Russian Wrecking Crews Go Phishing with Worms and Wipers
Sandworm Strikes Ukraine with “Malware Cocktail”
As the Russian invasion of Ukraine approaches its one-year anniversary, destructive wiper malware is being increasingly adopted as the cyber weapon of choice among Russian and pro-Russia threat actors targeting Ukraine.
The Ukrainian Computer Emergency Response Team (CERT-UA) recently uncovered an attempt to take down Ukraine’s national news agency, Ukrinform. In a Jan. 27 report, CERT-UA reports that the attacker used a “malware cocktail” in the attack, including Windows-wipers CaddyWiper, ZeroWipe, and SDelete, Linux wiper AwlfulShred, and FreeBSD wiper BidSwipe.
The attacker initially snaked its way into the target’s network as early as Dec. 7, 2022, and waited a full month before deploying malware, using a Windows Group Policy (GPO) to launch CaddyWiper. This type of attack timeline — infiltrate then wait — is a common tactic of advanced persistent threat (APT) groups.
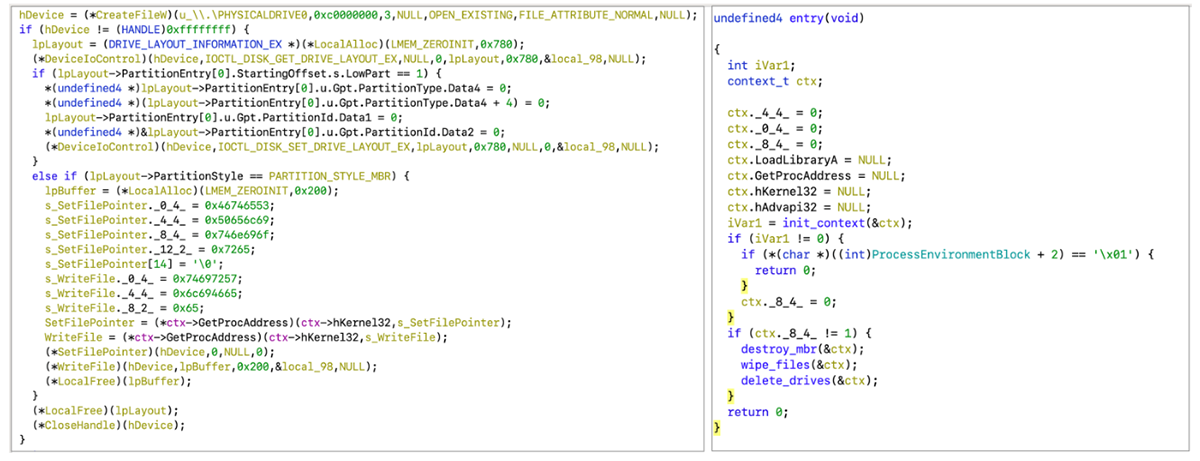
Sample of decompiled software code from CaddyWiper (Source: CERT-UA)
CERT-UA attributed the attack to the Sandworm APT group, which is part of the Russian Military Unit 74455 of the Main Intelligence Directorate. The group has been active since at least 2007, and is also tracked under the monikers Voodoo Bear, Iron Viking, Electrum, and Iridium.
Ultimately, the Ukrinform attack failed, only destroying files on “a couple of data storage systems” rather than wiping all the news agencies’ systems, as was presumably the intention.
This attack is the latest to be chalked up on Sandwom’s “Fail” board, after the group used data-wiper CaddyWiper in a bungled attack on a Ukrainian energy provider last April, which powered high-voltage electrical substations in Ukraine. The station lost power for an hour, but no lasting damage was done.
SwiftSlicer Takes a Byte Out of Ukraine
As the war continues, it can be taken for granted that cyber-disruption will continue to go hand-in-glove with military and political action as a way of targeting entities of Russia’s displeasure. Since the Ukraine invasion began in February 2022, a deluge of data-wiping malware has descended on Ukrainian targets, including DoubleZero, HermeticWiper, IsaacWiper, WhisperKill, WhisperGate, and AcidRain.
Now, researchers at Slovak cybersecurity firm ESET have identified a new wiper in Ukraine that they attribute to the Russian Sandworm APT group. Dubbed SwiftSlicer, the previously undocumented wiper was deployed against an unnamed Ukrainian entity in the public sector on January 25. It works by overwriting crucial files used by the Windows operating system.
"Wipers have not been used widely as they're targeted weapons," Dmitry Bestuzhev, BlackBerry's Most Distinguished Threat Researcher explains, noting that ransomware is still the threat actors’ medium of choice. "Sandworm has been actively working on developing wipers and ransomware families used explicitly for Ukraine."
SwiftSlicer was written in Go (AKA GoLang), an extremely versatile programming language which has since been adopted by many threat actors.
“GoLang is a cross-platform language, which is not simple to reverse,” says Bestuzhev. “That makes it a solid choice when developing cyber-weapons. On one hand, it can be easily used to code for both Windows and Linux environments. On the other hand, when those malware samples end up in the hands of the researchers, it is time-consuming to reverse-engineer them.”
ESET says that SwiftSlicer was launched using Active Directory Group Policy, which lets admins execute scripts and commands throughout all of the devices found in Windows network. As with CaddyWiper, this means that the group had already achieved persistence within the target’s network at the time of the attack.
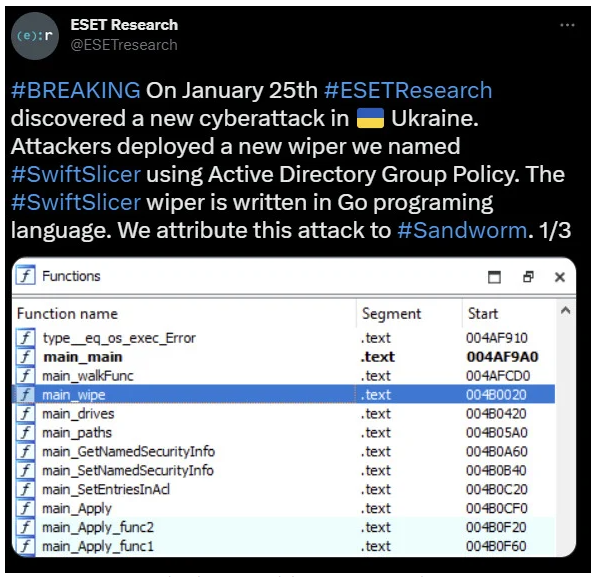
SwiftSlicer’s data-wiping malware functions (Source: ESET)
Sandworm is not the only threat group that has set its sights on Ukraine. According to the State Service of Special Communication and Information Protection (SSSCIP) of Ukraine, since the invasion began last February, Russia has launched over 1,500 cyberattacks against Ukraine.
Between September and December 2022, Ukrainian defenders observed numerous malicious operations coming from Russian and pro-Russian threat actor groups including Sandworm, APT28, APT29, Ghostwriter, COLDRIVER, Xaknet, KillNet, and Gamaredon.
BlackBerry recently took a closer look at Gamaredon in this in-depth report.
NikoWiper Takes Aim at Ukraine’s Energy Sector
Sandworm’s latest ‘release’ is yet another wiper called NikoWiper, which emerged shortly after SwiftSlicer caused damage to Ukrainian-based entities. Researchers at ESET released a report on Jan. 31 stating that Russian threat group Sandworm targeted an unnamed company late last year with data-wiping malware. ESET says:
“We detected the infamous Sandworm group using a previously unknown wiper against an energy sector company in Ukraine. APT groups are usually operated by a nation-state or by state-sponsored actors; the described attack happened in October, in the same period as the Russian armed forces started launching missile strikes targeting energy infrastructure.”
Two months prior in July 2022, Ukrainian energy company DTEK Energy was hit with a cyberattack while Russian military was physically shelling the Kryvorizka thermal power plant owned by the company.
NikoWiper is based on SDelete, a command-line utility tool from Microsoft used to securely delete files. The program is routinely used by network and system administrators. The abuse of SDelete is notable because it suggests that Sandworm may have been conducting experiments with the utility as a wiper in two different instances in its attempts to cause harm to Ukrainian organizations.
Dmitry Bestuzhev, BlackBerry's Most Distinguished Threat Researcher, explains how the NikoWiper malware strain is different from SwiftSlicer:
“NikoWiper relies on a clean and legitimate binary belonging to Microsoft. That technique could be an attempt to 'fly under the radar.’ In other words, it relies on a trusted application to perform data destruction operations. The technique can be effective when the targeted organization doesn’t have enough visibility or isn’t tracking the behaviors of clean or malicious files, capabilities that are often provided by endpoint detection and response solutions. Such executions might be considered a part of the Living Off the Land Binaries and Scripts (LOLBAS) techniques.”
Comparing the two, he continues: “In the case of the SwiftSlicer wiper, it's different. The whole implant is written in the GoLang programming language, and the data destruction is performed on an internal function by rewriting a few bytes in the file, leading to file corruption. So, the infected system stops booting up because of bad files.”
The new wiper underscores the way Russian military forces and cyberattack groups share similar goals. Wipers and other types of malware attacks are expected to escalate amid the ongoing Russian invasion of Ukraine. Sandworm’s less-than illustrious track record also includes a string of attacks using malware such as BlackEnergy, GreyEnergy, and the first iteration of Industroyer to target energy providers. Doubtless the group will soon be worming its way back into the news cycle again soon.
Related Reading