BlackBerry’s Cylance AI Prevents Terminator EDR Killer
A Russian-speaking threat actor going by the handle of Spyboy was recently reported to be selling an endpoint defense evasion tool that can allegedly “kill” every leading AV (antivirus), EDR (Endpoint Detection and Response) and XDR (Extended Detection and Response) product on the market.
The good news is that BlackBerry customers are protected by Cylance® AI from the Terminator EDR tool. Let’s take a look at the tool and discuss how organizations can protect themselves against it.
What’s the Story?
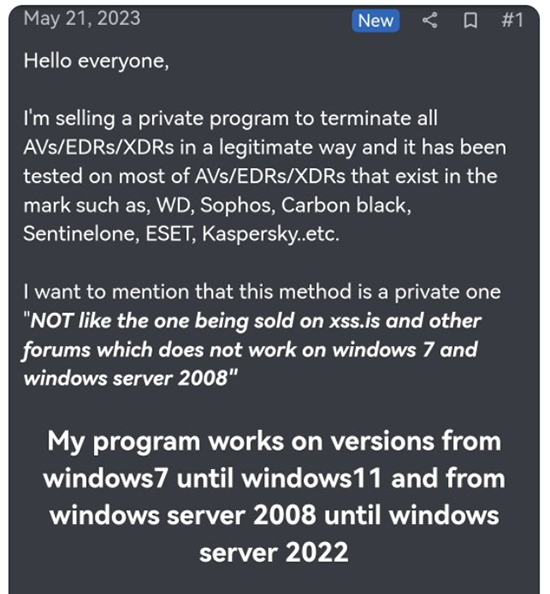
On May 21, a new threat actor calling themselves Spyboy shared details of an antivirus-killing tool on the Russian Anonymous Marketplace (RAMP) called Terminator EDR Killer. But rather than taking the user’s “clothes, boots, and motorcycle,” the author boasted that the Terminator tool was able to disable 23 AV/EDR/XDR products and controls, including products from Sophos, CrowdStrike, Kaspersky, McAfee, BitDefender, Malwarebytes, ESET, and more. Also included in the list was Windows Defender, on devices running Windows 7® and later.
At the time of writing, the price Spyboy charges for this tool ranges from USD$3000 for an “all-in-one bypass,” to USD$300 for “a specific AV/EDR/XDR.”
Figure 1 – Spyboy’s post, shared on Twitter (Source)
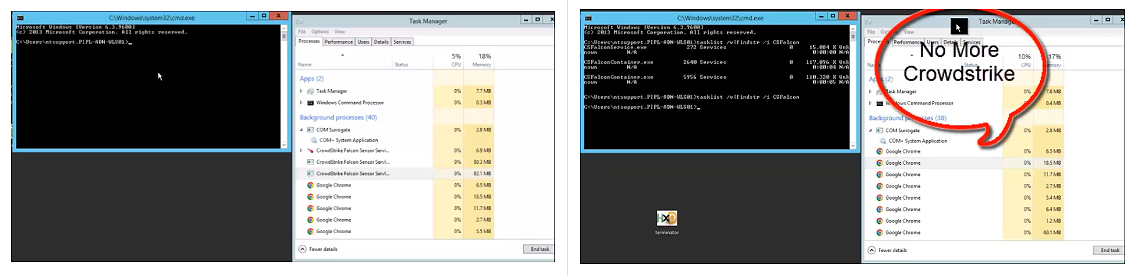
The threat actor also published demo videos allegedly showing the tool at work on Sophos and CrowdStrike solutions. A disclaimer noted that “Ransomware and lockers are not allowed and I’m not responsible for such actions.”
Figure 2 – Spyboy’s demo video showing CrowdStrike Falcon EDR allegedly being disabled by Terminator (Source)
Examining the Terminator EDR Killer
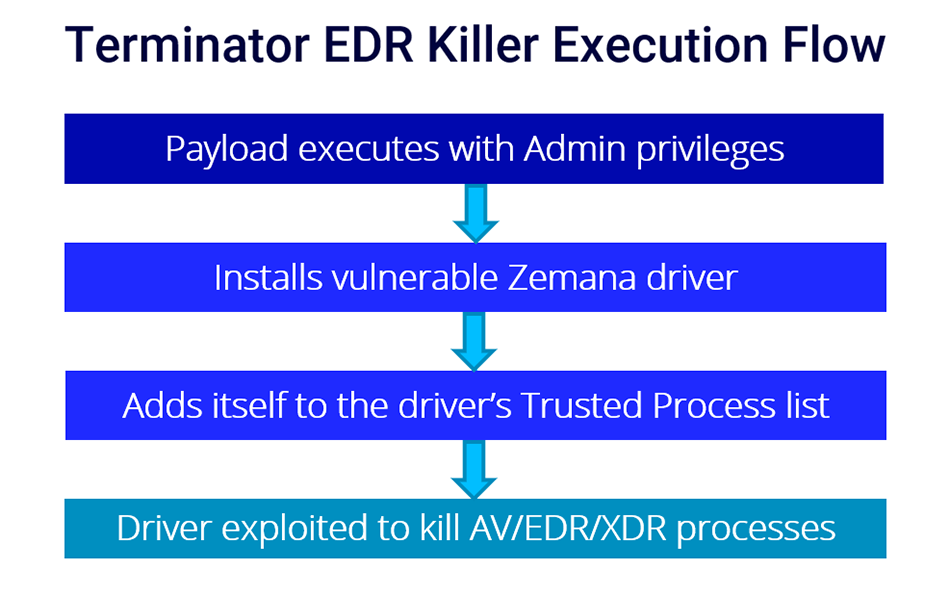
Spyboy’s Terminator tool relies on the Bring Your Own Vulnerable Driver (BYOVD) attack technique. This means that the tool deploys drivers that are legitimately signed and as such, may be loaded onto Windows systems to let attackers disable security solutions and take over the machine.
Research engineer Andrew Harris revealed in a Reddit post that Terminator specifically deploys and loads a vulnerable version of Zemana AntiMalware kernel driver, which is used to exploit a security vulnerability being tracked as “CVE-2021-31728.” The kernel driver is named zamguard64.sys or zam64.sys, and is signed by “Zemana Ltd.” It is dropped into the C:\Windows\System32\drivers\ folder, with a random name of four to 10 characters assigned to it.
After the vulnerable driver is written to the disk and the user has accepted the User Account Control (UAC) popup, the Terminator tool loads the driver and uses its kernel-level privileges to terminate security software processes, which are normally protected.
Use of BYOVD Techniques on the Rise
The BYOVD attack technique has increasingly been adopted by those with malicious intent, ranging from ransomware gangs to state-sponsored cyber-espionage outfits, such as the North Korean hacking group Lazarus. Established threat actors such as BlackByte utilize vulnerable drivers that give the attacker the ability to execute malicious code in kernel context. This elevates the aggressor to a privileged position within the system.
Harris notes in his Reddit post that “This technique is similar to other Bring Your Own Driver (BYOD) campaigns being used by threat actors over recent years.”
Remediation
So what can be done to ‘terminate’ the Terminator tool once it has already been dropped to the system? Dmitry Bestuzhev, BlackBerry Senior Director of Cyber Threat Intelligence, points out that the tool will not run by itself without manual action from the user. He notes that “The end-user must be a local administrator, and must also accept the UAC acceptance prompt.”
In terms of removal of the tool from the system, Bestuzhev advises: “If a user is an admin, it would be enough to simply uninstall the program through the "add/remove programs" feature in Windows, or through an official anti-malware uninstalling program.”
How can companies reduce risks associated with tools that claim to be able to disable anti-malware tools? Says Bestuzhev, “Users should have restricted user rights in the system. Company admins should enable device control to restrict usage of unwanted USB-like devices.” He also recommends that organizations enable self-protection features in their anti-malware products, so even though the tool may be downloaded by a user, either accidentally or with malicious intent, the antivirus solution will not be removed.
“Finally, visibility over endpoints is key,” says Bestuzhev. “Through events generated in the system and EDR/Sigma rules, it is always possible to detect malicious or suspicious activities and remediate them properly.”
We’ll continue to monitor this threat actor closely. Doubtless, they’ll be back.
BlackBerry Detection Provides Industry Leading AI-driven Defense
BlackBerry customers can rest easy knowing that our technology prevents the execution of Terminator EDR Killer. The Cylance® AI-driven defense model is a battle-proven solution that uses sophisticated algorithms that enable the system to detect and prevent threats before they have a chance to fully execute.
The use of AI is a highly effective and efficient approach to cybersecurity that is well-suited to the needs of modern organizations that must defend themselves from constantly emerging threats, such as Terminator EDR Killer.
CylanceOPTICS Rule
BlackBerry Threat Research has authored a custom CylanceOPTICS® rule (now part of CylanceENDPOINT™) to identify and mitigate techniques utilized by the Terminator tool. BlackBerry customers can access the following link through their accounts: https://support.blackberry.com/community/s/article/111050
For similar articles and news delivered straight to your inbox, subscribe to the BlackBerry Blog.
Related Reading: