The BlackBerry® Research & Intelligence team has been tracking and monitoring Cobalt Strike team servers associated with the threat actor TA575, a financially motivated cybercrime group and prolific Dridex affiliate. They are well-known for conducting mass spam campaigns that use malicious document lures to deliver malware such as Dridex, Qakbot, and WastedLocker.
Since February 2021, TA575 have deployed over 50 Cobalt Strike team servers. These servers use unique values in their configurations that have allowed our researchers to identify disparate infrastructure that had previously been flying under the radar.
Portions of this infrastructure have been used by thousands of Cobalt Strike “Beacons” and malicious document stagers across several distinct malspam campaigns. In more recent offensives, such as the Fake Kaseya VSA phishing campaign first reported by Trustwave in early July, the team server infrastructure was used for staging further Dridex payloads.
Prior to deployment, the beacon payloads associated with TA575 team servers tend to be packed using CryptOne and signed using one of several self-signed code-signing certificates. The internal filenames within the version information are either Mightywill.QA.CrashReport.exe or simply Opera. BlackBerry researchers have observed thousands of beacon loaders packaged in this manner, usually dropped as part of malicious document attack chains. They are related to several distinct campaigns targeting healthcare, government, and legal verticals in the U.S.
Further unravelling of the network infrastructure has proved invaluable for tracking campaigns, as they yield domain names for associated IPs that are registered in advance of deployment (via DGA). They also provide indicators that can be used to fine-tune our threat detection capabilities.
We are sharing this intelligence with the community because many of TA575’s Cobalt Strike team servers remain unattributed, and several have yet to be fully operationalized. Furthermore, since not all team servers are being used for high-profile Dridex or Qakbot phishing campaigns, the association between Cobalt Strike Beacon and TA575 may not always be immediately apparent during investigations.
We hope that the insights and indicators in this report may prove beneficial to analysts, researchers, and investigators in providing attribution as well as correlation with past and present TA575 Cobalt Strike activity.
The following information is presented as a timeline of this threat actor’s activities and expansion of its malicious use of Cobalt Strike Beacons.
February 2021 – Qakbot
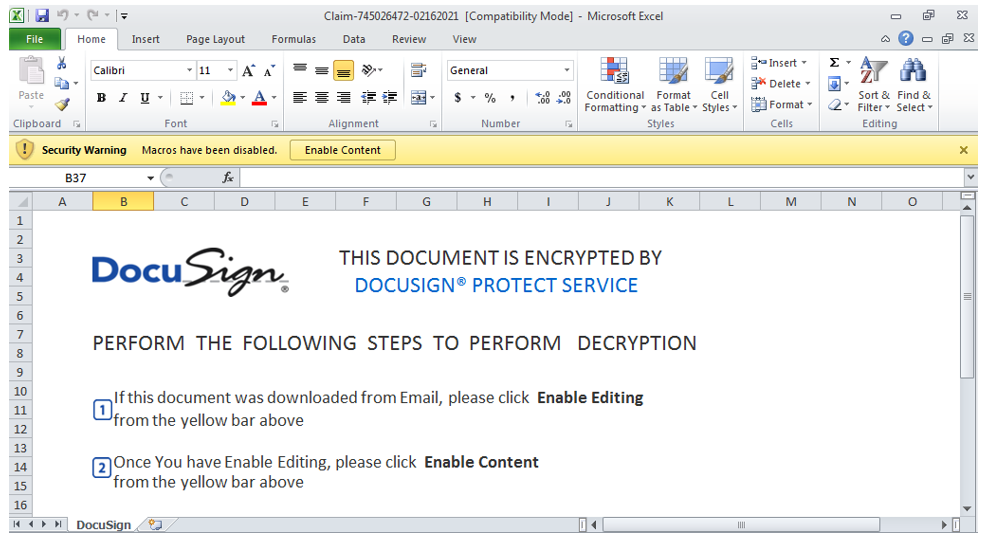
The first campaign to leverage the team server infrastructure began in late February. It was ultimately responsible for deploying Qakbot in a targeted attack against healthcare, municipal county offices and law firms in the U.S. The phishing emails contained malicious document attachments that would display a convincing DocuSign-based lure when opened.
This lure was designed to trick the recipient into enabling macros, as shown in the image below. Once activated, the macro-enabled documents would deploy Beacon and Qakbot payloads via an MSHTA attack chain.
Figure 1: DocuSign phishing lure used to deliver Cobalt Strike/Qakbot
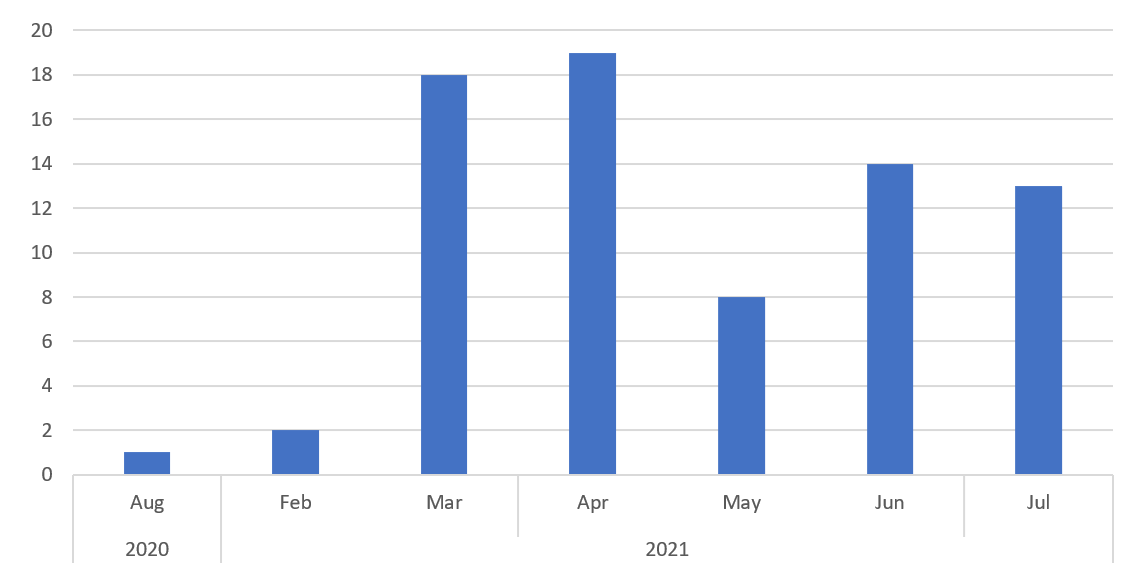
Owing to the effectiveness of this campaign, TA575 apparently decided to broaden its team server infrastructure for subsequent campaigns, deploying nearly 20 servers a month after the Qakbot campaign. The deployment rate tailed off slightly in May, picking up again from June onwards. These additional servers were used to underpin a new Dridex phishing campaign that began in early July and continued into early August.
Figure 2: TA575 Cobalt Strike team server deployments by month (tracking unique IP/ports)
Notably, a single team server was deployed as far back as August 2020, when TA575 conducted a prior Dridex campaign. However, the cyber-criminal group seems to have favored the now-defunct PowerShell Empire post-exploitation framework at the time, and did not deploy related team servers again until the Qakbot campaign in late February.
July 2021 – Dridex
Starting in early July 2021, TA575 deployed a fresh batch of team servers and began hosting Dridex and maldocs alongside Cobalt Strike Beacons. This occurred while phishing campaigns were again targeting healthcare and municipal county offices in the US, as well as broader targets across South Korea. Around this time, a mass spam campaign pumping fake Kaseya VSA phishing lures was observed by Trustwave and Malwarebytes, containing attachments embedded with CryptOne-packed Cobalt Strike Beacon loaders.
BlackBerry researchers discovered that many of the loaders were signed using a self-signed certificate named MZJVESLENZVLRPQFZD, with an internal filename of Mightywill.QA.CrashReport.exe. These loaders were configured to communicate with recently deployed team servers already under observation.
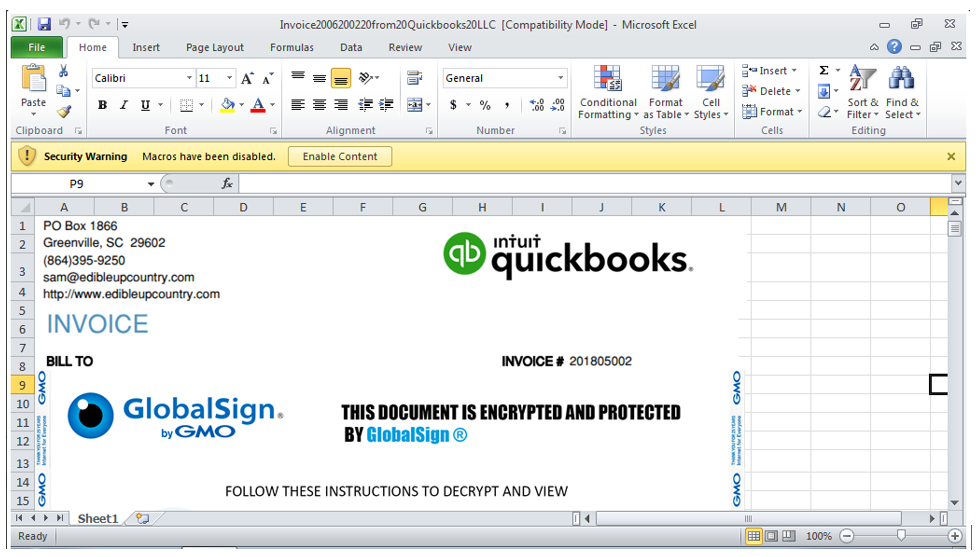
In addition, malicious Excel® documents were found to be using GlobalSign by GMO and QuickBooks lures to dupe targets into enabling macros. Using filenames such as Invoice_891042.xls, zbetcheckin_tracker_Invoice_952068.xls and Reciept 19129475.xlsb (sic), the maldocs dropped CryptOne-packed Beacon loaders, Dridex, and VBA downloaders used as part of an MSHTA attack chain.
Several examples of the document lures are presented below:
Figure 3: GlobalSign by GMO/QuickBooks lure
Figure 4: GlobalSign by GMO lure
Figure 5: Other maldoc lures from the same campaign used a fake “Microsoft Document Protection” ruse
August 2021 – Dridex
TA575’s Dridex campaign has continued throughout the summer of 2021. While the emails, documents, lures, Dridex command and control (C2) channels, and domains have all changed, the core team server infrastructure underpinning their activities remains the same.
The latest maldocs are typically named Scan_84532.docx or Document_31584.docx. They use Office 365-related lures to socially engineer victims into enabling macros, as seen here:
Figure 6: Office 365 lure
Using Office 365 phishing domains to enhance the ploy, URLs on these domains ultimately yield Dridex payloads:
- documents365updates.com
- azure365documents.com
The Emotet Connection
Further hunting has revealed historical overlaps between a code-signing certificate and an Emotet campaign that began during late March 2019. The Emotet samples were signed using a certificate named FNXAUGHC, packed using CryptOne, and they used Mightywill.QA.CrashReport.exe as the internal filename.
The reason for this connection remains unclear, but we would speculate that the certificates and filenames are indicative of a pre-distribution packaging system, perhaps operated by distributors and other affiliates more closely involved with the deployment phase of these malicious campaigns.
We also have gathered historical evidence showing that the 2019 Emotet campaign was targeting a variety of organizations including municipal county offices, MSSPs, and Fortune 200 companies in the U.S.
Findings
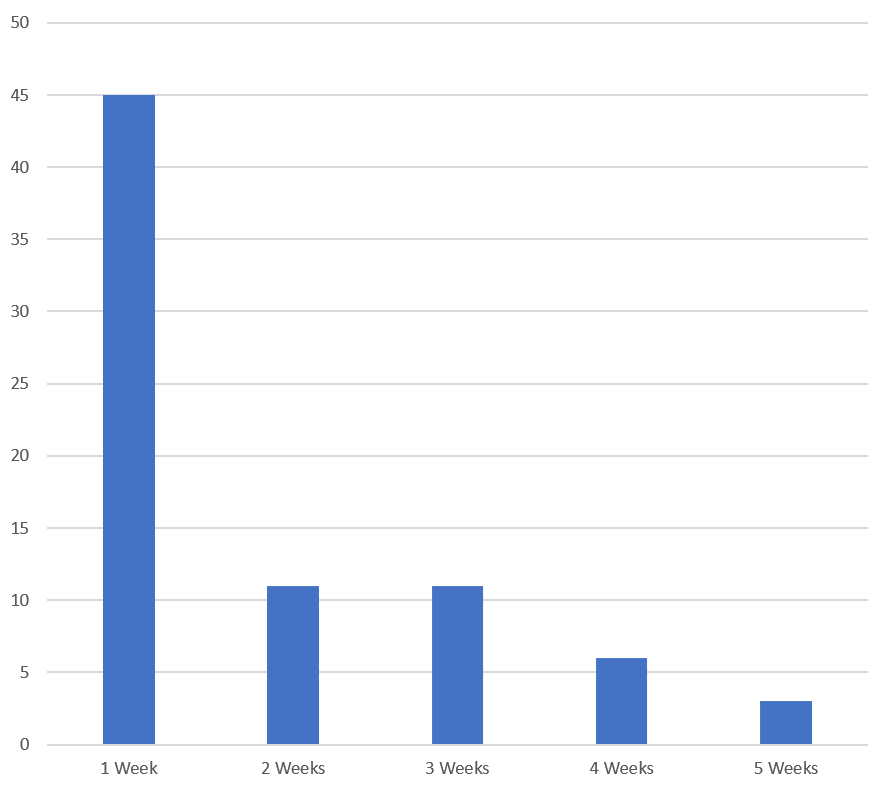
Monitoring TA575’s Cobalt Strike team server infrastructure has given us great insight into their malspam campaigns throughout 2021. Overall, BlackBerry has observed an increased frequency in deployment of Cobalt Strike team servers. In addition, the average operational lifespan of these team servers increased to several weeks. As they are able to stay active for longer, Cobalt Strike is becoming more popular with TA575, both for deployment of payloads and subsequent lateral movement in networks. The threat actors appear to be phasing out PowerShell Empire, which was their post-exploitation framework of choice until early 2021.
Figure 7: TA575 Cobalt Strike team server lifespan
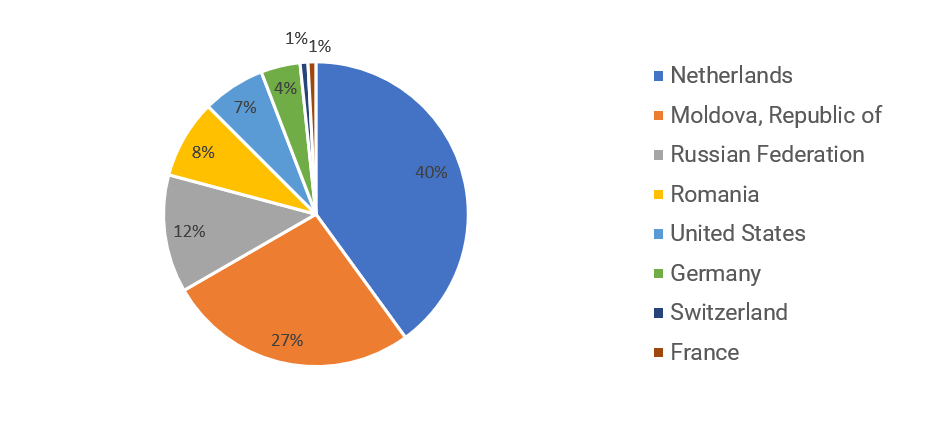
87% of the TA575 team servers we observed are hosted on netblocks in the Netherlands, Moldova, Russia, and Romania. The remaining 13% of servers were deployed throughout the U.S., Germany, Switzerland, and France.
Figure 8: TA575 team servers deployed throughout the world
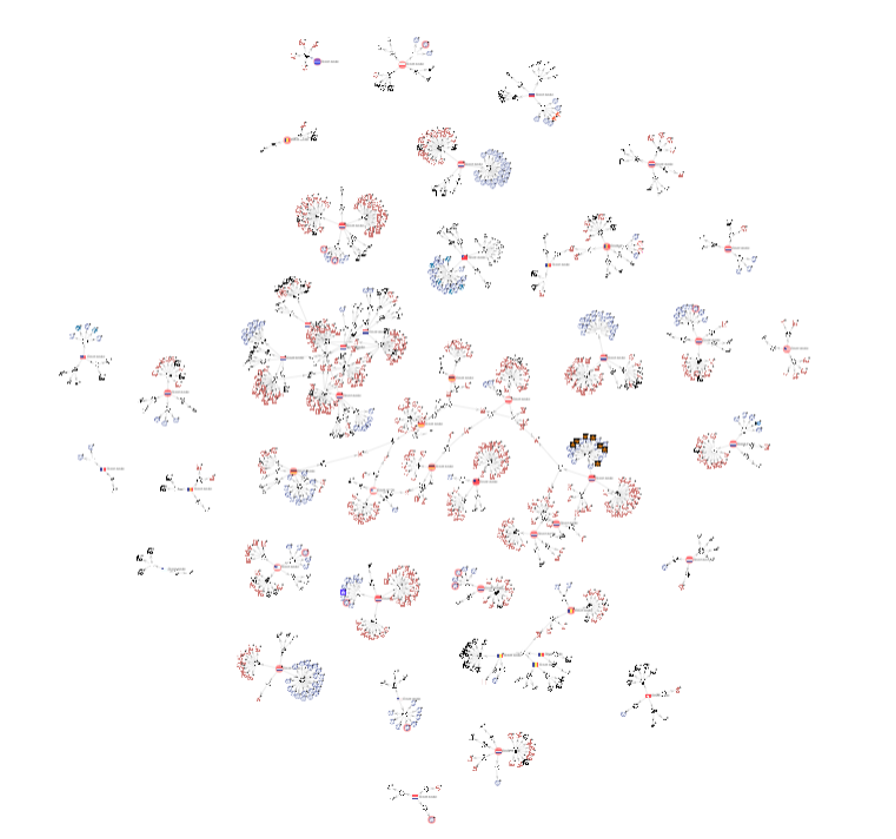
As we pivoted on the team server infrastructure to perform further hunting and correlation, we revealed a vast web of TA575 phishing lures, maldocs, and CryptOne-packed Beacon loaders, as well as final-stage payloads such as Dridex, Qakbot, and Emotet.
Figure 9: Team server VT graph, showing a web of TA575 phishing lures, maldocs, and CryptOne-packed Beacon loaders
Indicators of Compromise (IoCs)
While we will continue to leverage this intelligence to monitor for new campaigns and Cobalt Strike team server infrastructure related to TA575, we have amassed a vast quantity of indicators that we are happy to share with the community.
A small number of the indicators are historical and are included only to highlight connections. Overall, we have collected over a 1,000 high-confidence indicators to share with law enforcement and the threat intelligence community.
A full list of IoCs is available on our GitHub here: https://github.com/blackberry/threat-research-and-intelligence/blob/main/TA575-Dridex.csv
Infrastructure
- Over 50 team server IP addresses
- 12 new Dridex C2 servers (from 4 distinct configurations)
- Hundreds of Dridex phishing/maldoc domains
SHA256
- Over 60 new Dridex samples since July 2021
- Hundreds of Cobalt Strike Beacons
- Hundreds of CryptOne Beacon loaders
- Qakbot loaders from February 2021
Filenames/Command-Lines
- Maldocs
- Dridex
- Loaders and stagers
Certificates
- 5 certificates used for signing CryptOne Cobalt Strike Beacon loaders
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry blog.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.