BlackCat ransomware is on the prowl and expanding its attack territory. It has now compromised more than 60 organizations worldwide and this number is likely to grow.
The threat group behind BlackCat, known as ALPHV, recently began offering its malware in the ransomware-as-a-service (RaaS) marketplace, where threat actors can buy subscriptions to the malware and use it to launch their own ransomware campaigns.
This decision to expand BlackCat’s availability beyond ALPHV obscures the group’s presence on any given network or endpoint, while simultaneously growing its reputation and revenue. When other cybercriminals — the subscribers — use BlackCat RaaS, it becomes difficult to determine whether a detected attack is directly attributable to ALPHV. Additionally, third-party threat actors who utilize BlackCat as a service contribute as an extra source of profit to the malware authors.
BlackCat shares proximity with the BlackMatter and DarkSide groups, who famously breached U.S. energy distributor Colonial Pipeline in May 2021, causing widespread gasoline shortages and price increases. Many malware developers behind that attack support BlackCat, as well.
The RaaS version of this threat is based on the Rust programming language, which allows the threat operator to maintain a single code base that can be used on various operating systems. BlackCat is also highly versatile and can be used as ransomware or wiper malware, based on different execution paths. The tool can simultaneously exfiltrate and encrypt files for ransom in so-called “double extortion” attacks.
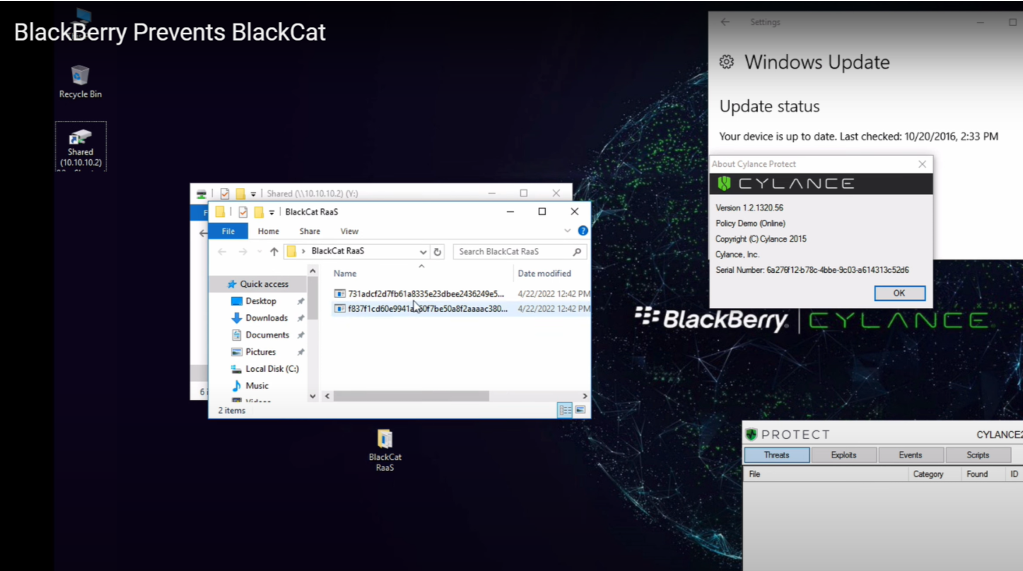
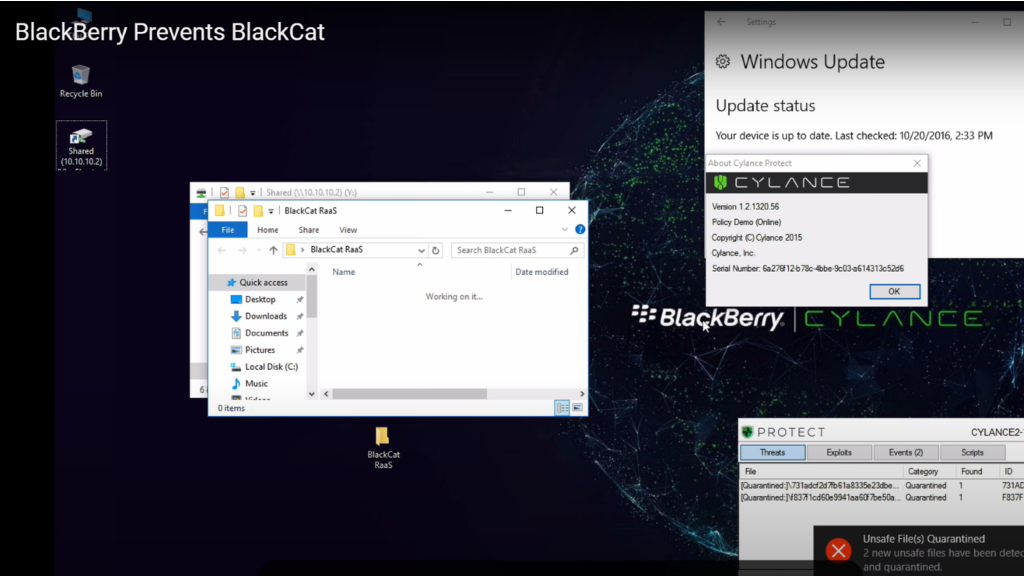
See how BlackBerry prevents BlackCat attacks in our demo video below, which shows CylancePROTECT® going head-to-head with a live sample of BlackCat ransomware.