Update 03.09.22: Ragnar Locker gang breaches 52 critical infrastructure organizations in the U.S. Learn more.
Summary
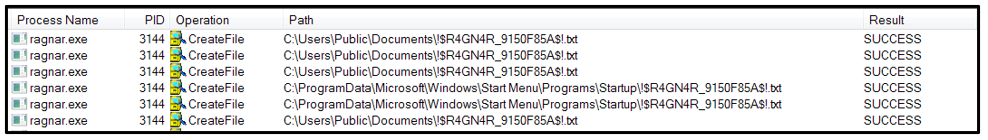
Ragnar Locker ransomware has made international headlines lately due to targeted attacks against ADATA, a leading Taiwanese manufacturer of high-performance DRAM modules and NAND Flash products. The first variant of this family appeared in late 2019.
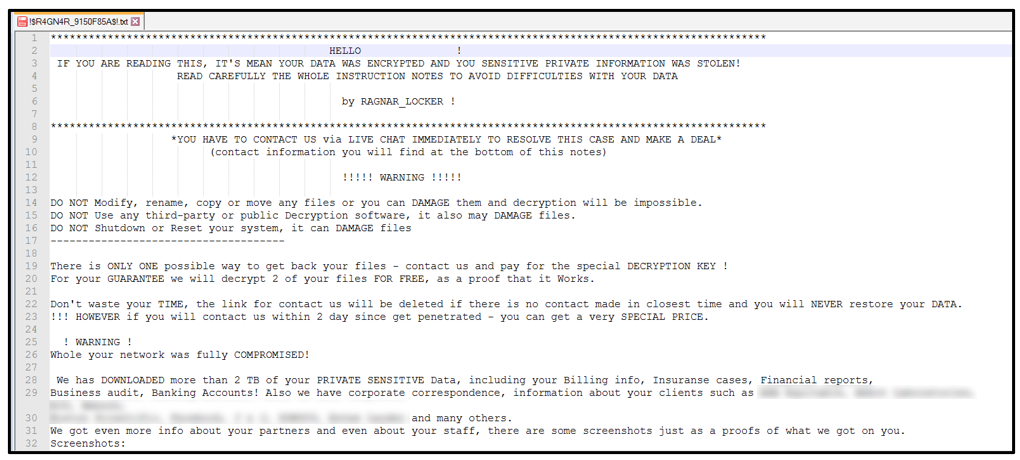
Like many other well-known ransomware variants (such as DarkSide, Avaddon, and REvil), the current variant of Ragnar Locker uses a double extortion technique to encourage victims to pay, where data is both encrypted locally and exfiltrated before the ransom demand is made. If the victim refuses to pay, their data is published to a site located on the dark web at hxxp[:]//p6o7m73ujalhgkiv[.]onion/?BatxqaHm8rKxIP16Z1xB.
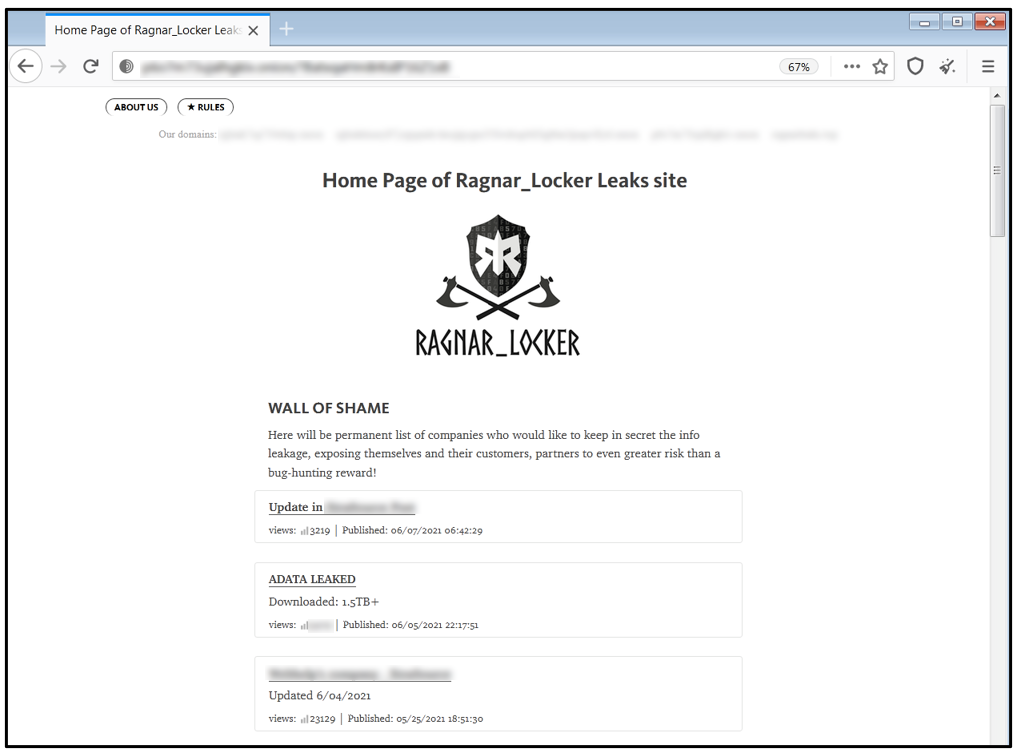
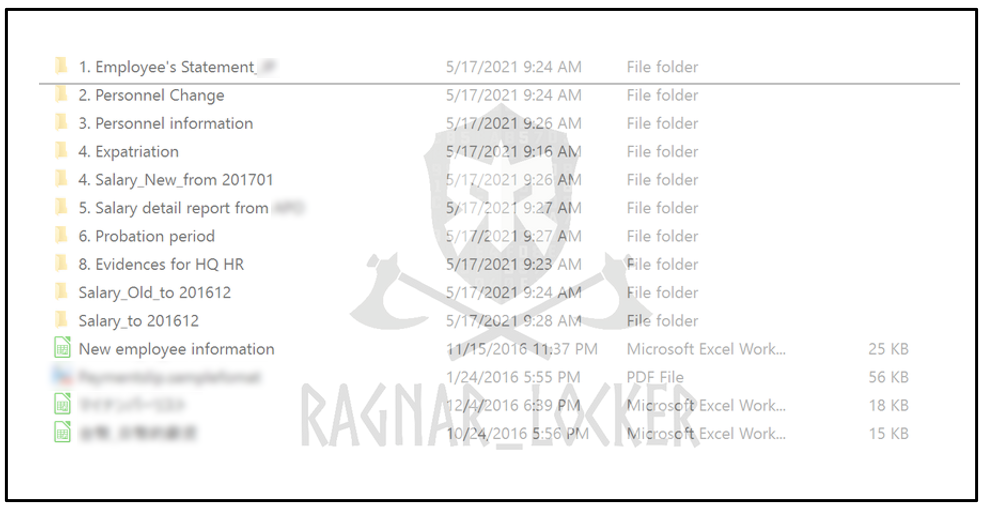
Upon visiting Ragnar Locker’s dark web site, their latest victims can be seen under their self-dubbed “wall of shame”. They currently claim to have exfiltrated 1.5TB of data from ADATA. According to the website, this information has been carefully gathered for a long time.