BlackCat is bigger and badder than ever. ALPHV, the threat group behind BlackCat, recently introduced the option for other threat actors to subscribe to its Ransomware-as-a-Service (RaaS) offering, leading to the compromise of more than 60 entities worldwide at the time of this writing. The threat actor’s decision to offer its wares to affiliates not only enables it to increase revenue and build its reputation, but it also helps disguise the group’s presence.
By allowing other threat actors to use the ransomware as a service, the malware’s presence is no longer a good indicator of a direct attack from ALPHV. Any number of the threat group’s customers could be on a victim’s machine, operating the attack.
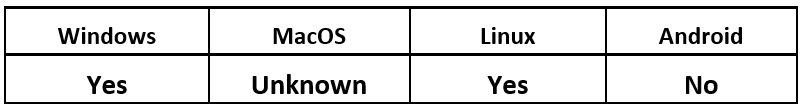
The new RaaS version of BlackCat has a lot to offer potential affiliates. Being based on the programming language Rust, it allows the threat operator to have one code base that can be used on many different operating systems, as their needs require.
Operating System
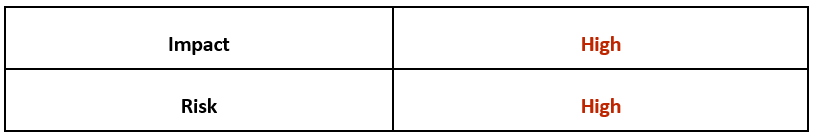
Risk & Impact
Technical Analysis
BlackCat ransomware is a tool that appears to be part of the final stage of ALPHV hacking campaigns, designed to extract as much value as possible from victims. With the release of this tool, the hacking group has joined the malware trend of both exfiltrating and encrypting files for ransom, conducting what’s become known as a “double extortion” attack.
However, victims are not the only potential revenue stream for threat groups. Cybercriminals who utilize malware such as BlackCat are themselves a potentially significant source of profit to the malware authors.
BlackMatter and DarkSide Get Rust-y
It’s likely that BlackCat has drawn inspiration from better-known threat groups, such as BlackMatter and DarkSide. Members of ALPHV have even gone on record to say that they are connected with these threat groups. They state that the new group has “borrowed their advantages and eliminated their disadvantages.”
An argument could be made that this new threat is in fact a “Rust-ification” of the earlier malicious programs – updating the previous threats using the Rust language – as BlackCat includes many of the same features, processes, and exclusions seen in those earlier programs.
For example, the BlackCat ransomware provides many standard behaviors and processes that have become accepted as standard ransomware fare, such as the following:
- Implementing AES or CHACHA20 for encryption
- Clearing of Windows Event logs
- Automatic deletion of shadow copies
A Shiny, Custom Paint-Job
Where BlackCat really shines is in its highly customizable design. It offers a wide variety of options that can be configured to the particular threat actor or victim, as the situation requires.
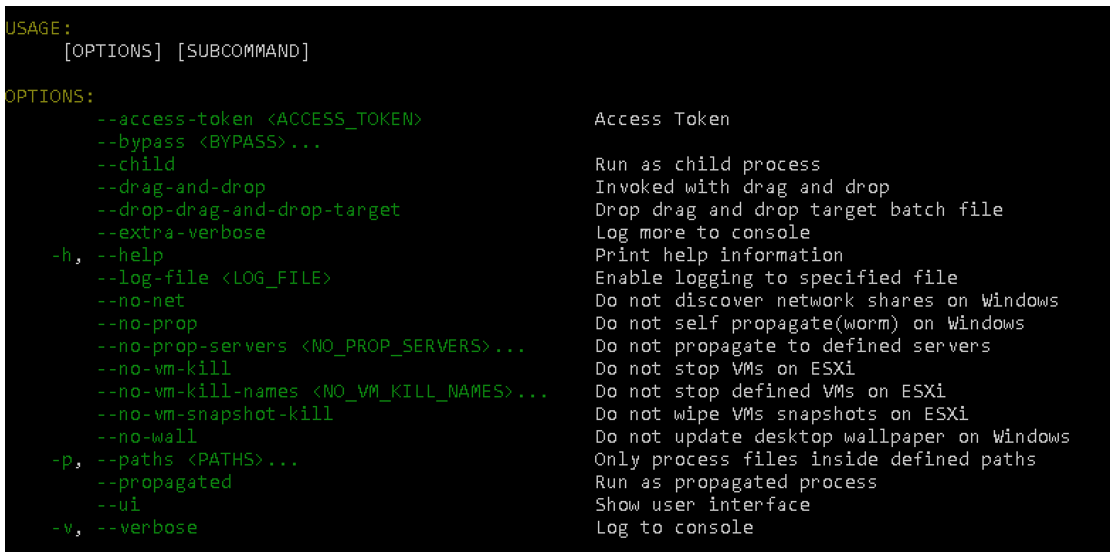
A threat operator can easily change the malware’s capabilities, such as changing the process it uses to run. For example, an attacker can choose to call its malicious process as a child process of another process of their choosing, or it can be called via the dragging and dropping of a batch file.
Attackers can also reduce the amount of “noise” they create on an affected system by selectively choosing details like which folders are encrypted, or whether to display a desktop ransom notice. This could leave the victim unaware of the damage that has been done for a longer time. Some of these options are configured in the binary builder, and some are changed at run time, which would allow attackers to customize on-the-fly.
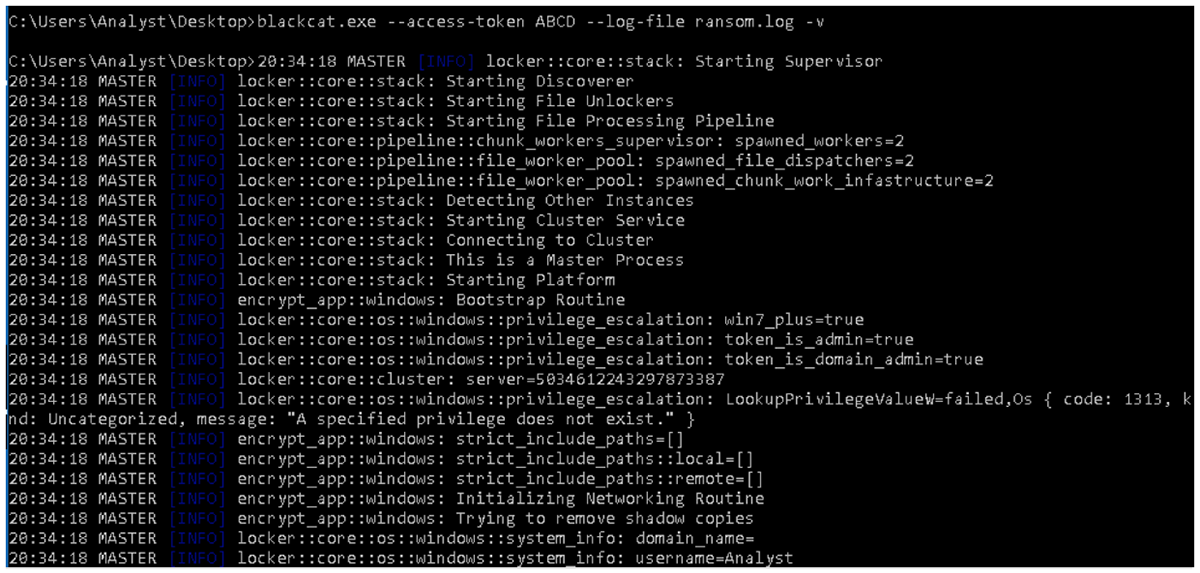
Figure 1: Run time config options
Options in the builder also allow clients to produce custom file extensions and ransom notes. They can also denote which file types to skip, which services and processes to kill, and much more. Further, credentials – either purchased or gathered in an earlier stage – can be provided such that the malware can leverage the popular tool “PsExec” to attempt to perform lateral movement throughout the victim’s network.
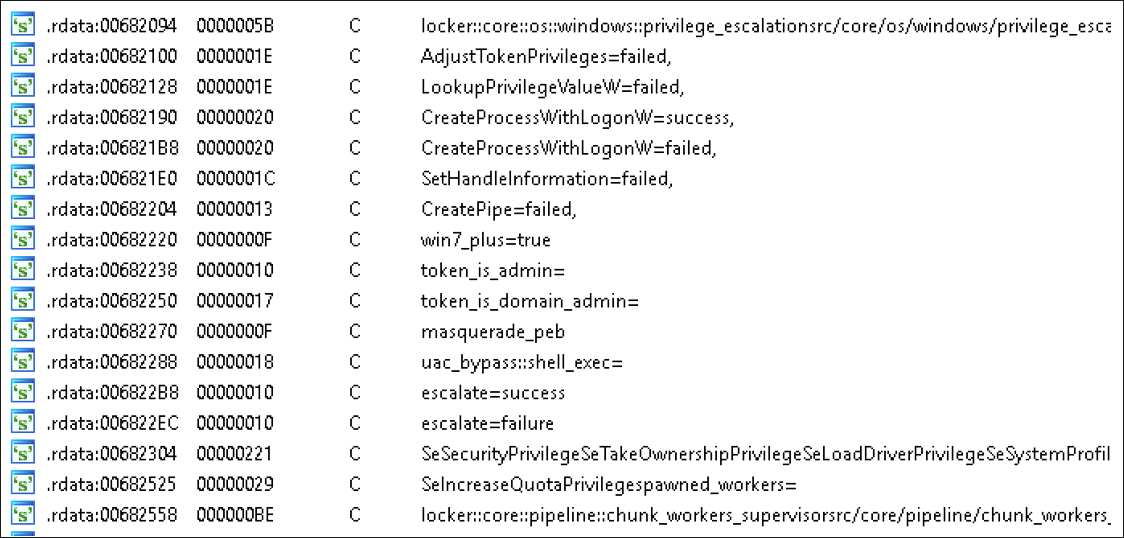
Security bypasses used for privilege escalation can be chosen at will, and include:
Figure 2: Bypass option strings
There is a configuration file that is embedded into the binary when it’s built, which includes even more options for affiliates. Configuration categories include the following:
Victim configuration ID
|
Include encryption paths that override exclusion settings
|
Change the desktop wallpaper to show a ransom note
|
Set default file encryption mode (full, fast, dot pattern)
|
Enable killing ESXi VM snapshots
|
Set default file cipher
|
Set a list of processes to kill
|
Exclude certain file extensions
|
Set a list of services to kill
|
Exclude directory names
|
Enable killing ESXi VMs
|
Set credentials to pass for lateral infection
|
Exclude a file path by wildcard
|
Enable self-propagation
|
Name the ransom note file
|
Set file names to be excluded
|
Choose the public key used for encryption
|
Choose an extension to append to files
|
Enable network discovery
|
Exclude ESXi VMs from being killed
|
Set a short note for text on wallpaper
|
Beneath the Shiny Exterior
All this configurability gives BlackCat a lot of power. We’ve discussed how this can be used for financial gain, but it could also be used for other types of destructive attacks.
While this threat has configuration options that allow affiliates to exclude files, folders, and extensions, if the threat operator chooses to omit all of these exclusions, they would suddenly have a very different sort of malware on their hands. Without skipping critical system files, this would lead to an execution path that would fully encrypt the victim’s entire disk, thus making it a wiper rather than ransomware.
This inclusion of wiper functionality could be an attempt by the threat’s authors to widen their potential affiliate audience beyond ransomware. This way, they can include malware operators who want their attacks to be even more destructive.
Under BlackCat’s Hood
Figure 3: Crates used for discovery, privilege escalation, parameter reading
BlackCat leverages Rust’s many external modules (called crates) for the bulk of its functionality. As the crates the threat actors chose are established modules, this means they reused rather than wrote their own code.
Rust has seen growing adoption as a malware language of choice over the last few years, as threat actors seek out new ways to thwart traditional antivirus (AV). Rust is a natural choice for any Malware-as-a-Service (MaaS) offering because it allows cross-compilation, which lets affiliates use the same codebase, regardless of the target’s platform of choice.
Conclusion
BlackCat is a complex and highly customizable RaaS that allows threat actors to leverage configurations that can be tailored to their goals, and to specifics of their victims’ environments. As the popularity of alternative programming languages grows, we could see a shift toward malware authors choosing to create threats that allow multi-platform access, and relying less on traditional languages like C/C++.
Mitigation Tips
Many threat groups, including ALPHV, use credentials obtained from access brokers. Some steps you can take to prevent credential-based attacks include the following:
- Frequently change passwords to network systems and accounts, and always avoid reusing passwords for different accounts.
- Frequently audit user accounts with high-level administrative privileges and configure access controls with least privilege in mind.
- Monitor accounts for unusual and unauthorized access that falls outside of the baseline (MITRE D3FEND techniques D3-AZET, D3-LAM).
- Implement multi-factor authentication (MITRE D3FEND technique D3-MFA).
In addition to standard security advice, you can also take the following steps to reduce your exposure to this ransomware threat:
- Token Manipulation (MITRE T1134) – Review users’ token privileges and potentially remove them from the authentication cache (D3-ANCI).
- Bypass UAC (MITRE T1548.002) – Configure stricter User Account Control and file access policies (D3-LFP).
- Put into place a recovery plan to safely maintain multiple copies of sensitive or proprietary information.
References
https://www.varonis.com/blog/blackcat-ransomware
https://www.bleepingcomputer.com/news/security/alphv-blackcat-this-years-most-sophisticated-ransomware/
https://blogs.blackberry.com/en/2022/04/blackcat-ransomware-brings-halloween-horrors-to-world-organizations
https://www.ic3.gov/Media/News/2022/220420.pdf
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you, providing around-the-clock support where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
Related Reading
About The BlackBerry Research and Intelligence Team
The BlackBerry Research and Intelligence team is a highly experienced threat research group specializing in a wide range of cybersecurity disciplines, conducting continuous threat hunting to provide comprehensive insights into emerging threats. We analyze and address various attack vectors, leveraging our deep expertise in the cyberthreat landscape to develop proactive strategies that safeguard against adversaries.
Whether it's identifying new vulnerabilities or staying ahead of sophisticated attack tactics, we are dedicated to securing your digital assets with cutting-edge research and innovative solutions.