Threat Thursday: BlackMatter RaaS - Darker Than DarkSide?
First identified in July 2021, BlackMatter is a new player in the Ransomware-as-as-Service (RaaS) arena that many researchers have dubbed the successor to the recently retired Russian ransomware gang DarkSide. However, a spokesperson for BlackMatter insists they are not the same operators.
BlackMatter has recently made headlines as the likely culprit behind cybersecurity incidents affecting a major medical technology company and a U.S. farming cooperative.
Operating System
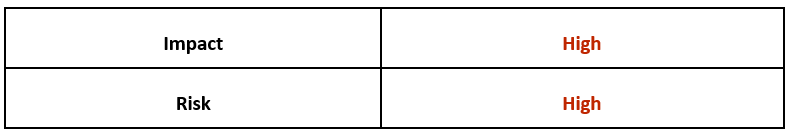
Risk & Impact
About the BlackMatter Group
BlackMatter has been advertised on Russian underground forums, such as XSS and Exploit, looking to recruit affiliates. They claim to have adopted the “best” attributes of DarkSide, REvil and LockBit.
Although these underground forums are among those that have banned ransomware advertisements in the wake of the ransom attack on Colonial Pipeline in May 2021, BlackMatter circumvented this restriction by advertising for “initial access brokers.” These brokers are criminal groups that have gained access to corporate networks or machines.
In their posts, BlackMatter offers a payment of up to $100,000 USD. They state they are looking for access to corporate networks in English-speaking countries, with targets that have between 500 and 1500 hosts and a revenue of over $100M.
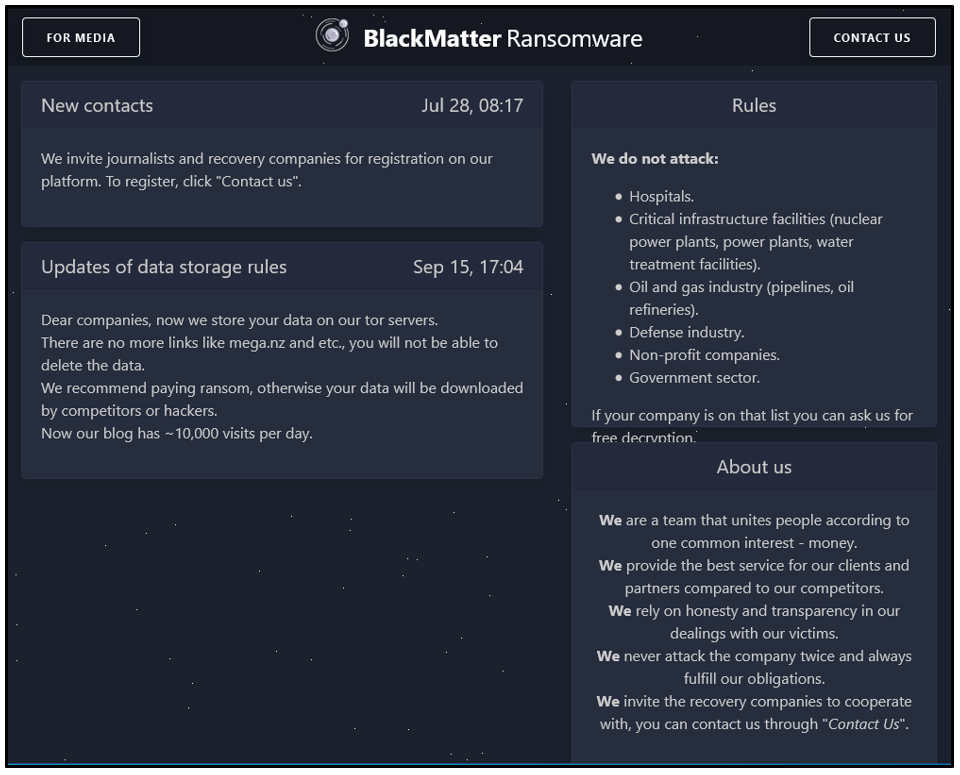
The BlackMatter website provides information about the group and even its motivations. The RaaS provider says it aims to fill a void in the market left by DarkSide and REvil pausing their activities. The group’s advertising promotes the strengths of its malware to compete with existing offerings, presumably to attract the most successful affiliates.
On their blog site, BlackMatter includes a list of rules defining sectors they do not attack; they claim to offer free decryption to any victims in these sectors. This is most likely an attempt to avoid the backlash suffered by REvil, Conti, and DarkSide in targeting such industries during 2021.
Unlike DarkSide and REvil, BlackMatter does not include any checks to ensure victims in certain geolocations are not encrypted. BlackMatter will encrypt Russian systems, which may be another way they’re trying to distinguish themselves from other threat groups.
Figure 1: BlackMatter "About" information
Technical Analysis
Since July there have already been several versions and updates of BlackMatter identified. These include versions 1.2, 1.6, 1.9 & 2.0. Additionally, a Linux® variant is available.
Statically analyzing a recent sample identifies the file as a Windows® 32-bit executable with a compile stamp from the Aug. 16, 2021. The file includes a .rsrc section, although the binary contains no resources. This section is instead where the encoded configuration information is stored. The sample reviewed is a BlackMatter variant version 2.0.
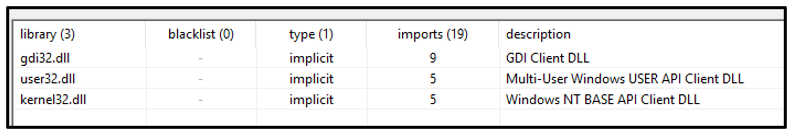
The binary uses only three libraries, and its import table contains a short list of Application Programming Interfaces (APIs).
Figure 2: Static analysis of the file's imported libraries
BlackMatter employs various methods to help evade detection and hinder researchers. For example, most of the APIs and important strings are obfuscated. The executable will de-obfuscate these during runtime as required. Although this approach is common with threat actors, the way it is implemented by BlackMatter is very similar to the functionality found in DarkSide.
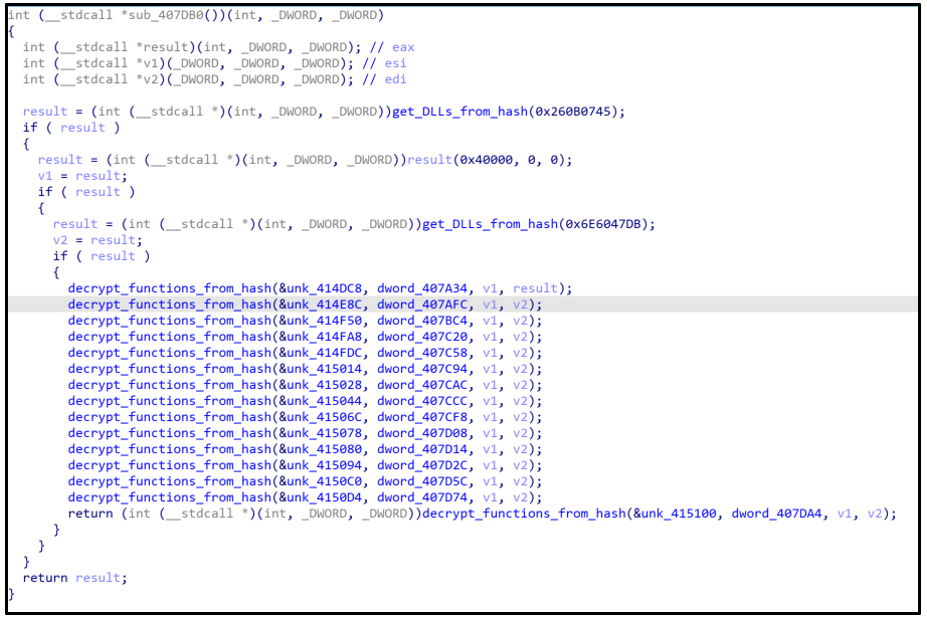
Directly after the file’s entry point, the binary resolves the addresses of the APIs it requires when executing. The function shown in the image below dynamically loads additional libraries and APIs.
Figure 3: Function to resolve APIs and functions
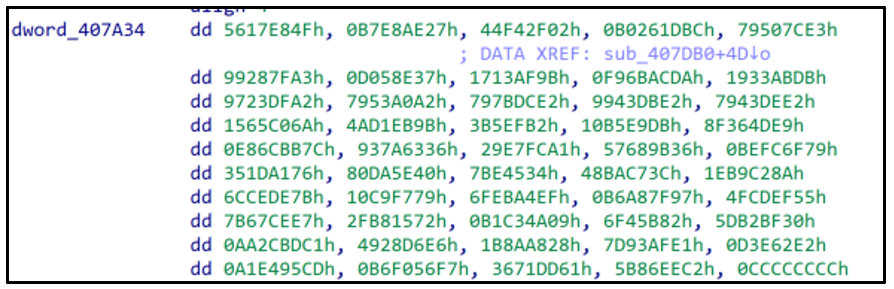
The DWORD values point to blocks of encrypted hashes for each API, followed by a trailing 0xCCCCCCCC. Each hash is decrypted by an XOR operation.
Figure 4: Block of encrypted hashes
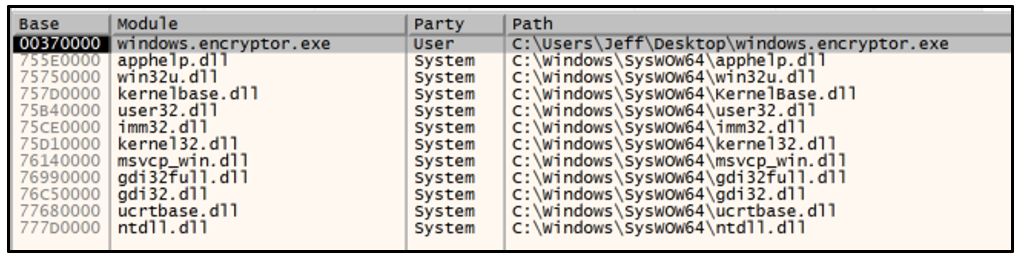
The image below illustrates the libraries loaded before execution of the function sub_407DB0.
Figure 5: DLLs loaded before function has executed
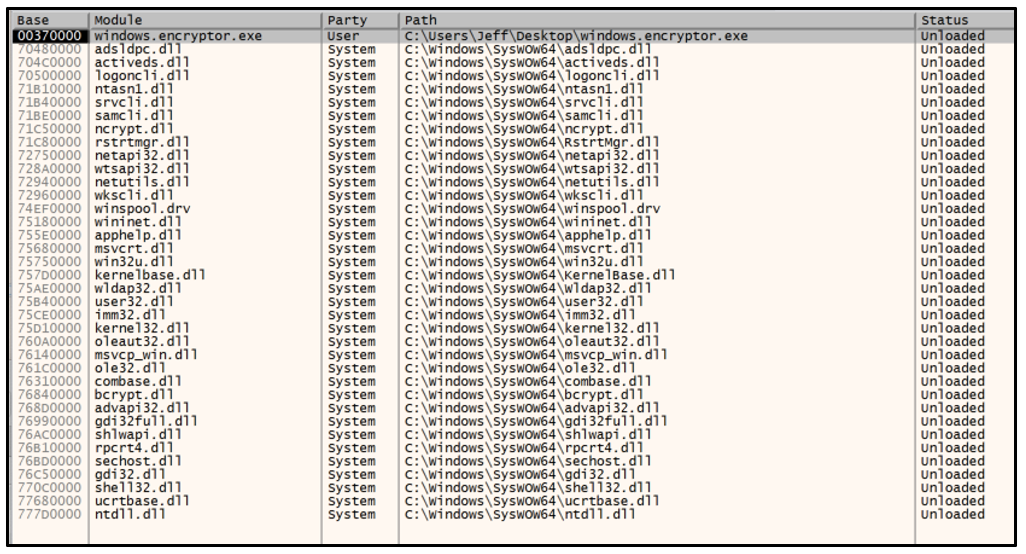
The following image illustrates the DLLs loaded into memory after the function to resolve APIs has executed.
Figure 6: DLLs loaded after the function has executed
BlackMatter also employs anti-debugging techniques to hide threads from the debugger, which makes it trickier to analyze. If it is analyzed while running under a debugger, the application will crash.
The binary accepts command line arguments when executed. If no argument is supplied, its default action is to first verify the rights of the current user. If required, it will attempt to elevate privileges and bypass User Account Control (UAC).
The malware creates a mutex to ensure that only one instance of the ransomware is running. The mutex name is generated from a registry value relating to the MachineGuid; for example, “Global\21661c2e54b253e217f64acc8644f973”.
The executable deletes three services relating to shadow copies – “vmicvss,” “vmvss” and “vss.” Removing shadow copies is a common practice with ransomware, as it prevents victims from easily restoring their systems.
BlackMatter will terminate common productivity-related processes to increase its impact. Terminating these processes ensures that important files will not be locked, and valuable files can be encrypted.
The ransomware takes a multithreaded approach to enumerating the filesystem and executing the encryption routine, to ensure that files are locked quickly. Local files and any found on connected drives will be encrypted, while vital system files are skipped.
The BlackMatter encryption routine shares similarities with that of DarkSide. It uses custom implementations of the Salsa20 and RSA-1024 algorithms. Only the first megabyte of each file is encrypted, and the encrypted key is added to the end of the file. Partially encrypting files makes the process much faster, which shortens the attack duration and leaves little time for the victim to react.
Encrypted files are appended with an extension consisting of an alpha-numeric string that varies between attacks. Below is an example of an encrypted filename.
Figure 7: Encrypted file with appended extension “.3LqOKCiOu”
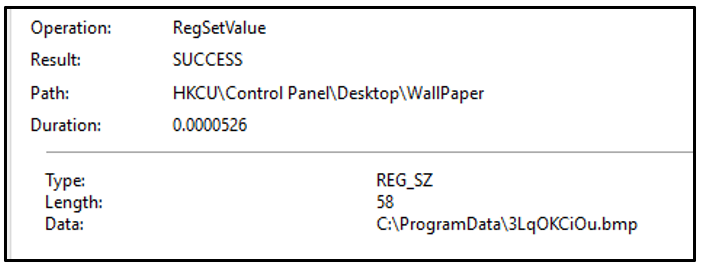
The ransomware drops a bitmap image file to C:\ProgramData\ and sets this as the victim’s background through the registry.
Figure 8: Defining wallpaper image in the registry - 3LqOKCiOu.bmp
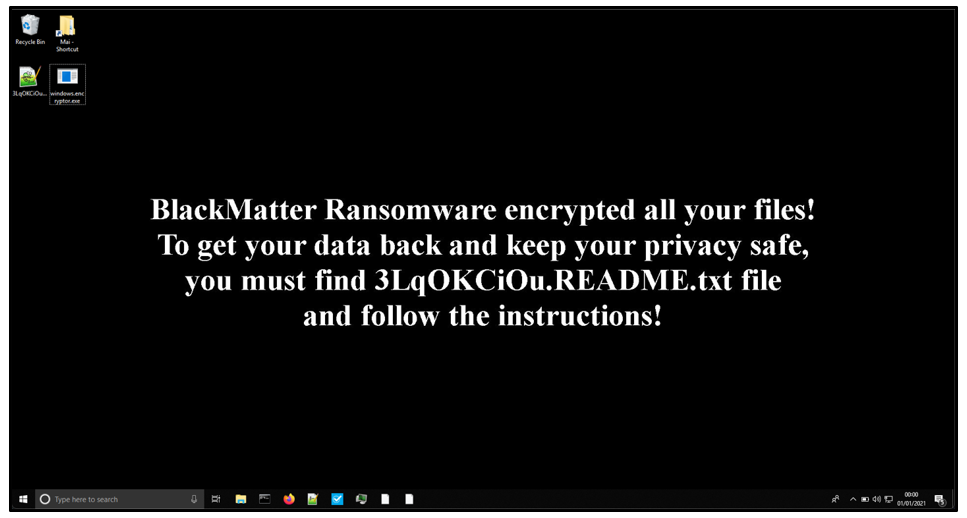
The wallpaper notifies the user their files have been encrypted by BlackMatter. The image itself appears very similar to the one used by DarkSide.
Figure 9: Desktop wallpaper of an infected endpoint
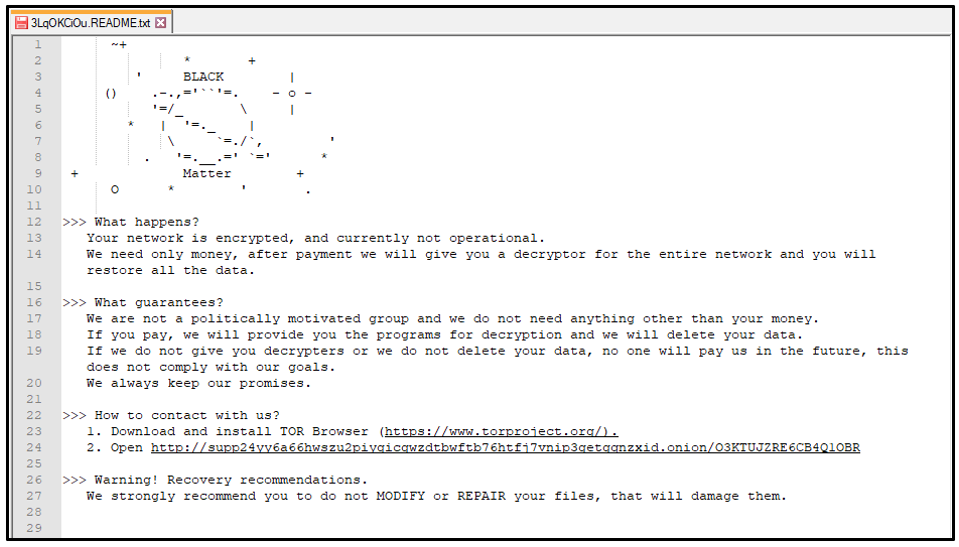
A ransom note is also dropped into each directory as a text file. This text file is named using the same extension as the encrypted files, appended with README.txt. For example, “3LqOKCiOu.README.txt.”
Figure 10: BlackMatter ransom note
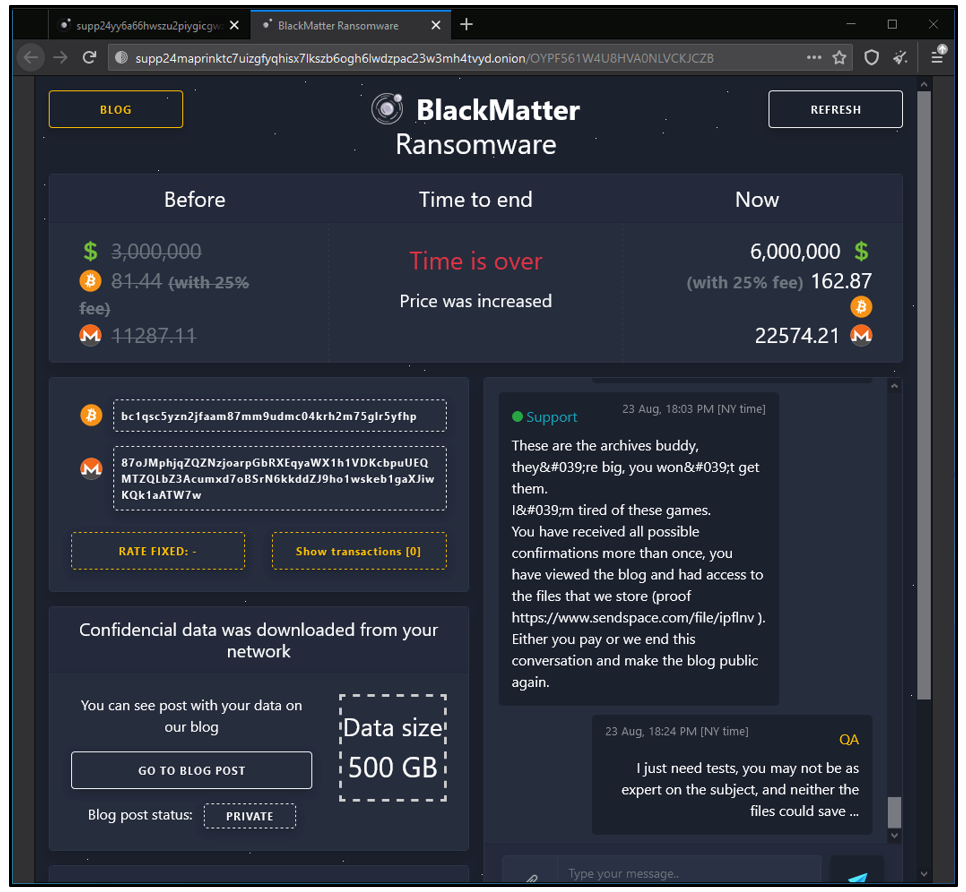
The ransom note provides the URL of an onion website (one accessible via TOR) where the victim can pay if they wish to obtain the decryptor for their network.
Figure 11: BlackMatter payment website
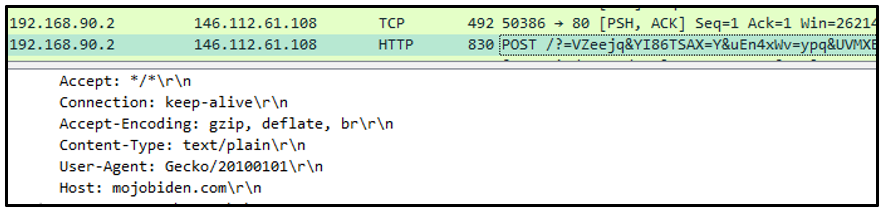
The malware collects information from the victim’s machine and sends this data to its command-and-control (C2) servers in an encoded POST request. During our analysis, the sample in question communicated with http[s]://mojobiden[.]com and http[s]://nowautomation[.]com.
Figure 12: POST request to C2
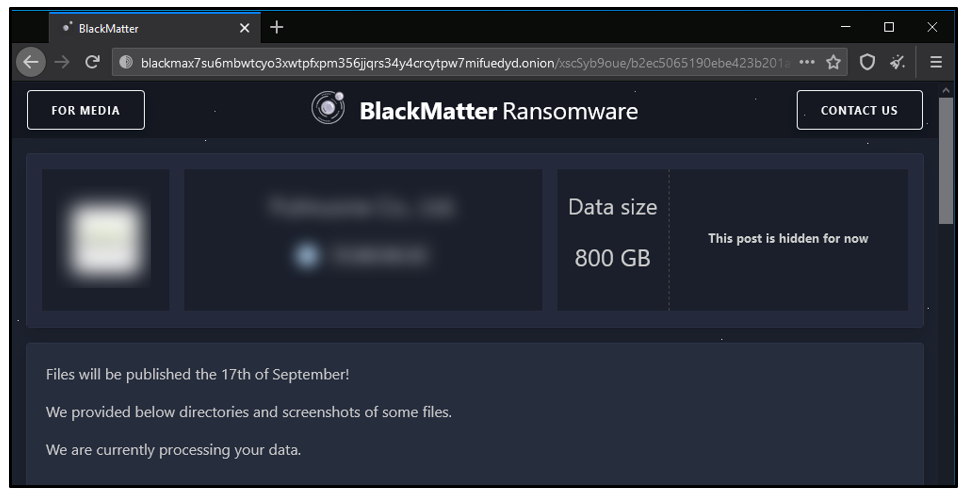
Like most modern RaaS providers, BlackMatter uses the technique of double extortion. A leak site is available on the dark net. Victims are threatened that their confidential data will be released publicly if they choose not to pay.
Figure 13: BlackMatter leak site
YARA Rule
The following YARA rule was authored by the BlackBerry Research & Intelligence Team to catch the threat described in this document:
import "pe"
import "hash"
rule Mal_Win_Ransom_BlackMatter {
meta:
description = "BlackMatter Ransomware September 2021"
author = "BlackBerry Threat Research Team"
date = "2021-09"
condition:
pe.is_32bit() and
filesize < 90KB and
filesize > 60KB and
pe.number_of_imports == 3 and
pe.imphash() == "2e4ae81fc349a1616df79a6f5499743f" and
hash.md5(pe.sections[0].raw_data_offset, pe.sections[0].raw_data_size) == "100da8cf342d6d8f3bd24b367e0ea999" and
pe.sections[3].name == ".rsrc" and
pe.number_of_signatures == 0 and
pe.number_of_sections == 5
}
|
Indicators of Compromise (IoCs)
Files Dropped:
C:\ProgramData\<alpha-numeric_extension>.bmp
e.g.: C:\ProgramData\3LqOKCiOu. Bmp
Mutex
Global\<alpha-numeric_string>
e.g.: Global\21661c2e54b253e217f64acc8644f973
Services Terminated
Vmicvss
Vmvss
Vss
Encrypted Files:
<filename>.<alpha-numeric_extension>
e.g.: test.jpg.3LqOKCiOu
Ransom note:
< alpha-numeric_extension >.README.txt
e.g.: 3LqOKCiOu.README.txt
CnC Servers:
http[s]://mojobiden[.]com
http[s]://nowautomation[.]com
Payment URL:
hxxp://supp24yy6a66hwszu2piygicgwzdtbwftb76htfj7vnip3getgqnzxid.onion/O3KTUJZRE6CB4Q1OBR
|
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you by providing around-the-clock support, if required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
Want to learn more about this threat? Watch our new demo video: BlackBerry vs. BlackMatter RaaS.
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.