Lessons From the Front Line: Threat Hunting
This article is the fifth in the series from the Blackberry Incident Response (IR) team (now with guest appearance from the BlackBerry® Guard team) examining critical behaviors that either stop incidents from happening or greatly reduce their impact.
The first four articles can be found here:
Insight
While it is understandable for organizations to want to rely on purchased security products to find all instances of evil in their environment, it is just not possible. Security technology must be paired with a human element that thinks like an attacker. This is especially true when implementing threat hunting. Those threat hunters should understand the cyber kill chain (mentioned in our proactive monitoring article) to know what to look for in each phase.
In fact, one might think of threat hunting as proactive monitoring on steroids—it is the next step in the evolution of shortening the time to detection. Hunting is the transformation of being purely reactive to becoming proactive in your detections.
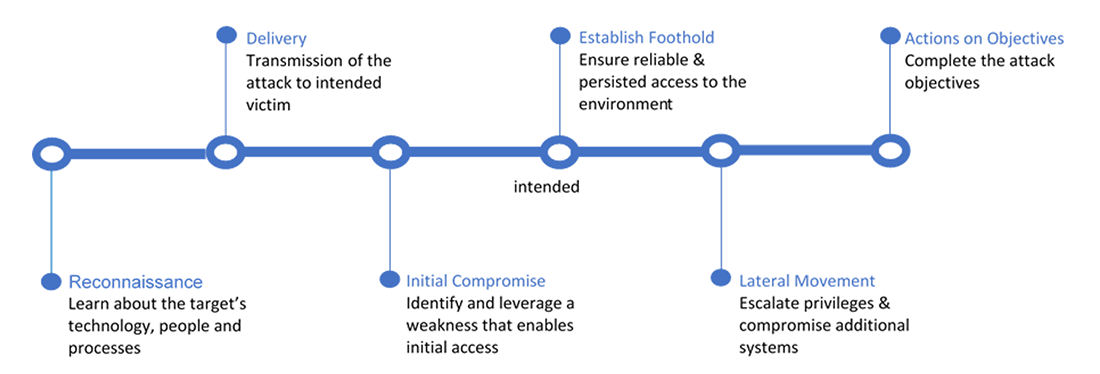
Figure 1: Cyber Kill chain showing stages that can be used to proactively sweep the environment for signs of compromise
Real-World Scenario
The BlackBerry Guard team spends their days on the constant hunt for signs of compromise within customer environments. This 24/7 service has discovered multiple instances of maliciousness, such as:
- Ursnif and Trickbot related fileless malware detected via a BlackBerry® Optics EDR behavioral rule watching for suspicious mshta usage. This malware maintained persistence via run keys in the Windows registry, which were set to run malicious code that was located elsewhere in the registry via mshta.exe.
- XMRig-based coinminer hiding out on a web server. This was identified via a BlackBerry Optics EDR rule designed to detect uncommon processes spawning cmd.exe. The process in this instance was the web server process. Another BlackBerry Optics EDR rule fired at the same time on the system, designed to detect suspicious file activity in the root of the ProgramData directory. This was part of the same malicious activity. Once confirming maliciousness, the BlackBerry® Threat Research and Intelligence team reverse engineered the malware to determine its full functionality and other Indicators of Compromise (IOCs) to use for further threat hunting.
Tips for Effective Threat Hunting
This may be one of the least adopted topics we have covered in this series, because it requires significant investment above and beyond keeping the lights on and basic block and tackle, so we hope this list can help organizations get started:
- Centralize multiple data feeds into a single system
- Correlate multiple data feeds into related events
- Augment data using threat intelligence feeds for easy wins
- Use statistical analysis (stacking) to identify anomalous activity
- Investigate the use of machine learning (ML) to identify further anomalies
- Gather and curate intelligence gained from your environment into a central repository. Use this to hunt for similar incidents in an automated fashion.
- Build additional sweeps for the following activity:
o Tools and tactics referenced in the Mitre Att&ck framework
o Commonly abused processes launching a command shell, such as:
• Web server processes (IIS, for instance)
• Microsoft Office applications
o File activity in commonly abused directories such as the root of ProgramData on Windows.
o Common network attacks such as connection attempts to port 3389 over a short period of time
- Curate experienced staff capable of keeping up with the latest attacker tactics, techniques, and procedures (TTPs) so they can continue to improve threat hunting efficacy.
While some organizations have the resources to provide this capability in-house, others may not. For those that do not, consider hiring a third party to augment your in-house capabilities. Organizations that are not able to invest in 24x7 threat hunting operations should consider periodic “Compromise Assessments” to identify past and ongoing compromises.
Conclusion
The investments made in security products are not wasted money; however, to get the most from those products and services, you need to combine them with humans who think like attackers. One such example is the threat hunting covered in this article.
We hope the tips provided will help you get started or at least know what to look for when enlisting the help of a third party MSSP that includes continuous threat hunting.