Lessons from the Front Line: Principle of Least Privilege
This article is the fourth in the series from the BlackBerry® Incident Response (IR) team examining critical behaviors that either stop incidents from happening or greatly reduce their impact. The first three articles can be found here:
Insight
After exploitation, attackers typically need to escalate privileges to achieve their goals—so don’t make it easy for them. Assigning proper account privileges is a fine balance of providing just enough access to perform the job at hand, but low enough access to lessen damage if the account is compromised. This is the crux of the principle of least privilege and it matters for two main reasons:
1) When a host is compromised via an exploit, the attacker typically assumes the access level (rights) of the vulnerable software that was exploited.
a. Example: Run your webserver with Administrator privileges and it is exploited; the attacker is now an Administrator.
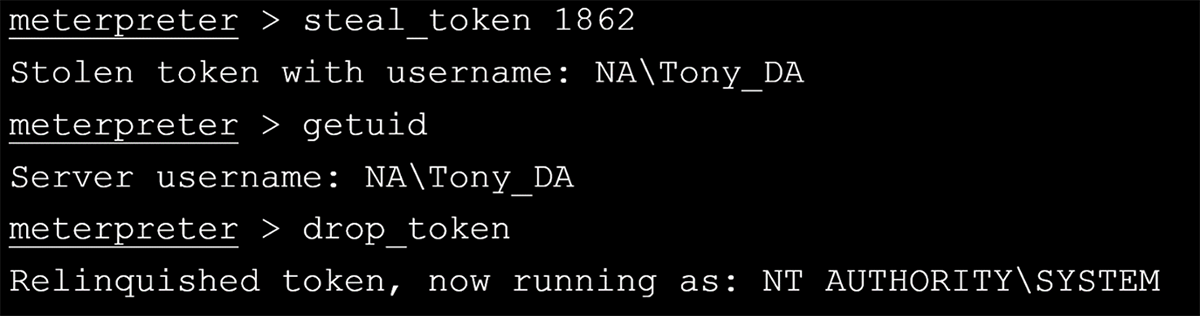
2) If an attacker gains full control over a system (NT AUTHORITY/SYSTEM or Administrator), they can usually steal the tokens of any other process on the system—including domain users.
a. Example: Run your backup application as a domain Administrator account. If the host is exploited and the attacker can migrate to that backup application process or steal the token, voilà, the attacker is now a domain Administrator.
Figure 1: Example of token theft
Real-world Scenario
All too often, the worst incident response cases are the ones in which organizations are not following the principle of least privilege. Sometimes, the very first exploited host has sufficient domain credentials to enable the attacker to laterally move through the network to achieve their goals.
It could be a service account with too much access or even a domain Administrator account that has been cached due to a user login at some point. Either way, this enables the attacker to inflict more harm in a shorter period of time. If by following the principle of least privilege, you make it difficult for the attacker to hunt and achieve sufficient privileges, you give yourself additional opportunity to catch and stop them from causing serious harm.
In a recent real-world example, the BlackBerry Incident Response team traced back the initial compromise to an insecure web application running Microsoft Internet Information Services (IIS). The vulnerability in the application allowed the attacker to upload a variant of the infamous “China Chopper” web shell to maintain persistence. As some might know, China Chopper and most variants are feature-rich web shell that provide many capabilities to the attacker, such as file creation and execution. Making matters worse, the account running the IIS process was also a domain account with elevated privileges. Whilst it was not a “Domain Admin,” the account had sufficient privileges to enable remote logon to most other systems on the network. The attacker used this access to move laterally and harvest remaining credentials needed to achieve their goal.
For those of you following this series of articles you may have spotted some of the other issues from our related posts, including vulnerability management and network segmentation. When combined, these issues can become devastating.
Tips for Following Principle of Least Privilege
This may be one of the most difficult topics we have covered in this series, but hopefully the following will serve as a checklist to get you started:
- Audit the number of privileged user accounts in your domain or forest (Example: How many domain admin and enterprise admins do you have?)
- Audit the number of privileged service accounts in your domain or forest (Example: How many applications do you have that use domain admin or enterprise admin?)
- Do you use privileged account security software? (Example: Password vault for enterprise password management?)
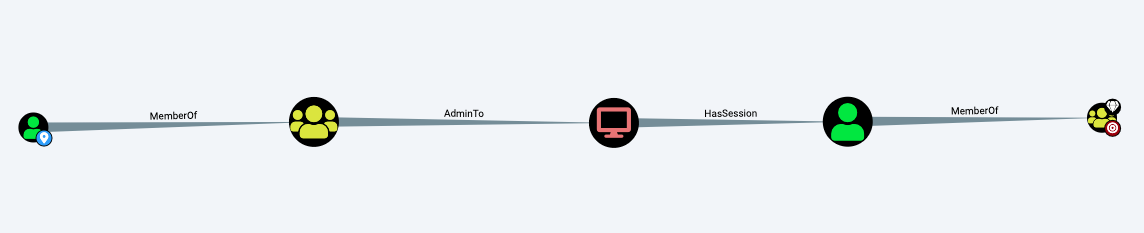
- Conduct a proper red team assessment (Ex: Bloodhound and variants are effective in sniffing out privileged access violations)
Figure 2: Example Bloodhound mapping of escalation paths
It is possible to make privilege escalation more difficult for attackers by reducing the number of privileged accounts, limiting access to those accounts via one-time usage, and by continuously checking and eliminating escalation paths.
Conclusion
Implementing proper hygiene to strictly follow the principle of least privilege is a difficult task, but there is software out there to help maintain and test that hygiene. Combine that software with the right people and training and it is achievable.
Always make the attacker’s work more difficult for them. Frustrate them into making a mistake so you can catch and stop them. Combine this lesson from the front line with the others, and you are becoming a security champion and will be in a much better place to repel attacks against your organization.