ZingoStealer is infostealer malware that uses the appeal of “free” software to attract both predators and prey. This infostealer was first spotted in March 2022 being distributed by the Russian threat group, “Haskers Gang.” A YouTube video, uploaded on March 4 by the Haskers Gang, presents the infostealer as free to the threat actor’s “members,” and distributed through the Ginzo Telegram channel. ZingoStealer targets Windows® systems. For $3, an alternate version of this threat is available that contains “ExoCrypt” crypter, to help it evade antivirus (AV) detection.
The offer to obtain the infostealer free of charge has led to a dramatic increase in its adoption. Home users seem to be the primary victim of this threat. ZingoStealer lures its victims with the promise of “free” software, as it disguises itself as an access point for “cracked” versions of popular videogames and programs.
Once ZingoStealer gains access to a system, it steals sensitive user data such as login credentials and cryptocurrency. This information is exfiltrated back to the command-and-control (C2) server and used by the attackers for financial gain. Other threat actors who adopt this infostealer may also be getting “ripped off” by this free offer, as the original authors of Zingostealer retain access to all data stolen by their clients, and could profit from it before their clientele.
ZingoStealer is potentially more dangerous than many of its fellow infostealers because it can deliver additional malicious payloads to victims’ machines. For example, the threat has been observed dropping cryptominers such as XMRig and additional infostealers such as RedLine.
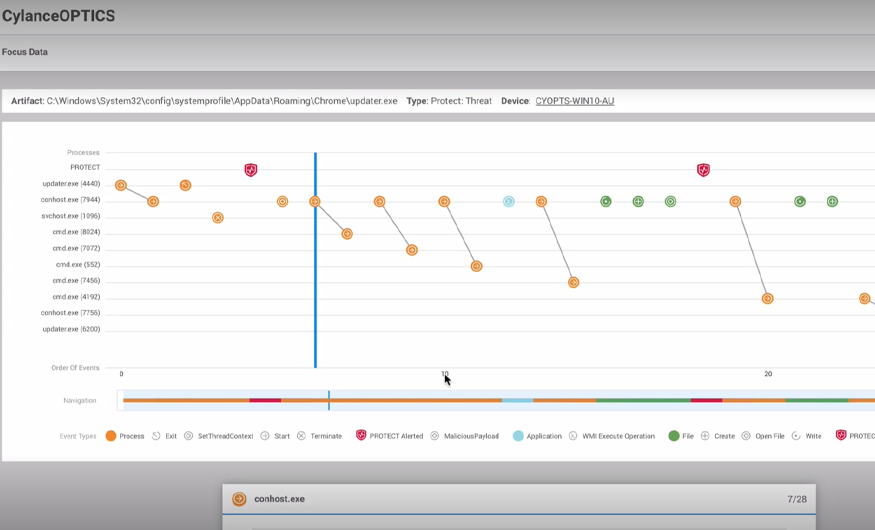
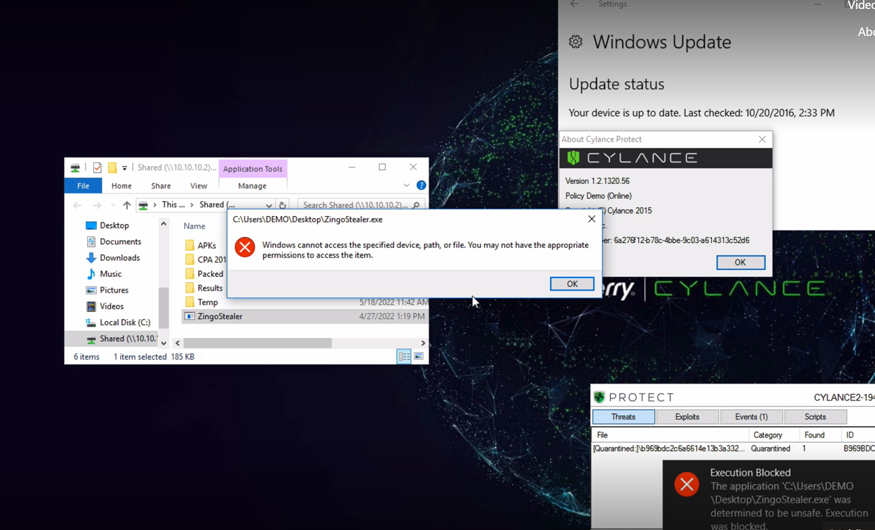
See how BlackBerry prevents ZingoStealer attacks in our latest demo video, which shows BlackBerry® products going head-to-head with a live sample of ZingoStealer.