WhisperGate Wiper: Watch This Threat Get Silenced by BlackBerry (Video)

Threat actors have used WhisperGate Wiper, a destructive, multi-stage malware, in targeted cyberattacks on Ukraine’s infrastructure. Rather than financial gain, the sole purpose of the malware appears to be the destruction of data. While the observed version of WhisperGate targets Windows® OS, there may be a variant affecting Linux® systems, according to the Ukrainian government. Organizations running either operating system are strongly advised to take preventative measures.
While being primarily destructive in nature, the malware’s design also makes it hard to detect. At the onset of the attack, WhisperGate generates a “red herring” ransom note to camouflage its true purpose. It also intentionally delays the execution of certain functions to stay undetected. Furthermore, it does not force a reboot. It instead waits for victims to reboot their system themselves. And it’s this delayed reboot that gives the malware time to launch additional stages of the attack chain.
BlackBerry classifies WhisperGate Wiper as a potential high impact, but low risk threat to network security
BlackBerry Defeats WhisperGate Wiper
Watch our demo video below to learn more about WhisperGate attacks, and to see how BlackBerry defeats them using our cloud-enabled Endpoint Detection and Response (EDR) solution CylanceOPTICS® in conjunction with CylancePROTECT®, our artificial intelligence (AI) powered Endpoint Protection Platform (EPP).
BlackBerry Cylance
To learn more about Cylance AI capabilities visit: Cylance® AI from BlackBerry
BlackBerry Assistance
The BlackBerry Incident Response team can work with organizations of any size and across any vertical, to evaluate and enhance their endpoint security posture and proactively maintain the security, integrity, and resilience of their network infrastructure. For emergency assistance, please email us at DLIR@blackberry.com, or use our handraiser form.
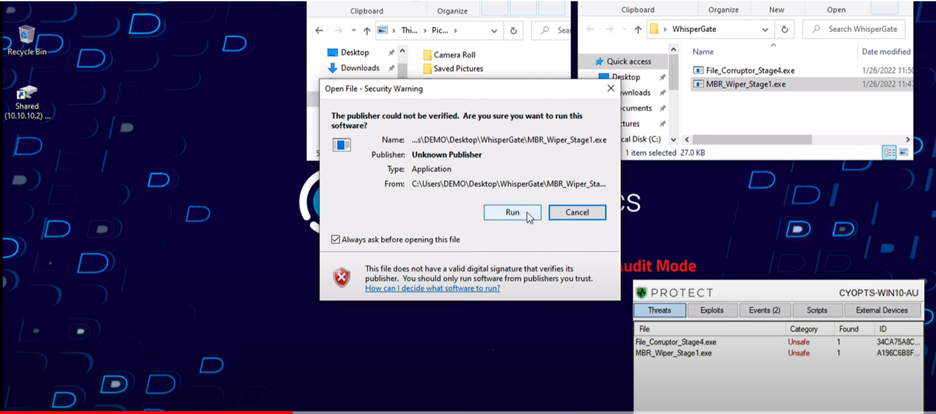
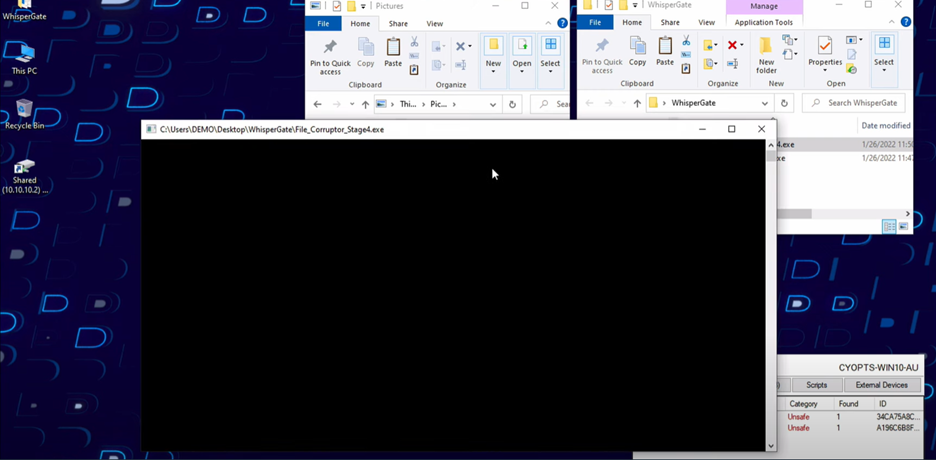
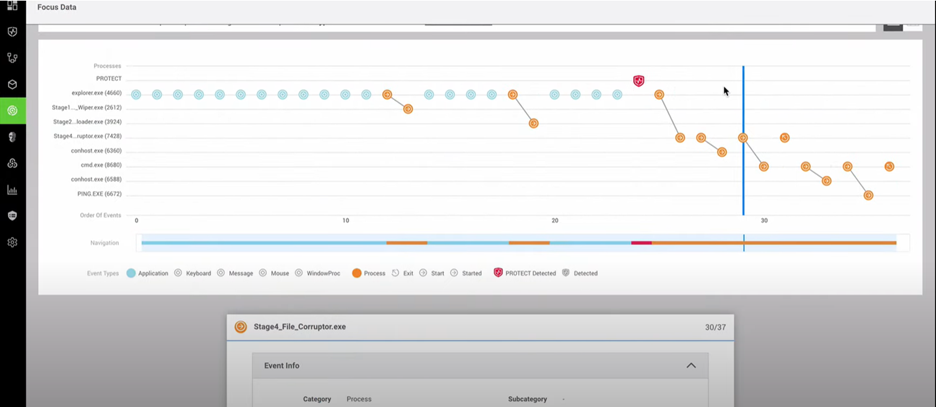
Transcript In this video, we’ll be analyzing WhisperGate, a recent multi-stage wiper attack with the primary objective of data destruction, with no recovery possibilities. Two of its four stages are specifically oriented to data destruction: a master boot record (MBR) wiper and a file corruptor. We configured this system in audit-only mode to allow malware execution. First, the MBR wiper silently replaces the master boot record to prevent access to the system once it is restarted by the user. Then, stage four conducts a general file corruption process, subsequently executing a command to disappear from our system, leaving all our data irrecoverable. When we conduct a root-cause analysis with CylanceOPTICS®, we can visualize the timeline of the steps taken by WhisperGate, including its self-deletion from the system. Now let’s identify if our Temporal Predictive Advantage could have stopped this advanced attack. This is a Cylance® AI model from October 2015, with no internet connectivity or OS updates. As you can see, the attack is prevented in milliseconds, before its execution. Prevention is Possible, with BlackBerry. |

