Lessons from the Front Line: Network Segmentation
This article is the third in the series from the BlackBerry® Incident Response (IR) team, examining critical behaviours that either stop incidents from happening or greatly reduce their impact. The first two articles can be found here: Vulnerability Management and Proactive Monitoring.
Insight
It may seem strange that we are mentioning the need for network segmentation, but this security measure has been particularly important as of late—not just to slow down advanced threat actors, but also limit the damage of worming and fast spreading ransomware.
Segmentation is the separation of hosts on the network into various zones, often organized by function and business criticality. Segregation is a term often used interchangeably with segmentation and is implied; it is achieved by creating controls and rules about how those network segments are permitted to communicate with each other.
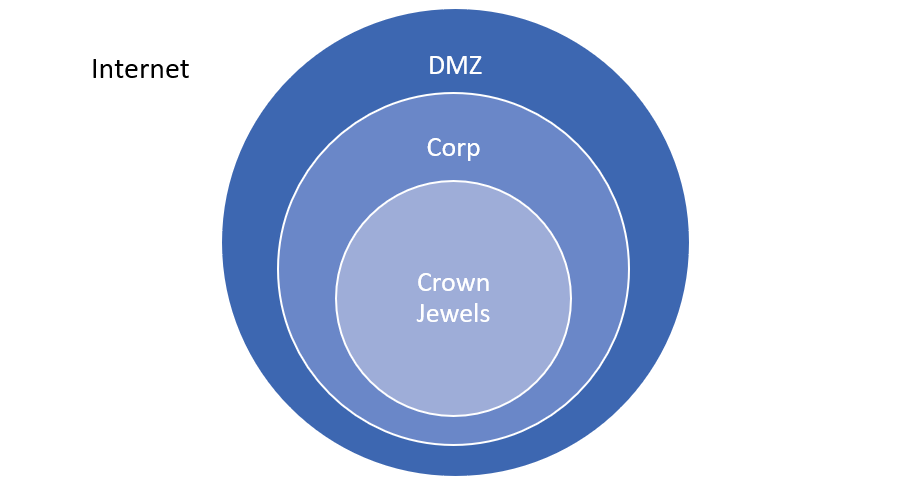
Unfortunately, many consider merely having a demilitarized zone (DMZ) to protect themselves from the Internet as adequate. While this is a critical segmentation point, it is not the only segmentation that needs to be considered. Other opportunities for network segmentation include any areas of the network that have disparate risk levels (PCI, PII, PHI, critical infrastructure etc.) and possibly geographic boundaries.
Figure 1: Network segmentation by geographic boundary
Real-world Scenario
While we have seen plenty of incident response engagements that illustrate the need for robust network segmentation, there is a publicly known incident from June 2017 that best highlights this need. The Wired article titled “The Untold Story of NotPetya, the Most Devastating Cyberattack in History” tells the tale:
“In 2016, one group of IT executives had pushed for a pre-emptive security redesign of Maersk’s entire global network. They called attention to Maersk’s less-than-perfect software patching, outdated operating systems, and above all insufficient network segmentation. That last vulnerability in particular, they warned, could allow malware with access to one part of the network to spread wildly beyond its initial foothold, exactly as NotPetya would the next year.”
This Wired article describes in detail the disastrous events that unfolded from this NotPetya infection. Unfortunately, this type of consequence is not unique to Maersk and it is not unique for NotPetya, but it is true for any organization that faces a worming threat.
Recent Trends
The BlackBerry Incident Response (IR) team continues to track the latest malware trends, which of late includes the ever popular Trickbot family. This malware family effectively combines strong worming abilities with RYUK ransomware to make a formidable foe.
The security industry is also noticing increased capabilities being added to worming ransomware by APT groups such as the Lazarus Group (also known as Hidden Cobra), a group with ties to North Korea. In 2017, researchers linked Lazarus with the WannaCry ransomware worm that caused hundreds of millions of dollars in damage worldwide.
Malware capabilities will continue to improve because attackers understand that the cost of recovering Active Directory and client-facing servers motivates victims into paying ransoms. This is often a complicated cost calculation because it is based on multiple factors such as lost availability, lost revenue, and lost productivity. Not to mention the costs of outside help, additional tooling and protections, and what may be the most damaging of all: the cost of lost reputation.
While there was a time in which breaches could go largely unnoticed if cleaned up quickly; that time is now fading due to an increasing number of cases like Maze Ransomware publicly naming and shaming victims. In the worst instances, data is also intentionally leaked when targets do not pay the ransom. The BlackBerry Incident Response team has noticed a growing trend of other ransomware groups also adopting this tactic.
Tips for Creating Effective Network Segmentation
Many organizations should already have differing degrees of network segmentation in place, but the following should act as a checklist and/or sanity check:
- A DMZ separating the Internet from the Internal network is a must—we have not seen a single legitimate reason why this should not be the case.
- Evaluate the firewall rules between your existing segments—if the firewall rules consist of ANY ALLOWS, that does not really count towards segmentation.
- Consider geographic boundaries as potentially different trust levels. Global companies often operate within countries that may suffer from varying degrees of socio-economic strife or political unrest.
- Attempt to discover systems which may be operating at different trust levels within the same network (PCI, PII, PHI, etc.). Consider segmenting these systems while still maintaining simplicity.
- Consider additional protection of critical infrastructure such as Active Directory, backup servers, application and database servers can often be achieved by grouping similar functions together and whitelisting only allowed communication between network zones.
- Administration for hosts in these protected zones can then be isolated to specific administration segments or using jump boxes and enhanced controls like Multi-factor Authentication (MFA) and closely monitoring for anomalous activity.
Figure 2: Network segmentation based on risk levels
Conclusion
Implementing proper network segmentation is a fine art. Depending on the size of the organization, this segmentation may come in the form of building, region, country, or function. There is no one-size-fits-all solution and firewall management can get quite complicated as the rule sets grow. As usual in this industry, the trick is to strike a fine balance between security and usability.
If you find yourself stuck, it may be beneficial to reach out to your trusted security partner for services such as a network architecture review and/or firewall assessment to get started on this journey. Recent trends and increasingly damaging ransomware tactics will make this investment worthwhile.