The Hybrid Digital Workforce: Securing Enterprise Mobile
It’s a recipe for security gaps. Enterprise deployments for secure mobility get complicated in a hurry, particularly when trying to achieve different sets of outcomes.
At the software layer, even before establishing user end goals, directives are issued on enterprise-wide software that delivers basic productivity capabilities like email, document writing and spreadsheets. There is one vendor that has virtually no competition here: Microsoft.
What happens when this productivity software is also what you rely on to secure it? Is the included security “good enough” for your organization? In this blog, the third in a series on securing the hybrid digital workplace, we explore user experience alongside the need to work within a secure digital environment that delivers high levels of data privacy.
Securing the Digital Workforce
During the first blog in this series, The Hybrid Digital Workforce: How to Maximize Security and Productivity, we explored the ubiquitous nature of data and the related challenges. In our second blog, Seamless Integration: BlackBerry Work Enhances Security with Apple, Microsoft we explored the role that practical user experience plays in maintaining peak mobile productivity — while ensuring security is not an afterthought.
Now, let’s get started on part three.
Start Me Up!
When I say Start Me Up! you may remember that the Rolling Stones hit song was a small part of a big Microsoft launch in the 1990s. However, we’re not going to talk about Windows 95 in detail or Steve Ballmer’s on-stage dance routine to the song during that product launch. Although I think it can be argued this period was the start of a new chapter for Microsoft, and one laser-focused on user experience. Outside of early stability and usability issues, user experience improved over time and the related products became ubiquitous.
However, what also increased through subsequent releases was the need for security patches. Patching really started to matter as threats became more sophisticated and these exposed early-on gaps in the Microsoft security stack.
As an example, remember when the BlackBerry device was at its peak in terms of popularity? Microsoft released ‘ActiveSync for mobile’ as a way for receiving email on non-BlackBerry devices. A good tick in the box for user experience and choice, however it was problematic on the security front as both ends of the ActiveSync connection were, in essence, exposed. This was a point of discussion and concern.
Fast forward to 2024 and many gaps still exist, and they’ve been publicly called out by the CEO, who promised a greater focus on fixing security. However, I’m wondering about something: Without requiring more patching and additional security features, how can you build security into already existing products — unless you rebuild them from the ground up?
Better Together Security Approach
Can your organization afford to depend on Microsoft Intune to secure Microsoft products in your environment? Many organizations see this as a cheap or cost-effective approach. However, the TCO (total cost of ownership) of using Microsoft Intune may be challenging over time as you try to fill security gaps which can become both complex and costly.
Consider a recent study on the TCO of Microsoft Intune deployments by Sedulo Inc. Sedulo uncovered what they called the “True Cost of Free,” using real customer examples of why a deployment of Intune isn’t necessarily cost effective.
We’ve seen this movie before, and in this case, the firm detected gaps in data security and privacy and it also highlighted additional gaps in secure connectivity and secure productivity. The report found that third-party tools are needed to fill the gaps, and this leads to unfortunate results.
One example involved a Microsoft Intune customer that deployed Microsoft’s E5 security add-on and Intune suite. Their NPV (net present value) over three years led to a TCO of up to $14.4M in losses. And the organization still had gaps in security, particularly data leakage, which could lead to more unexpected costs in the long run.
According to the analysis, downgrading some Microsoft SKU’s and replacing connectivity solutions with BlackBerry® UEM would have cut that TCO loss nearly in half, saving up to $7.2M over three years, while strengthening security and improving productivity at the same time.
This example reveals that you need a strategy here, but what is it? The answer is simple; if you deploy a solution that is not security-first then you must create a security-first approach by taking a ‘Better Together’ view.
How BlackBerry UEM Works Alongside Microsoft Intune
BlackBerry developed the UEM market some 25 years ago with a security-first approach, and it remains a market leader. BlackBerry UEM’s continued innovation means robust Microsoft interoperability that is superior to other UEM vendors. For example, your employees can view, edit, and share Microsoft office documents securely on mobile (BlackBerry® Bridge), it comes with seamless integration into Microsoft Teams, and it supports necessary capabilities such as Microsoft conditional access and compliance policies.
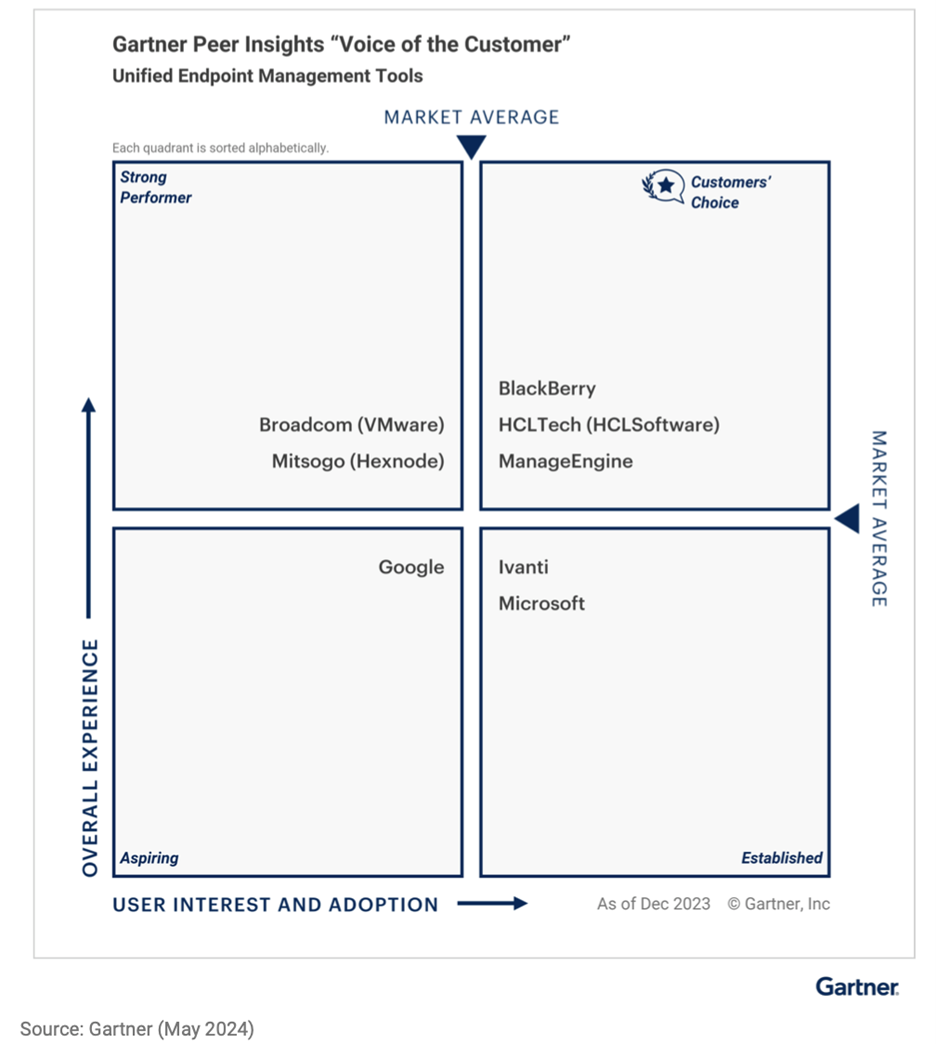
Our security first approach fills in the gaps — while ongoing innovation boosts productivity with Microsoft products at the same time. And yes, BlackBerry UEM allows you to effectively manage all devices — whether they’re running iOS®, Android™, Windows® or IoT operating systems — you’ll find all of them in a unified platform. All these reasons, and more, are why our current customers love using BlackBerry UEM and named BlackBerry a Gartner Peer Insights Customers’ Choice in UEM, two years running.
Conclusion
Unified Endpoint Management (UEM) is not just a tool but it’s also a strategic approach to managing the complexities of the modern digital workplace. Join the world’s leading governments and organizations by implementing BlackBerry UEM, so you can keep your organization both productive and secure. You no longer must choose one or the other.
Reach out and let’s start your journey toward a more secure digital workforce.