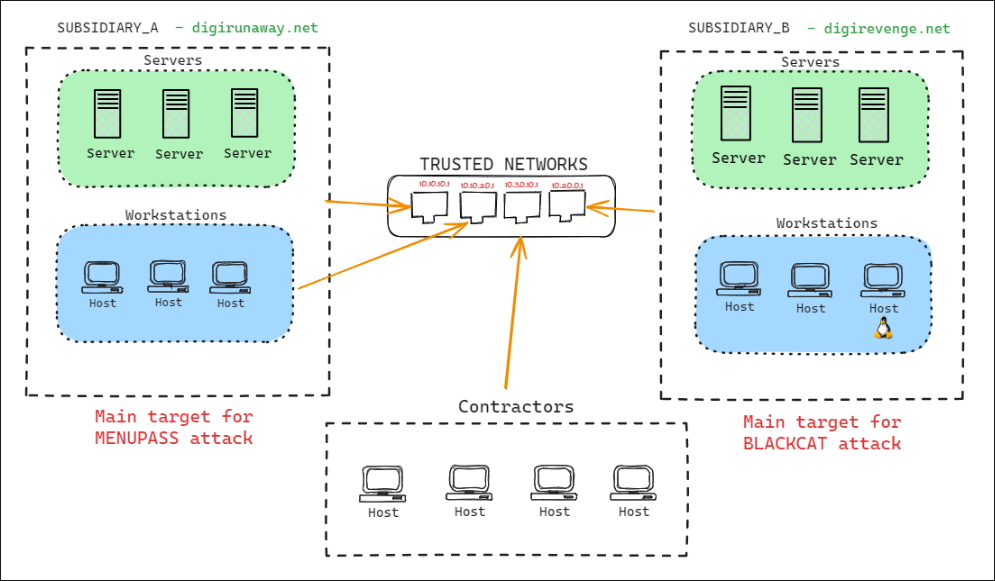
For this year’s MITRE Evaluation, the environment was designed with added complexity in comparison to those of previous evaluations, simulating an enterprise network that included trusted networks across multiple buildings and external connections to contractors.
- The first scenario emulated menuPass’s compromise of two subsidiaries of a fictitious global pharmaceutical company. The emulation replicated menuPass’s use of living-off-the-land techniques, reflective code loading to evade detection, and DLL side-loading to execute the SigLoader, FYAnti, QuasarRAT, and SodaMaster payloads in memory.
- The second scenario introduced a cohabitating ALPHV BlackCat affiliate’s deployment of BlackCat ransomware to Windows® and Linux® ESXi servers in one of the subsidiaries, highlighting defense evasion, data encryption/destruction, and system recovery obstruction behaviors.